Credentials Delegation
K2 Pass-Through Authentication offers a number of methods for delegating or storing securely a set of user credentials and then delegating them. These options enable K2 Pass-Through to be as intuitive as possible yet there may be additional setup and configuration required along with prerequisites and potential limitations.
The options that are available for Delegation are:
K2 Delegation Overview
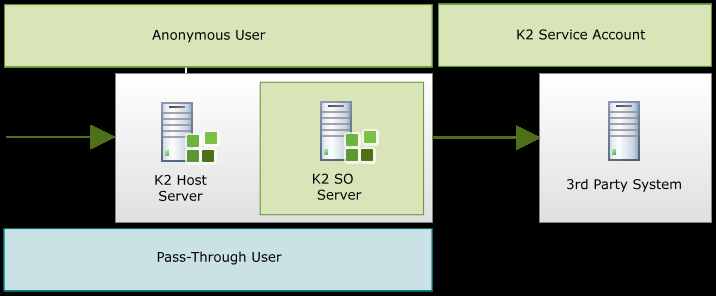
The K2 Server which is a Hosted Service (including the K2 SmartObject Server) may at times be required to pass the Client’s credentials to a 3rd party system.The K2 Workflow Server, which is one of the hosted services, does not independently perform delegation of the Client’s credentials. Since the K2 Workflow Server is a hosted service it only calls 3rd party systems asynchronously (not in real time), such as within a workflow’s Server Event. The physical limitation with this is that there will never be any client credentials to delegate by the hosted service.
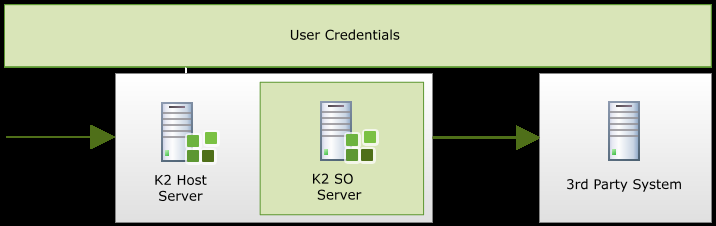
When K2 Pass-Through Authentication is necessary for the connection from InfoPath to the K2 Host Server, only the K2 Server has the K2 Pass-Through Authentication user. This identity is only recognized by the K2 Server and not any 3rd party system. This prevents the K2 Server from passing any credentials to SharePoint for example, and the K2 Service Account is used as if there is no pass-through because this is a delegation scenario. If Kerberos were configured, the Client’s credentials would be passed through the chain all the way to SharePoint (InfoPath to K2 Host Server to K2 SmartObject Server to SharePoint).