SharePoint Impersonation
Microsoft SharePoint includes native impersonation capabilities, which can be leveraged when Kerberos has not been configured and credentials need to be passed between machines. One particular scenario where the SharePoint Impersonation can be useful is when SSO capabilities are not available and SharePoint based Service Instances must be executed as the service account.
Service Instance Configuration
From within K2 Workspace, the service instances are configured and the enforce impersonation flag for the relevant service must be set to false. In spite of SharePoint impersonating the Client, the K2 SmartObject Server is unaware of this so if the impersonation flag is set to true, the authentication attempt will be blocked.
How it Works
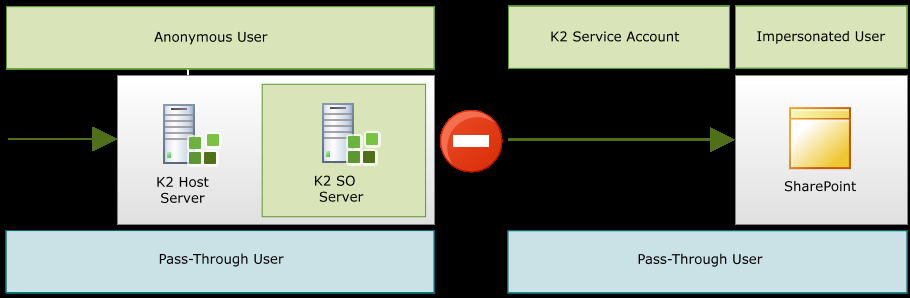
The K2 SmartObject Server passes the details of the K2 Pass-Through Authentication user to K2’s SharePoint-based web service. From this point SharePoint’s native impersonation features are used to impersonate the K2 Pass -Through Client user. This methodology is fully supported by Microsoft’s SharePoint, and the Client has been successfully impersonated all activity with SharePoint will be logged as being performed by the client, using the client’s credentials in the same manner that they would have had Kerberos been configured, for example, if a new list item was created the audit will reflect that the Client user created the List Item and this is supported in all versions of SharePoint.