Security Audit SmartObject
Use the Security Audit SmartObject to generate an audit log of all authorization framework security changes in your K2 environment. You can, for example, use this SmartObject to generate reports for auditing, compliance or regulatory purposes. You must be a member of the Security Administrators role to execute methods of the Security Audit SmartObject. Find this SmartObject in the K2 Designer at: All Items > System > Management > Security > SmartObjects > Security Audit and in K2 Management at Categories > System > Management > Security > SmartObjects > Security Audit in K2 Management.
Do not modify System SmartObjects in any way. These SmartObjects are used internally by K2, and K2 software updates may modify these SmartObjects, undoing your changes. If you wish to modify a System SmartObject, create a copy of the SmartObject and edit the copy.
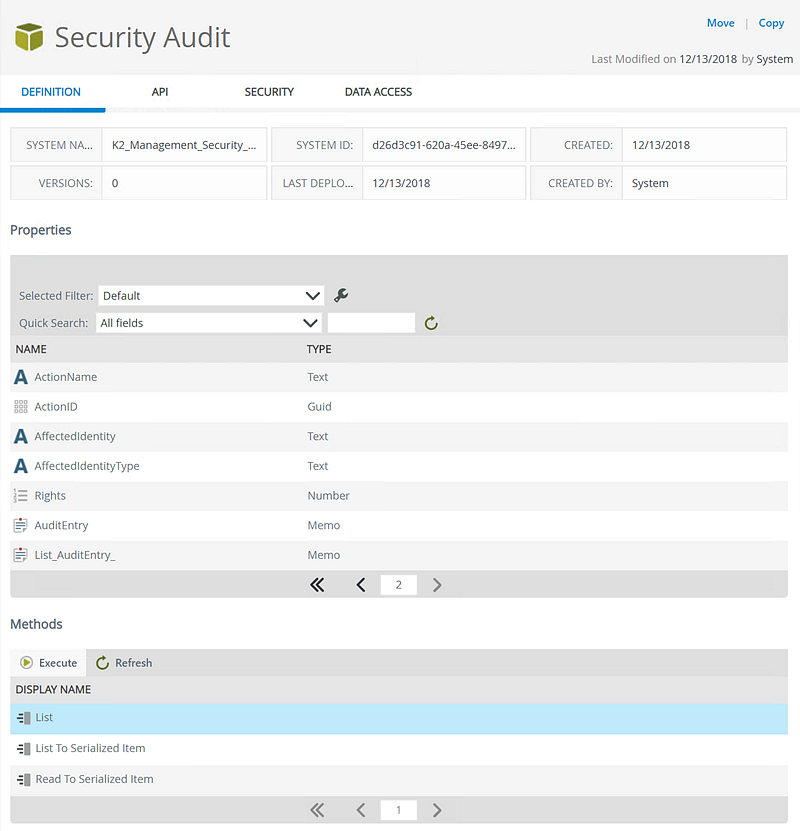
SmartObject Properties
| Name | Type | Description | Example Value | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| AuditID | Number | The unique ID of the audit item | 2269 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| LogTimeStampUtc | DateTime | The time stamp of the of audit log item, in UTC format | 2018-12-18T10:53:10 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ModifiedBy | Text | The user, group or role that made the security change | K2:DENALLIX\Administrator | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ModifiedByType | Text | The identity type that made the change. Can be a User, Role or Group | User | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| AuditActionName | Text |
This is the action that was performed on an object, class or identity. The following actions can be performed:
|
Register | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ClassName | Text | The type of entity that the security action was performed against | Application | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ClassID | GUID | The global unique identifier of the affected entity | 45d0bfee-408f-4762-b971-420b980b279 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ObjectName | Text | The name of the affected entity | Employees | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ObjectDisplayName | Text | The display name of the affected entity | Workspace Registration | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ObjectID | GUID | The unique ID of the affected entity | 45d0bfee-408f-4762-b971-420b980b279 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ActionName | Text | The name of the logged action performed | View Data | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ActionID | GUID | The ID of the action in GUID format | 45d0bfee-408f-4762-b971-420b980b279 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| AffectedIdentity | Text | The identity affected by the security change | Security Administrators | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| AffectedIdentityType | Text | The identity type of the identity affected by the security change | Role | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rights | Number |
The Authorization right that was logged. Use the table below to identify which right was logged:
A rights value can be a combination of values, for example, Create and Execute rights are 16777216 + 128. The easiest way to see which values combine to give the rights value is to convert the value to hexadecimal. For example, the combination of Create and Execute rights is 16777344, which in hexadecimal is 1000080. |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| AuditEntry | Memo | The AuditEntry represents all the return properties as a single line of text. It contains all of the information for a single log entry (AuditId, LogTimestampUtc, etc) as JSON-formatted text | {"AuditID":2322,"LogTimeStampUtc":"2018-12-14T05:43:33.727","ModifiedBy":"K2:DENALLIX\\BOB", "ModifiedByType":"User","AuditActionName":"Register","ClassName":null,"ClassID":"3edb0c3c-07e2-45a8-b254-c62ada5ff90f", "ObjectName":"Employees","ObjectDisplayName":null,"ObjectID":"d7c69dd4-5273-4fc9-ba05-54c8bddaeefa", "ActionName":null,"ActionID":null,"AffectedIdentity":null,"AffectedIdentityType":null,"Rights":null} |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| List_AuditEntry_ | Memo | The List_AuditEntry_ is all the return properties for all the returned log entries (more than one AuditEntry value) combined as a single JSON-formatted line of text | {"AuditID":2322,"LogTimeStampUtc":"2018-12-14T05:43:33.727","ModifiedBy":"K2:DENALLIX\\BOB", "ModifiedByType":"User","AuditActionName":"Register","ClassName":null,"ClassID":"3edb0c3c-07e2-45a8-b254-c62ada5ff90f", "ObjectName":"Employees","ObjectDisplayName":null,"ObjectID":"d7c69dd4-5273-4fc9-ba05-54c8bddaeefa", "ActionName":null,"ActionID":null,"AffectedIdentity":null,"AffectedIdentityType":null,"Rights":null} |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
SmartObject Methods
The Security Audit SmartObject includes the following methods:
| Method | Description | Properties |
|---|---|---|
| List | Lists all the properties and their values of the SmartObject |
|
| List To Serialized Item | Lists all properties in a serialized format | AuditEntry |
| Read to Serialized Item | Reads all properties in a serialized format | List_AuditEntry_ |
Example: using the Security Audit SmartObject
You can create a list view in K2 Designer to build a re-usable View and Form to list security audit events, or execute the Security Audit SmartObject in K2 Management to list security changes in your environment.
In K2 Designer, generate a list view of the Security Audit SmartObject and run the view to view the audit log: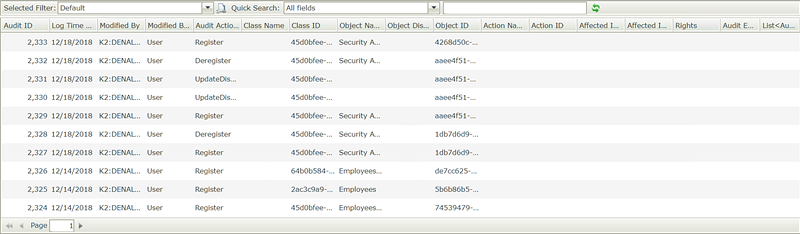
In K2 Management, execute the List, List To Serialized Item, or and Read to Serialized Item methods, to view the audit log: 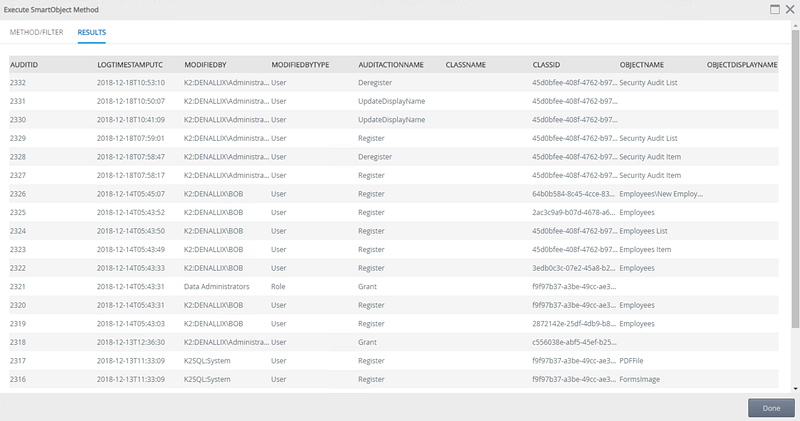
Considerations
- There is no retention policy applied to the audit logs captured by the Security Audit SmartObject. Audit log information is retained indefinitely in your SQL database. If you want to remove the audit log information, contact Nintex Customer Central for further assistance
- Audit Log information is stored in your SQL database not in files. If your database begins to run out of disk space and you want to free up space by removing audit log information, contact Nintex Customer Central for further assistance
- The security audit SmartObject only stores security changes set from the authorization framework.