SharePoint Issues
This section covers common issues you may encounter with SharePoint integration, as well as recommended resolutions.
Issue:
This error occurs when interacting with the K2 for SharePoint App, re-registering the K2 for SharePoint App, refreshing groups or applying the K2 for SharePoint App to a SharePoint list or library. This is caused by the timer job not running or attempts to run but fails. Running the App Deployment Health Check will also reveal the cause of the issue.
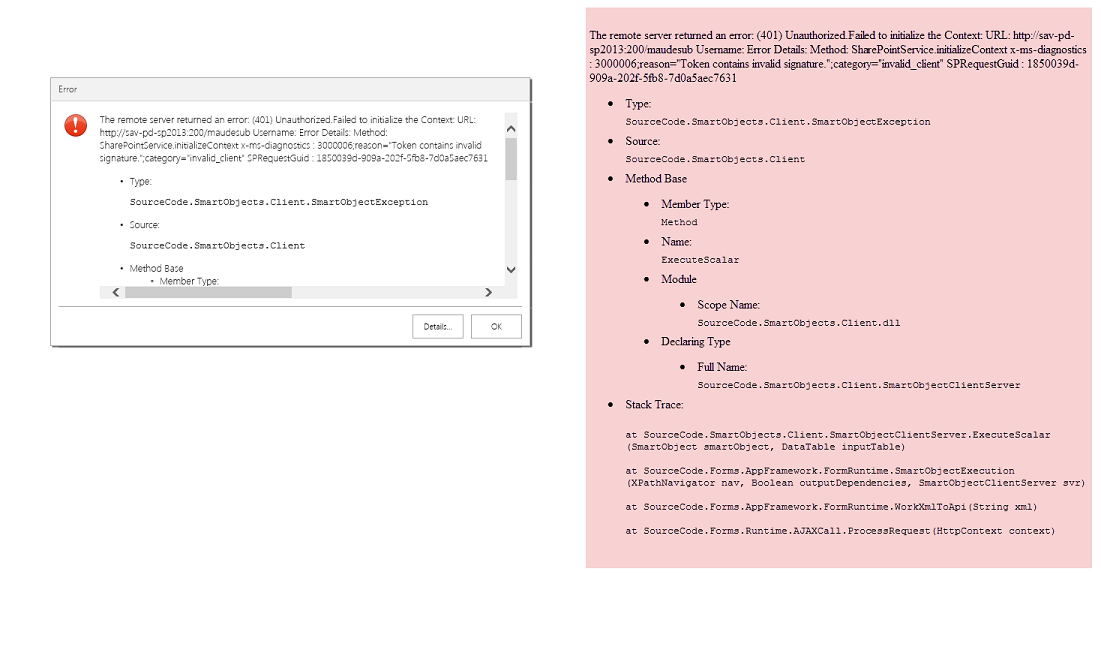
Resolution:
To resolve the issue follow the steps below:
- Navigate to Central Administration > System Settings > Manage services on server.
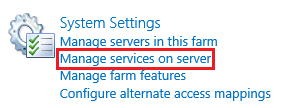
- Restart the User Profile Service.
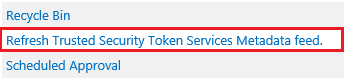
- Navigate to Central Administration > Monitoring > Review Job Definitions.
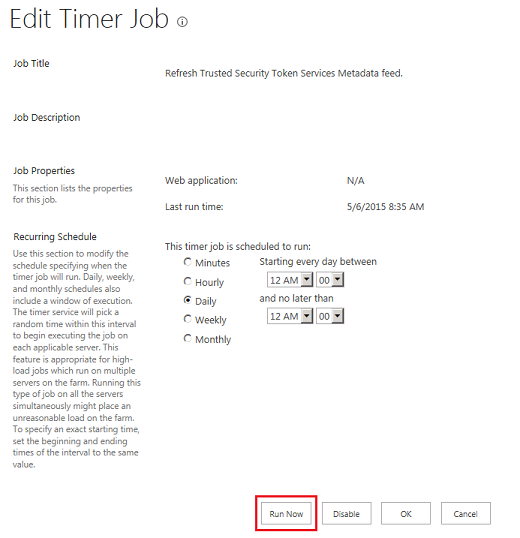
- In Job Definitions, find the Refresh Trusted Security Token Services Metadata feed job definition.
- Select it and the Edit Timer Job screen will open.
- On this page select the Run Now button.
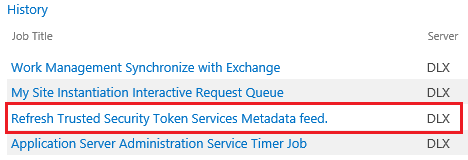
- To ensure no errors persisted, go to Timer Job Status.
- Here the job should be running or it should be completed successfully under the history section.
- The error will have been resolved.
Issue:
An issue exists where any URL not ending in a postfix (e.g. ".aspx") is not routed to the default asp.net handler by IIS 7.0 or 7.5, resulting in a 404 error.
Resolution:
After applying this hotfix - http://support.microsoft.com/kb/980368 and restarting the server, the issue is resolved.
Issue:
When registering the K2 for SharePoint App on OneDrive sites in Office 365, the following error may occur:
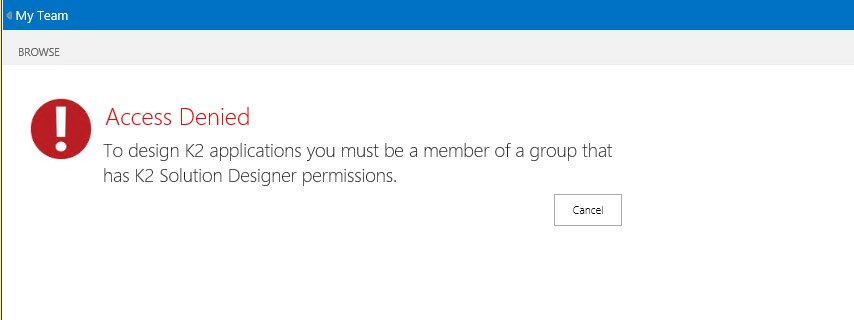
This error is caused by existing or new groups on OneDrive site not automatically given K2 Solution Designers and K2 Solution Participants permissions. OneDrive does not have a Members or Owners group and these are the groups that K2 automatically assigns the above permissions to for work with K2. The app cannot be used and the following error occurs:
Access Denied: To design K2 applications you must be a member of a group that has K2 Solution Designer permissions.
Follow the steps below to add groups to the site and assign the correct permissions.
Resolution:
- Log in with an Administrator account on Office365 and go to the OneDrive site.
- Navigate to the Site Permissions section of the OneDrive site administration.
- Add or Edit a group and assign rights to the group.
- Go to the K2 for SharePoint App Settings page and under the Administration section click Configure K2 Permissions.

- Assign the group K2 Solution Designers and K2 Participants Solutions permissions and click OK. See the K2 Application Rights topic for information on the required permissions to install and use the K2 for SharePoint App.

Issue:
An Access Denied error occurs when you deploy a workflow to SharePoint Online that uses SharePoint events, such as An item was added and An item was deleted.
Example Error Message:
The "SourceCode.SharePoint15.DeploymentTask.Task" task failed unexpectedly.
System.Exception: Service: SharePointIntegration
Service Guid: 71810da1-81e2-4f22-8cf2-4011dacfdf42
Severity: Error
Error Message: Thread 1: Access denied. You do not have permission to perform this action or access this resource.
Resolution:
To resolve the issue, follow these steps :
- Open K2 Management and browse to the Authentication > OAuth > Tokens node. Find and delete the SharePoint token for the K2 service account.
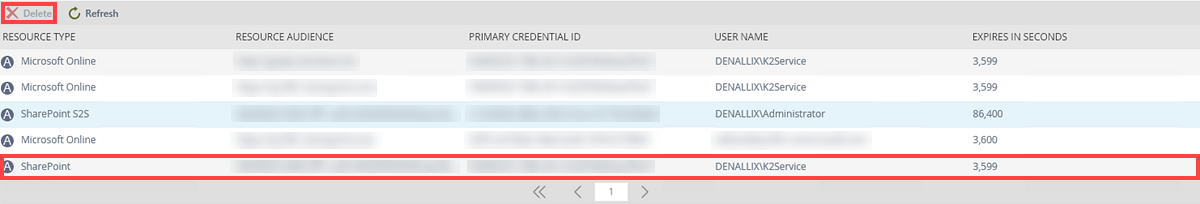
- From the app catalog, reactivate the site collection.
Issue:
An error occurs when the "Trust It" button is clicked when adding the K2 App to the site. The error occurs when the app is installed with the system account, the SharePoint log file will show the error message that the system account does not have permissions to perform the action.
Resolution:
Add the K2 App using an account other than the system account that has site collection rights and read rights in the app catalog site.
For more information see: the MSDN article Add apps for SharePoint to a SharePoint 2013 site.
Issue:
When connecting to Central Administration from a client machine for instance Activate All K2 Features and K2 Configuration Settings you may run into an Authentication is required for session xxx error caused by the double authentication hop. This means that the Kerberos configuration was not configured correctly. Check the following:
Resolution:
- For IIS 7 or IIS 7.5 Only: Add this attribute useAppPoolCredentials in the ApplicationHost.config file. (For more information, open the Microsoft article on Service Principal Name (SPN) checklist, then navigate to the Special case of running IIS 7.0 in a WEB FARM section).
-
Add HTTP SPN for Central Admin application pool account – for NetBIOS and FQDN.
- In Active Directory:
- Configure the Administration Server computer account to Trust this computer for delegation to any service (Kerberos only).
- Configure the Central Administration application pool account to Trust this computer for delegation to any service (Kerberos only)
- Make sure that the K2 server service SPN is configured correctly. (This should have been completed during the K2 installation if the option was selected.)
Ensure that the administration and timer services are running on ALL SharePoint servers (AppServer + WFE's)
- The timer service account should be setup as the same account as which the Central Administration application pool is running.
- The administration service account should be set as LocalSystem.
See the following diagram as quick reference guide: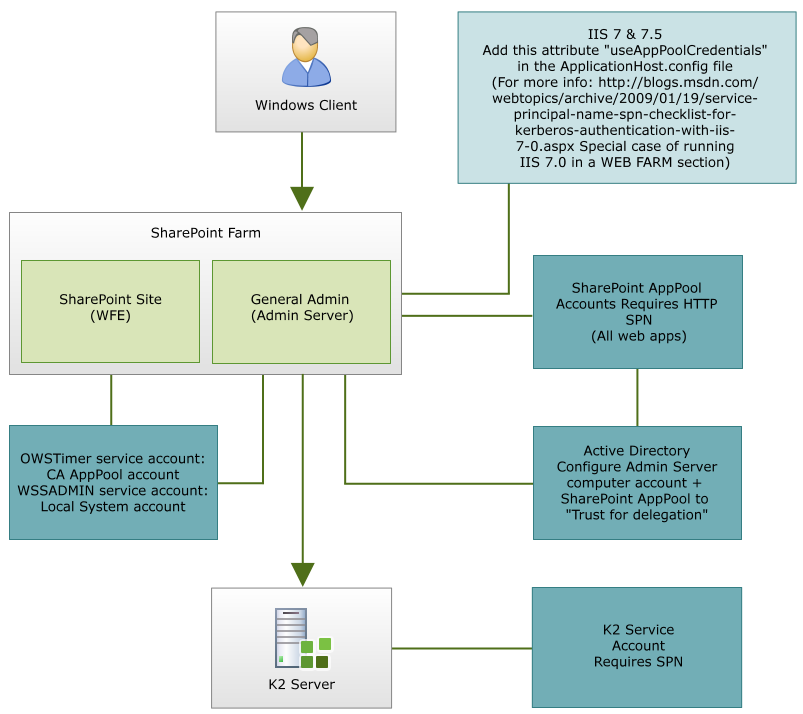
Issue:
The error below is surfaced in the K2 for SharePoint server component as a result of incorrectly configuring MSDTC:
3832","2014-01-30 02:09:18","Error","15","15002","ERROR","SourceCode.Configuration.SharePoint15.Config","15002 Deployment Error: One or more items was not found","anonymous","0.0.0.0","k2:C:\Install\K2 for SharePoint RC Installers\K2 for SharePoint RC (4.13350.0.0)\Installation","3832","9791699e7ec9484893efd324d0a42f6d",""
Resolution:
If K2 for SharePoint is deployed into a fully distributed environment, MSDTC needs to be correctly configured on the K2 server and the SQL servers as per K2 blackpearl Installation and Configuration Guide.
Issue:
Unable to trigger workflows from SharePoint events and the error below is encountered when trying to browse to the RemoteEventService.svc.
|
“HTTP Error 404.17 – Not Found |
|---|
This error occurs because the HTTP activation feature of Windows Server 2012 is not installed so that IIS 8 cannot handle .svc extensions.
Resolution:
Browse to Start > Administrative Tools > Server Manager then to Features and select Add Features to add the HTTP activation.
Issue:
When completely removing the K2 for SharePoint app from the App Catalog and then uploading and adding the K2 for SharePoint app again, navigating to a K2 artifact page results in an HTTP 500 error.
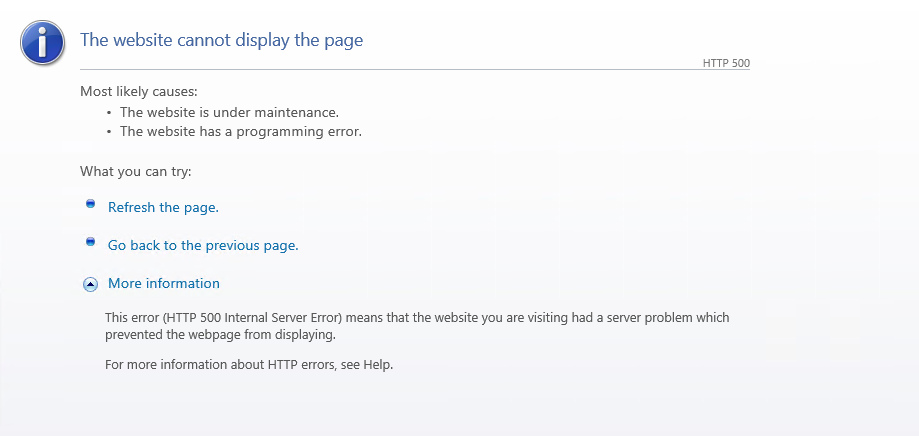
Resolution:
To resolve the issue, follow the steps below:
- Navigate to App Catalog > Site Contents and click on the K2 blackpearl for SharePoint app.
- On the App Catalog > K2 for SharePoint page, click the Manage App Deployments (SharePoint) link in the Administration section.
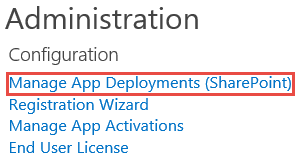
- On the Manage App Deployments page, deploy the K2 blackpearl for SharePoint app to a specific site collection or by the Managed Paths option (recommended), and click OK.
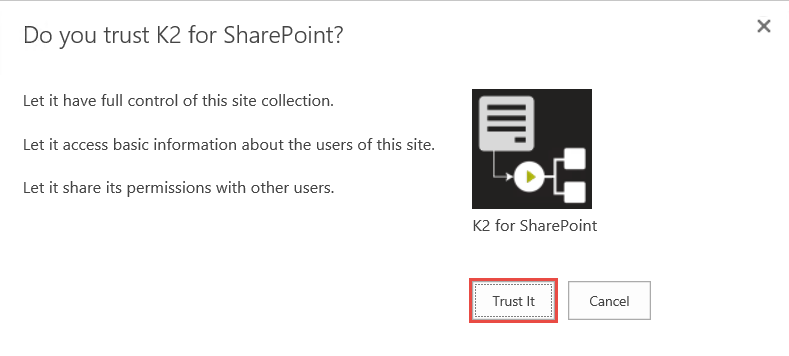
- Click Trust It on the Do you trust K2 for SharePoint page.
- On the Site Contents page, click the K2 blackpearl for SharePoint app.
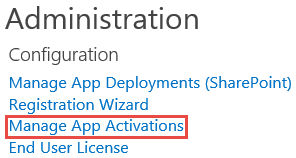
- On the App Catalog > K2 for SharePoint page, click the Manage App Activations link.
- On the Manage App Activations page, specify the site collection URLand click Activate.
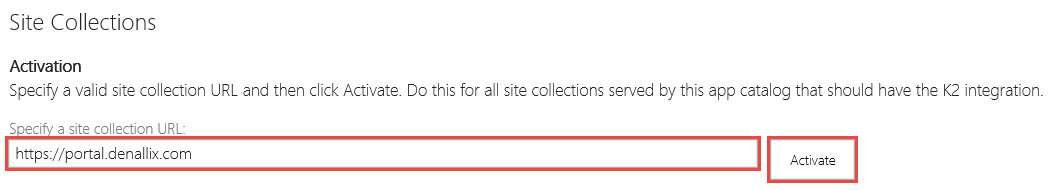
- On the Activate Site Collection page, the Activations Status will say Activated for all sites in the site collection. Click Activate All to reactivate the K2 for SharePoint app to all sites in the site collection. After activation is completed, click Close.
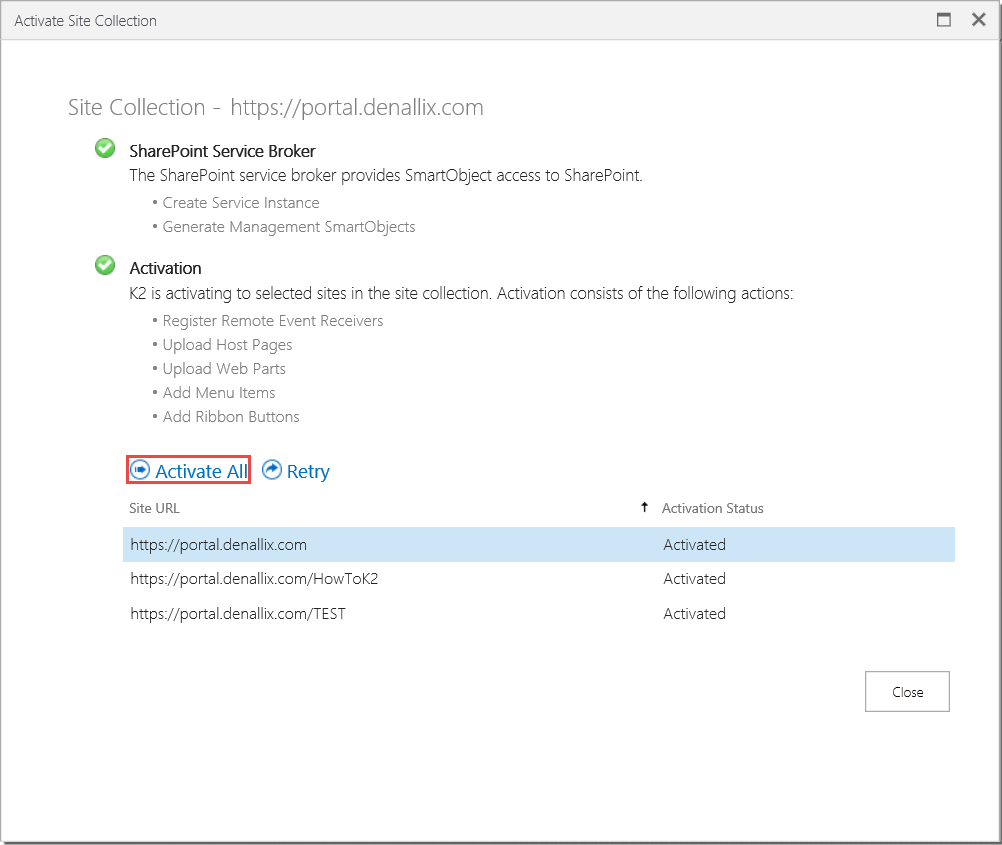
- Navigate to a K2 blackpearl for SharePoint integrated list or library, click the List or Library tab in the SharePoint ribbon and click the Application option.
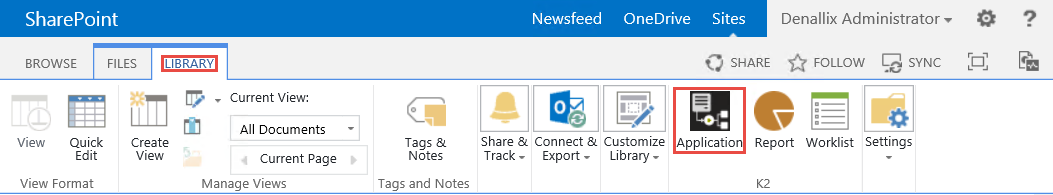
- The HTTP 500 is no longer displayed and the K2 artifact page shows.
Issue:
Internet Explorer 11 could have various issues with CRM, SharePoint and K2.
Resolution:
The best way to avoid these issues is to add all SharePoint, K2 and CRM sites to the Compatibility View list in IE 11.
Issue:
Clicking the K2 application in SharePoint a "Let us know why you need access to this site." message is displayed.
The issue appears if you don't have read permissions on the app catalog.
Resolution:
Ask your administrator to provide Read Permissions to all users/group needed to access to the K2 Application.
Issue:
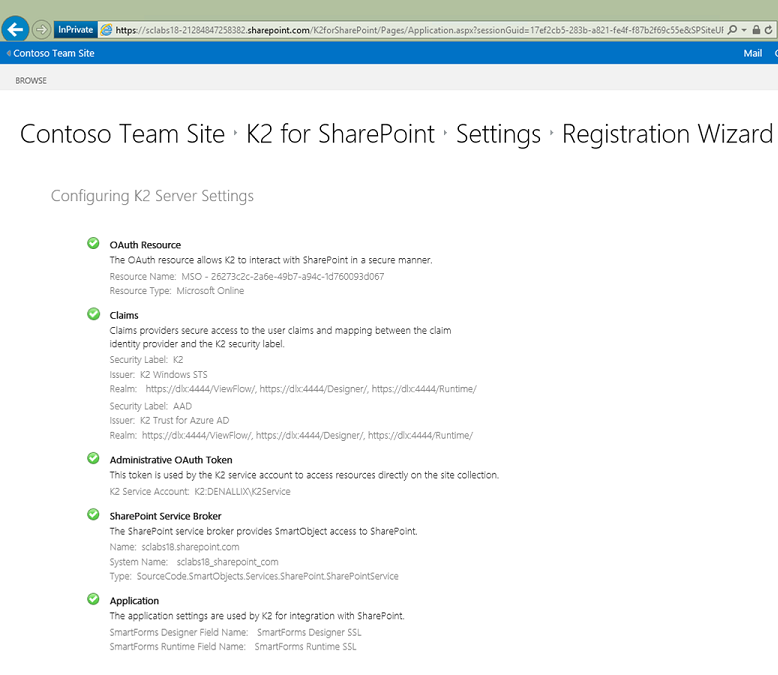
When registering the K2 for SharePoint App on a root site collection or a root site collection that was created by a non-admin user within an O365 environment, the Self Service Site Creation (SSSC) feature may cause failures during the registration wizard of the K2 for SharePoint App.
Resolution:
To resolve this issue follow the steps below:
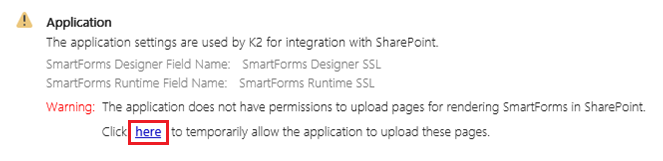
- When running the registration wizard, under the Application section, a warning is displayed.
- Click the link to temporarily allow the application to upload pages.
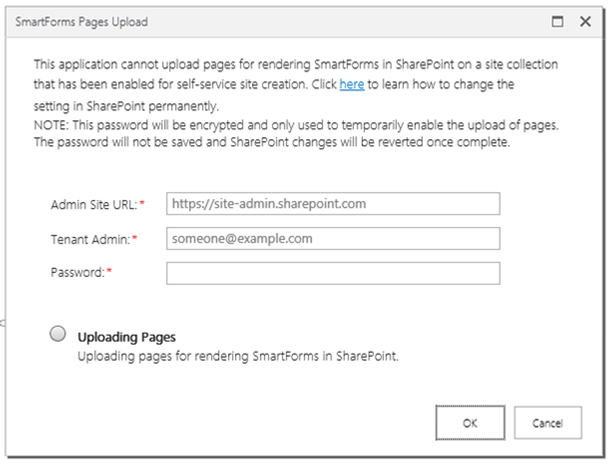
- Next the SmartForms Pages Upload screen will appear.
- Enter the Office 365 tenant administrator's credentials in the requested fields:
- Admin Site URL: This is the administration site URL for the SharePoint Online Environment, for example:
https://site-admin.sharepoint.com
- Tenant Admin: This is the tenant administrator's user name, for example:
someone@onmicrosoft.com
- Password: This is the tenant administrator's password.
- Admin Site URL: This is the administration site URL for the SharePoint Online Environment, for example:
- Clicking OK temporarily disables the SSSC feature and uploads the required pages. Once complete, the SSSC feature is re-enabled and a green tick is displayed:
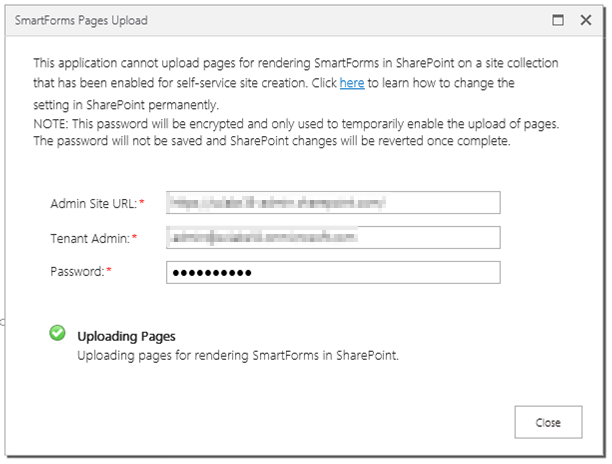
- Click Close and the registration wizard completes.
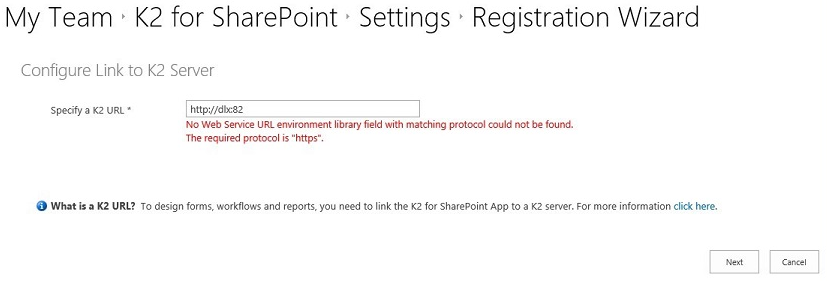
Issue:
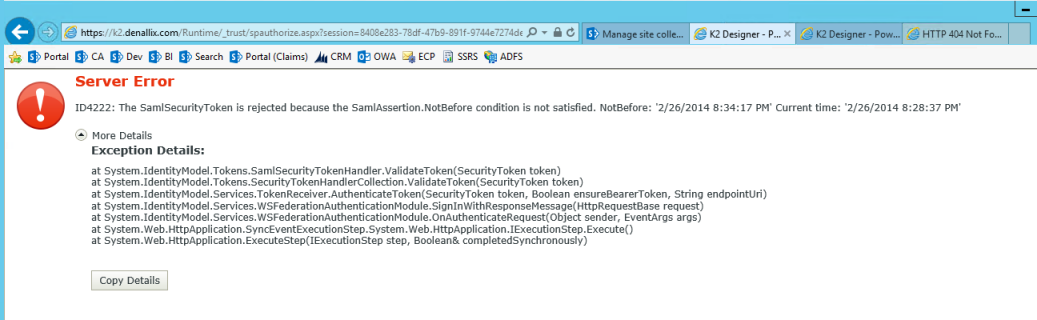
The app registration might fail with a SAML error similar to the image below:
Resolution:
Make sure the system clocks of the servers involved are set to the same time. Claims requires that tokens be passed between systems within a 5 minute window.
Issue:
At times in K2 for SharePoint, an IFrame pops up requesting a login method. After selecting a login method, you end up going through the login loop, always ending up back on the login page.
Resolution:
This issue is handled in a KB article: KB001556 Security Token Issues with IFrames and Cookies in Internet Explorer
Issue:
After converting from Windows Authentication to Claims Authentication in SharePoint 2010, an error is raised if there is a custom web part on the homepage.
Resolution:
See the article on adding the SharePoint Security Token Service for information on setting up SharePoint STS which will resolve this error.
Issue:
If this error is surfaced, the K2 services may be incorrectly configured.
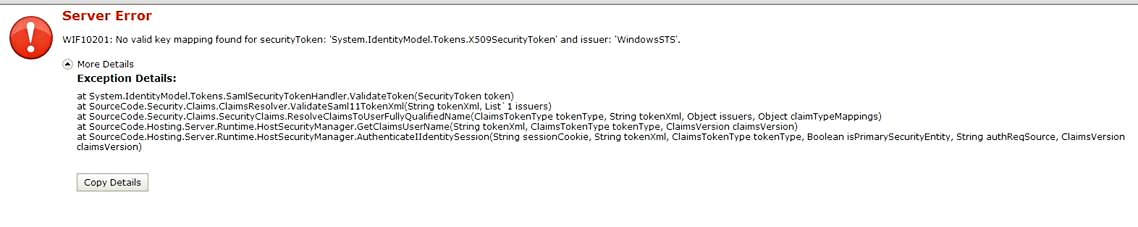
Resolution:
See the KB article KB001435 K2 4.6.7: Multiple binding configuration for K2 Services may overwrite settings on upgrade.
Issue:
You are not able to see the "Application K2" button in the Ribbon bar in SharePoint.
Resolution:
You need to be a member of the Solution Designers group (Site Contents > K2 blackpearl for SharePoint > Configure K2 Permissions) or the group you are a member of, needs Edit permissions (Site Settings > Site Permissions).
Once the changes have been applied, you must Synchronize Groups
Issue:
When installing and working with the K2 for SharePoint components, you must provide credentials for several different accounts. Using the incorrect account may result in errors while using those components. The following links describe the accounts that are used to install, configure, and run the various K2 for SharePoint components:
Resolution:
Consider the following example. User A is a farm administrator and has been set as the destination user. User B is a farm administrator and has been set as the SharePoint application pool account of the current web application. When user A logs in and opens his task, he receives an error because the program does not consider him to be the destination user, instead it expects user B to be the destination user.
Problem:
The problem in this case is because the user logging in to Workspace is the SharePoint\system or the application pool account, which SharePoint logs in as SharePoint\system account automatically. Because both accounts will display as system accounts, SharePoint cannot tell the difference.
Solution:
Do not use an actual user account as the application pool account. However, a workaround is available in the event where this cannot be prevented.
Use the stsadm command line utility that ships with SharePoint to run the command stsadm -o updatefarmcredentials -identitytype NetworkService.
This will change the identity type to NetworkService Service Account. The application pool account will stay the same.
Issue:
When registering the K2 for SharePoint App in a SharePoint online (O365) environment, if there are no environment library fields with matching protocols for the SmartForms Runtime URL, SmartForms Designer URL and Web Service URL present, the following errors will be displayed:
SmartForms Runtime URL: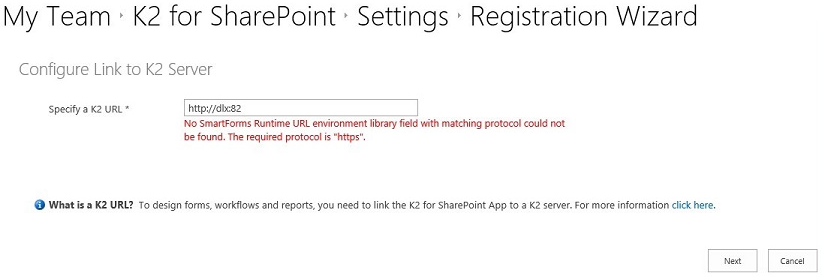
SmartForms Designer URL: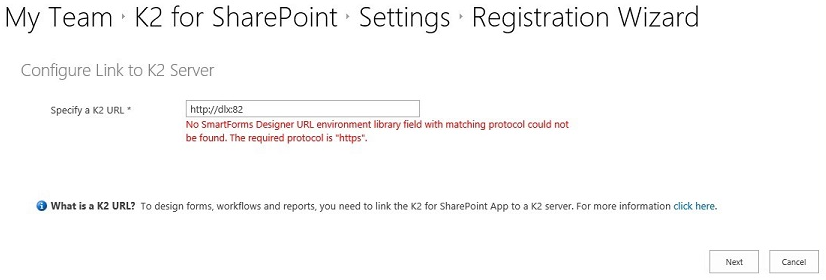
Web Service URL:
Resolution:
Ensure that there are environment library fields with matching protocols for the SmartForms Runtime URL, SmartForms Designer URL and Web Service URL.
Issue:
When using common consent, an intermittent issue occurs in AAD whereby the K2 App's requests no longer function as expected:
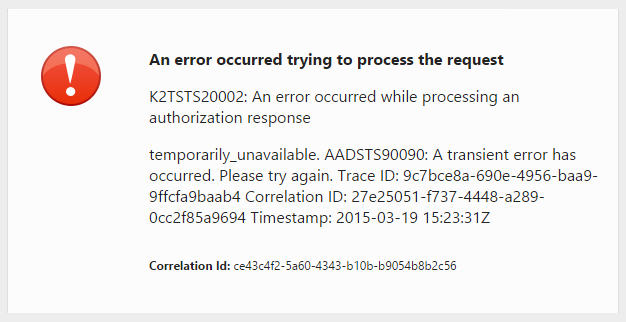
Resolution:
Remove the K2 App from the specific O365 tenant, then run through the consent again.
Issue:
Typical error: Sorry, something went wrong. The specified application identifier [GUID] is invalid or does not exist. Reproduce the error by following these steps:
- From Central Administration, select Apps option in the left-hand menu.
- Select the Configure Apps URLs option. If Apps are not enabled it will result in the following error:
Resolution: make sure that Apps are enabled for SharePoint 2013 and the permissions are set as in: Permissions.
Issue:
Various authorization issues similar to the following are experienced:
- 401 access denied.
- Cannot initialize client context.
-
Access denied when opening the K2 App from a list or library.
Resolution:
The following steps are typical of a support call to determine if the issue is related to the User Profile Service:
- Execute the following SMO as it will also give a 401 error if the profile is not valid. You can this to check if the user is part of a group. (SharePoint/{Site}/Management/Group SMO with method “Is User In Any One Group” to get the Groups to check the permission). Try executing the SMO directly for this user getting the issue.
Side note: the method requires a GroupID and username. Use SPM2013 to get the Group ID’s or look at the URL when opening the group. - Check that the Profile Synchronization Service is running. Also check that it passed. “User Profile Service Application - System Job to Manage User Profile Synchronization” (Central Admin > Monitoring > Check Job status).
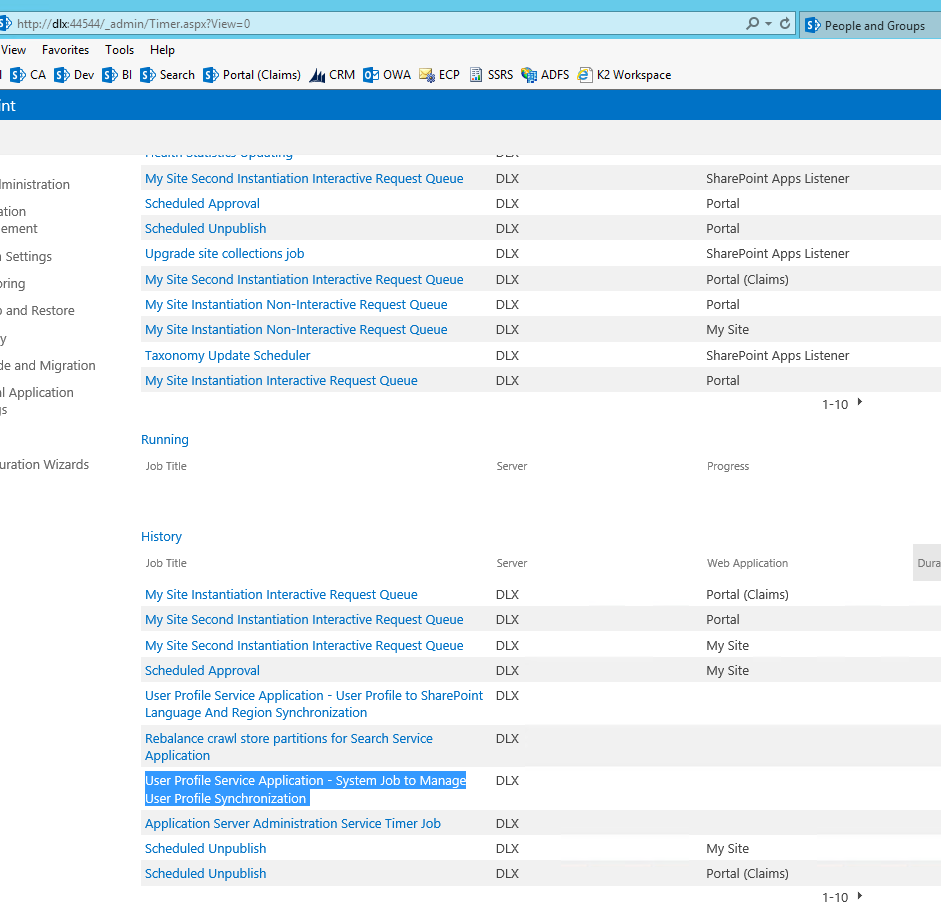
- For you to successfully validate permissions, you need to check the SID and userPrincipalName in SharePoint User Profiles. To check this, navigate to Central Administration > Application Management > Service Applications > Manage Service Applications. Find the User Profile Service Application (top node, not the Proxy) “Manage Profile Service: User Profile Service Application” screen should be open now. On the right hand side of the page (see the image below), you can see if the service is running and also the number of profiles. This should not be 0 if the service is running correctly.
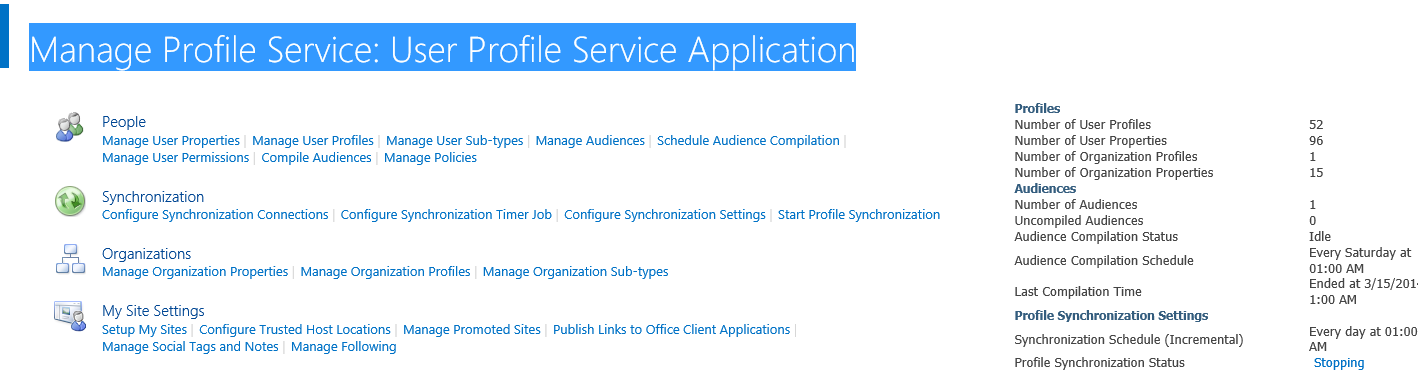
- If step 3 above is correct, navigate to the “People > Manage User Properties”. Here you will see all of the properties the SharePoint User Profile synchronizes from Active Directory. Check if the SID and userPrincipalName is there, and if not, add and map them.
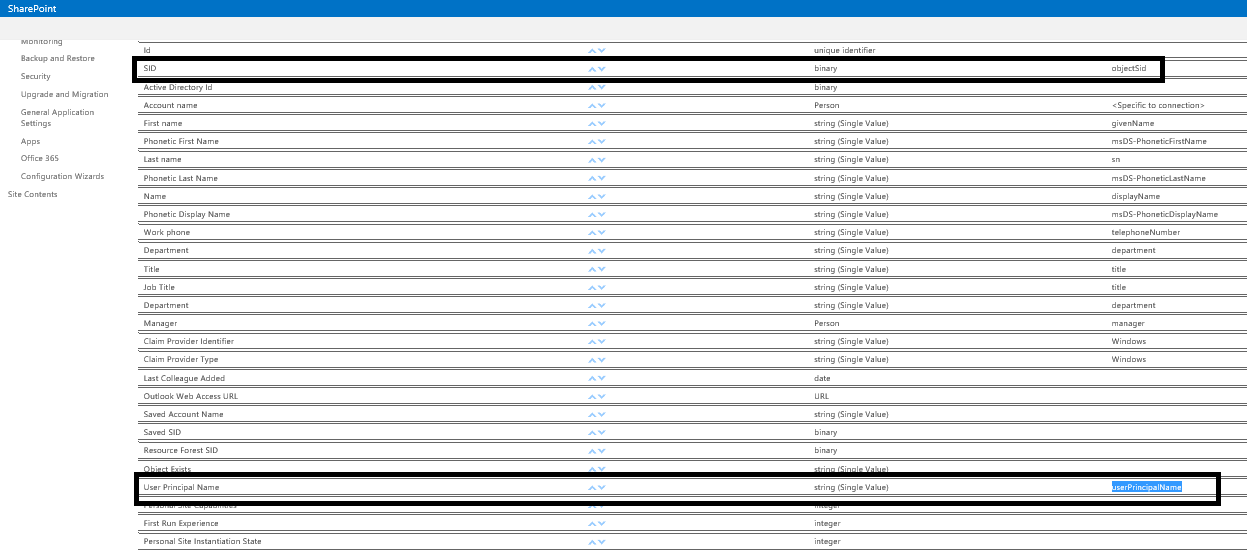
Be sure the following properties are set for the user:
- For on-premises installations, you will require at least the SID and userPrincipalName property to be set on the user’s profile.
- If using external SAML claims users, the identifier claim configured on the trusted provider must be either userPrincipalName, email address, SIP address or NameId. Additionally, this property must be set on the user’s profile.
Issue:
With multiple web applications defined, some or all are not shown in the App Deployment Wizard.
Resolutions:
There may be multiple resolutions depending on the underlying problem. Perform the following steps to correct this issue:
- Confirm that each of the web applications have app catalogs set up then re-run the App Deployment Wizard (AppDeployment.exe)
- Add the account used to run the App Deployment Wizard, to the site collection administrators for each app catalog. Then re-run the App Deployment Wizard (AppDeployment.exe). The user doing the install must be a site collection administrator.
See the Microsoft article, Install and manage apps for SharePoint 2013, for more information.
Issue:
After upgrading to K2 4.7 in a SharePoint environment upgraded from SharePoint 2010 to SharePoint 2013, the K2 app cannot be activated on SharePoint sites.
The issue is caused by K2 for SharePoint 2010 web parts (such as the K2 Worklist and K2 Task List) which weren't removed prior to upgrading to K2 4.7.
Resolution:
To resolve the issue follow these steps:
- Open the web part gallery on each site where the K2 app failed to activate.
- Remove all K2 for SharePoint 2010 web parts from each site's web part gallery.
- Rerun the app activation on the App Catalog and specify the sites for activation.
Issue:
When running the registration wizard using the K2 Service account, a login screen appears during the Administrative OAuth Token step. Entering the K2 Service account details results in the following error: "Sorry, but we're having trouble signing you in. We received a bad request."
Resolution:
Make sure to sign is as an AAD Global Administrator. K2 recommends you use the K2 Service account when running the registration wizard in SharePoint Online and that the service account is a member of the Global Administrators group in AAD. To add the account to the Global Administrators group in AAD, follow these steps:
- In the AAD admin center, open Users and Groups
- In All users, search for the service account
- Select Global Administrator as the Directory Role