Dynamic SQL Server ServiceObject Impersonation
SQL Server includes native impersonation capabilities which can be leveraged when Kerberos has not been configured and credentials need to be passed between machines to authenticate the K2 Pass-Through User.
Service Instance Configuration
From within K2 Workspace, the service instances are configured and the enforce impersonation flag for the relevant service must be set to false. In spite of SQL Server impersonating the Client, the K2 SmartObject Server is unaware of this so if the impersonation flag is set to true, the authentication attempt will be blocked.
 |
If the Enforce Impersonation flag is set to true, this will result in an Anonymous User error and authentication will fail. The event will be logged in the K2 Logs. See the section on Log Messages. |
How it Works
K2 Pass-Through utilizes the K2 Dynamic SQL Server Service Object to impersonate the Pass-Through User. This then allows the K2 Server via the K2 SQL Server Service Object to impersonate the end user to access secure data sources authentically and without creating a security risk and this in spite of only having the K2 Service Account where no Kerberos has been configured or SSO credentials are available.
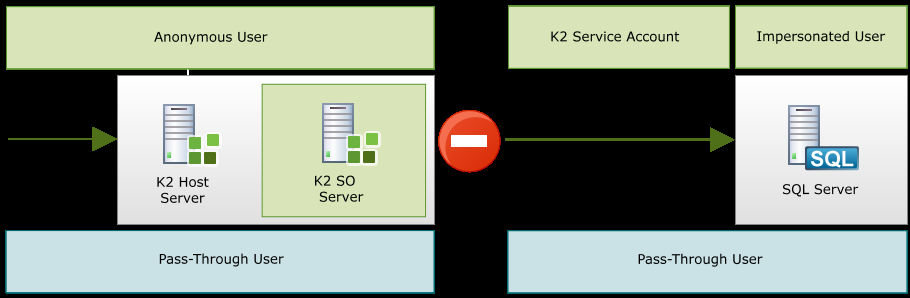
Authenticating Against the SQL Server Impersonation Functionality
The Dynamic SQL Server Service is able to negotiate the credentials passing of the Pass-Through User by using SQL Server’s User Impersonation capability. SQL Server has an “EXECUTE AS LOGON” connection string property. Since this method is available as a SQL Server Product feature, it has the support of the product vendor.
