Enforce Impersonation
 |
In scenarios where SharePoint Impersonation or Dynamic SQL Service Impersonation are being used; if the Enforce Impersonation flag is set to True the native impersonation functionality of the SharePoint Server and the SQL Server Respectively will reject the connection attempt. See the relevant topics for further information. Links are provided in this Caution Box. |
If K2 Pass-Through had been called by a service instance and there were no cached credentials for Single Sign On to be used then there would be no user credentials available. In certain instances, it would be acceptable that the K2 Service Account be used to impersonate the Pass-Through user. There are scenarios where setting this flag to true to enforce the impersonation would be unacceptable ie Auditing Processes where the User Credentials should be used to record user access and not the service account.
To provide security an additional, user configurable flag has been added called EnforceImpersonation. This setting is configured using the K2 Workspace Service instance tooling.
 |
By default this flag is set to FALSE |
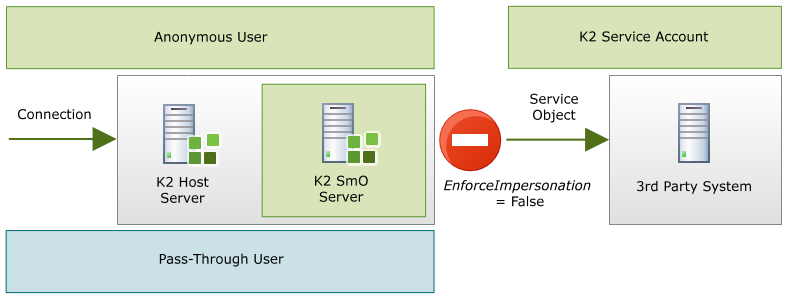
 |
If Kerberos were configured and functioning or Pass-Through had taken place, this setting would be redundant as the K2 Server would be executing as the Client User and there is no reason to prevent the connection. |
