Configure SAML with Azure Active Directory as identity provider
-
Microsoft has changed the name of Azure Active Directory to Microsoft Entra ID. However, some sections of Nintex Workflow and the help still refer to this product as Azure Active Directory.
-
For details about configuring SAML using Entra ID, see Configure SAML with Entra ID as identity provider.
![]() An administrator role is required. For information, see User roles.
An administrator role is required. For information, see User roles.
Before you begin, read Configure single sign-on using SAML protocol.
Jump to:
-
Configuration steps:
1. Verify your domain in your Nintex Workflow tenant
2. Get the Identity Provider data from Nintex Workflow
3. Create a Nintex Workflow application in Azure Active Directory
This step has two options for configuring the Email address attribute:
4. Copy the SAML metadata from Azure Active Directory to Nintex Workflow
1. Verify your domain in your Nintex Workflow tenant |
- Sign in to Nintex Workflow using an email address with administrator privileges.
-
Go to Settings > Tenant.
-
Click User management.
Note: Go to Settings > Tenant. The tenant and user details page opens. To return to the main menu, click
 next to the Nintex logo.
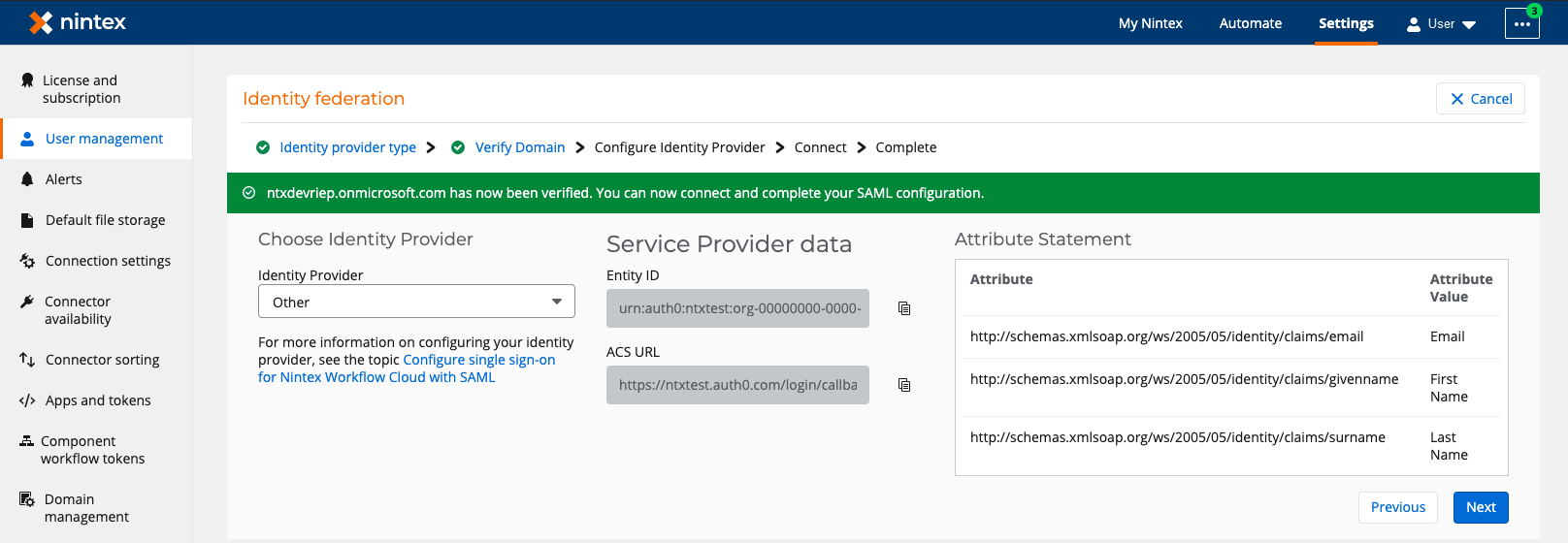
next to the Nintex logo. - In the Identity federation section, click Configure.
- Verify your domain by using the verification code and adding a DNS record. For complete steps on verifying your domain, see Verify a domain for SAML configuration.
Tip: The initial page in the setup wizard includes a warning message that lists the Nintex Workflow tenants associated with the tenant you're going to configure with SAML. Click View more to see the list of tenants.
Caution: As part of the prerequisites to federation configuration, you must first verify ownership over a domain that you're going to use for SAML configuration. If you have not verified your domain, or if your DNS is still processing the verification, you can continue configuring SAML in Nintex Workflow, but you cannot submit your SAML configuration.
2. Get the Identity Provider data from Nintex Workflow |
Note: Make sure your domain is verified and service provider details are updated. For more information about updating service provider details, see Upgrade identity federation.
- In the Verify Domain page of the setup wizard in Nintex Workflow, click Next.
- In the Configure Identity Provider page, select Other as the identity provider.
- Keep your Nintex Workflow browser open and go to Azure Active Directory.
Additional fields appear for the following:
Note: You will later need to copy and insert these values in specific fields in Azure Active Directory.
For detailed information on each field that appears on the setup wizard, see Identity federation setup wizard elements and description.
3. Create a Nintex Workflow application in Azure Active Directory |
Note: Prepare the Service Provider data (Entity ID and ACS URL) and Attribute Statement values (First Name, Last Name, and Email), which you noted in the previous step. You will need to copy the data and paste them into specific fields in Azure Active Directory.
-
Sign in to the Azure portal as an administrator and navigate to the Azure Active Directory service.
-
Create a new enterprise application.
-
On the left, navigate to the Manage section, and then click Enterprise applications.
-
Click New application > Create your own application.
-
Type the name of the application.
-
From the list of reasons for creating the application, select Integrate any other application you don't find in the gallery.
-
Click Create.
-
-
Configure the application settings.
-
On the left, navigate to the Manage section, and then click Properties.
-
Switch the User assignment required toggle to No.
Note:-
We recommend clicking No so that any user in Azure Active Directory is able to authenticate as participants in Nintex Workflow.
-
If you click Yes, the Azure Active Directory Admin needs to assign users to the SAML application before users can access Nintex Workflow.
-
-
Switch the Visible to users toggle to No.
-
Click Save.
-
-
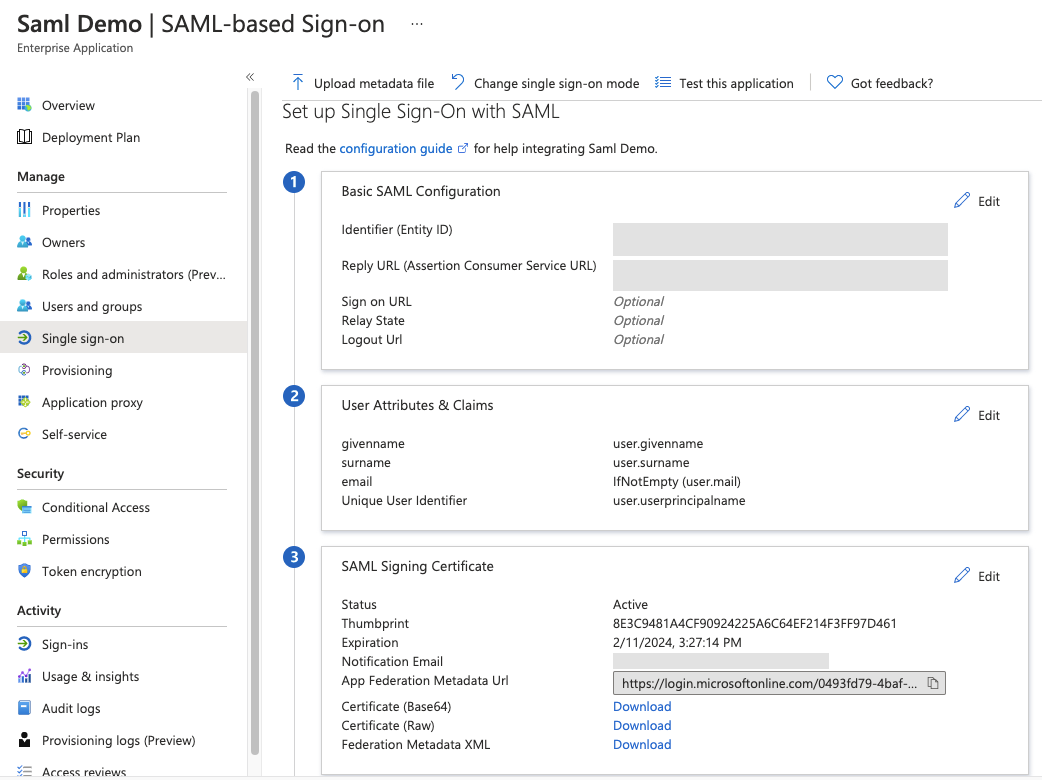
Open the Set up Single Sign-on with SAML page to configure the single sign-on settings.
-
Enter the Service Provider data from Nintex Workflow.
-
In the Basic SAML Configuration section, click Edit.
-
In the Identifier (Entity ID) field, paste the Entity ID that you copied from Nintex Workflow.
-
In the Reply URL (Assertion Consumer Service URL) field, paste the ACS URL that you copied from Nintex Workflow.
-
Click Save.
-
Click Close.
-
-
Map the Surname and Givenname identity attributes.
-
In the User Attributes & Claims section, click Edit.
-
Add or edit a claim for Surname and Givenname.
-
In the Name field, paste the attribute values that you copied from Nintex Workflow.
-
For Surname, paste the Last Name attribute.
-
For Given name, paste the First Name attribute.
-
-
For Source, select Attribute.
-
In the Source attribute field, select one of the following:
-
For Surname, select user.surname.
-
For Given name, select user.givenname.
-
-
Save the changes.
-
-
Map the Emailaddress identity attribute by performing one of the following configurations:
If your Nintex Workflow tenant will have guest user accounts, follow the steps for Guest user-enabled configuration. Otherwise, follow the steps for normal configuration.
-
Normal configuration
-
In the User Attributes & Claims section, click Edit.
-
Add or edit a claim for Emailaddress.
-
In the Emailaddress field, paste the Email attribute that you copied from Nintex Workflow.
-
Set the Source to Attribute.
-
In the Source attribute field, select user.mail.
-
For each user account, the source attribute value, which is mapped from Azure Active Directory must contain a valid and real email address.
-
Alternatively, you can also use a User Principal Name (UPN) as long as it contains a real email address. To use a UPN, select user.principalname. The UPN and email address do not need to be the same.
-
Save the changes.
Note: -
-
Guest user-enabled configuration
Important:-
Users with guest accounts can sign in to Nintex Workflow only if Auto-acceleration is turned on. For more information, see User management.
-
One-time password (OTP) is not supported for guest users.
-
Guest users cannot be promoted to a global administrator role.
-
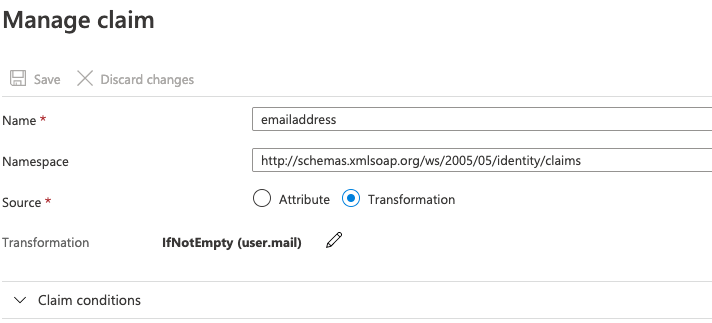
In the User Attributes & Claims section, click Edit.
-
Add or edit a claim for Emailaddress.
The Manage claim page appears.
-
In the Name field, paste the Email attribute that you copied from Nintex Workflow.
-
Set the Source to Transformation.
-
In the Transformation field, click Edit.
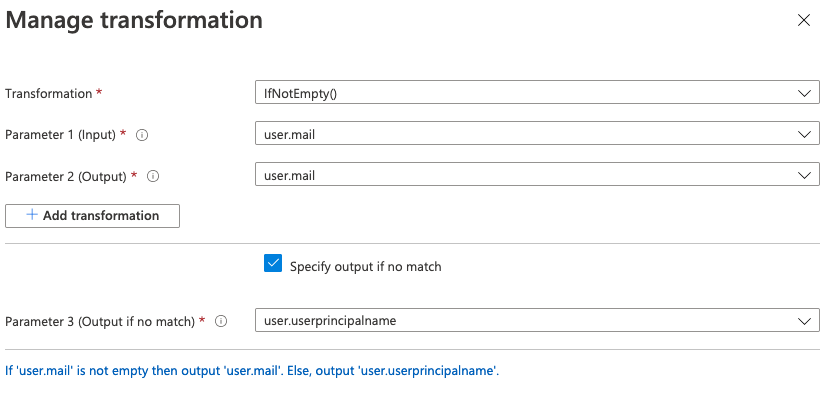
The Manage transformation panel appears.
-
In the Transformation field, select IfNotEmpty().
-
In the Parameter 1 (Input) field, select user.mail.
-
In the Parameter 2 (Output) field, select user.mail.
-
Select Specify output if no match.
-
In the Parameter 3 (Output if no match) field, select user.principalname.
-
Save the changes.
-
Caution: After adding Nintex Workflow as a SAML application to Azure Active Directory, make sure that users exist in Azure Active Directory. Depending on the identity provider, an empty directory may cause SAML configuration to fail. For information on how to manage user accounts, refer to Azure Active Directory's help documentation.
-
-
In the Signing Certificate section, copy the SAML Metadata URL or download the file, depending on what you want to use in the Nintex Workflow setup wizard.
-
In the App Federation Metadata Url field, click the Copy icon.
-
In the Federation Metadata XML field, click Download.
In the next step, you will need to copy the URL or attach the file in specific fields in Nintex Workflow.
For more information on the SAML configuration steps in Azure Active Directory, see Configure SAML-based single sign-on.
-
4. Copy the SAML metadata from Azure Active Directory to Nintex Workflow |
Prepare the App Federation Metadata Url or Federation Metadata XML, which you copied or downloaded in the previous step.
Follow these steps to complete the SAML configuration:
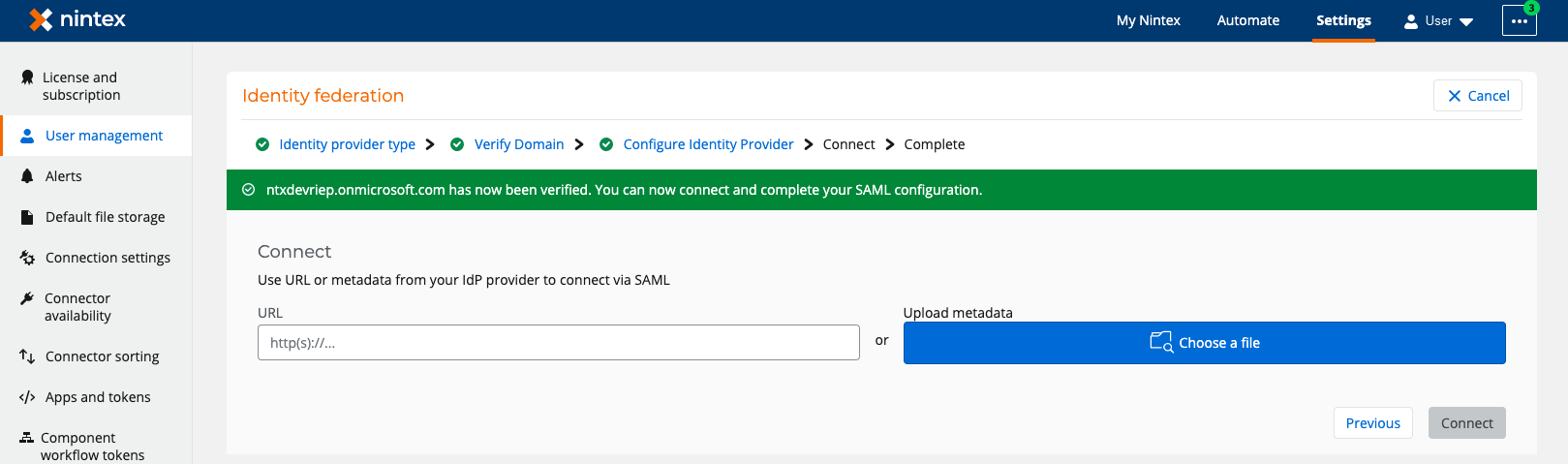
- In the Configure Identity Provider page of the setup wizard in Nintex Workflow, click Next.
- In the Connect page,:
- Click Connect.
- To copy the One-time password URL, click
 (Copy) next to the One-time password URL field.
(Copy) next to the One-time password URL field. - Open a new tab on your web browser, paste the copied URL and press ENTER.
- Enter your email address, and click Submit.
- Enter the one-time password you received, and click Sign in.
- Click Done.
Note: The Connect button is enabled only when your domain is successfully verified AND you have provided the metadata URL or file.
After connecting, your SAML configurations are checked. If successful, the setup wizard goes to the final page with the following information:
| Information | Description |
|---|---|
| Expiry date of certificate | Date when your certificate expires. |
| Recipient email address of the reminder for certificate expiry |
Email address to which a reminder email is sent when the certificate is close to expiring. Caution: You must renew the certificate before the expiry date. |
| One-Time Password (OTP) URL |
The One-Time Password (OTP) URL is used for troubleshooting purposes when configuration fails and you are locked out of your tenant. Follow these steps to access your tenant when you cannot sign in due to a failed configuration of SAML: For verification, a one-time password is sent to your email address. The one-time password expires after five minutes. You can access your Nintex Workflow tenant and resume configuring your identity federation. |
The Identity federation section now lists information about your SAML configuration such as provider, domain, person who completed the configuration, and the date of configuration.
5. Test your SAML connection |
- Sign in to your Nintex Workflow tenant.
- Click Sign in or press ENTER.
- In Azure Active Directory's login page, type your credentials, and then submit.
You are taken to the login page of Azure Active Directory.
If the SAML configuration is successful, you are granted access to the Nintex Workflow tenant.
| Page | Section | User interface element |
Description |
||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Identity provider type | Warning message |
A warning message appears, listing the tenants that are associated with your tenant. Enabling single sign-on in your tenant will also enable single sign-on in associated Nintex Workflow tenants. For example, both sales-myorg.workflowcloud.com and hr-myorg.workflowcloud.com will be enabled with single sign-on if you configure SAML in either of them. |
|||||||||||||||||||||||||||||||||||
|
Select single sign-on (SSO) type |
Select the means to enable SSO in your Nintex Workflow tenant.
|
||||||||||||||||||||||||||||||||||||
| Verify Domain (This page displays only when you select SAML for Single sign-on (SSO) type) |
DNS record |
The code to use as a value in your DNS record. For the domain verification steps, see Verify a domain for SAML configuration. Caution: As part of the prerequisites to federation configuration, you must first verify ownership over a domain that you're going to use for SAML configuration. If you have not verified your domain, or if your DNS is still processing the verification, you can continue configuring SAML in Nintex Workflow, but you cannot submit your SAML configuration. |
|||||||||||||||||||||||||||||||||||
 (Copy) (Copy) |
Click to copy the code. | ||||||||||||||||||||||||||||||||||||
| Configure Identity Provider (This page displays only when you select SAML for Single sign-on (SSO) type) |
Choose Identity Provider | Identity provider |
Displays the list of identity providers you can use for your tenant's identity federation. |
||||||||||||||||||||||||||||||||||
| Service Provider data |
|
(Appears after you select an identity provider) In the context of our SAML configuration, the service provider is Nintex Workflow. Depending on the identity provider you choose, the SAML terminologies displayed in this section correspond with what your identity provider uses.
|
|||||||||||||||||||||||||||||||||||
|
Attributes |
Set of identity data about a user. In configuring SAML in Nintex Workflow, only three attributes are requested from the identity provider:
|
||||||||||||||||||||||||||||||||||||
 (Copy) (Copy) |
Click to copy the values in the fields. | ||||||||||||||||||||||||||||||||||||
| Connect (This page displays only when you select SAML for Single sign-on (SSO) type) |
URL |
Location of the SAML metadata An XML document that contains information about a SAML deployment.. |
|||||||||||||||||||||||||||||||||||
| Upload metadata | The SAML metadata file. | ||||||||||||||||||||||||||||||||||||
| Complete |
<Date> |
(Only displayed for SAML) Expiry date of the certificate. |
|||||||||||||||||||||||||||||||||||
| <Email address> |
(Only displayed for SAML) Email address to receive reminder when certificate is soon to expire. |
||||||||||||||||||||||||||||||||||||
| One-Time Password (OTP) URL | <URL> |
The One-Time Password (OTP) URL is used for troubleshooting purposes when configuration fails and you are locked out of your tenant. Follow these steps to access your tenant when you cannot sign in due to a failed configuration of SAML:
For verification, a one-time password is sent to your email address. The one-time password expires after five minutes. You can access your Nintex Workflow tenant and resume configuring your identity federation. |
|||||||||||||||||||||||||||||||||||