Claims Issues
This section covers common issues you may encounter with Claims-Based Authentication (CBA), as well as recommended resolutions.
The K2 server logs an Info event (Enrolling Type: SourceCode.Security.Providers…) for each configured user manager. Verify the expected user managers are loading correctly.
The following errors may occur when K2 is not configured correctly for claims-based authentication.
- Error: ID4175: The issuer of the security token was not recognized by the IssuerNameRegistry. To accept security tokens from this issuer, configure the IssuerNameRegistry to return a valid name for this issuer.
This is an error from the Identity Framework when it validates the claims tokens against the trusted issuers name and thumbprint. This indicates that the values provided in K2HostServer.exe.config do not match what SharePoint returns. There is a known issue when copying from the certificate properties window in MMC into the config file and getting an extra non-printable character in the text string, which causes the thumbprint match to fail. To resolve this, delete the entire thumbprint tag in the K2HostServer.exe.config file, including the double-quotes, to ensure that there are no special characters left. Then use the thumbprint value returned from the SharePoint PowerShell command as recommended in the topic: Claims and OAuth Configuration. - Errors: "Token of type X not supported" or "A valid [SAML1.1/SAML2] Token is required" or "Not a valid [SAML1.1/SAML2] claims token".
This is an error from K2 indicating the claims token type is not supported or K2 was not able to process the claims token. K2 supports SAML 1.1 and SAML 2.0 claims token types. For more information, see the topic: Claims and OAuth Configuration. - Error: System.Exception: Deploying user '[Security Label]:[Domain\Username]' does not have impersonate rights.
This error will appear in K2 Designer for SharePoint (legacy) at deployment and indicates that after the claims changes were applied to the K2HostServer.exe.config, the K2 server needed to be restarted followed by an IISRESET.
AD FS 2.0
AD FS 2.0 can be challenging to configure. For more information, please refer to the numerous articles listed in Claims References.
A generic error message is displayed when AD FS encounters an issue with the user login.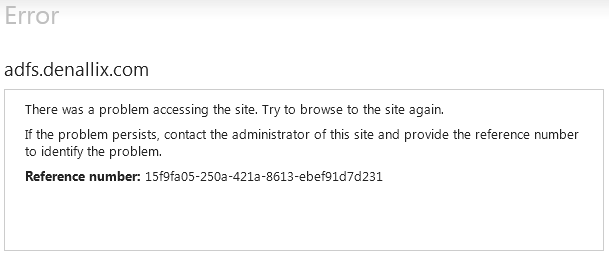
Open the Event Viewer and navigate to the Applications and Services Logs > AD FS 2.0 > Admin log to see more detailed information on the error.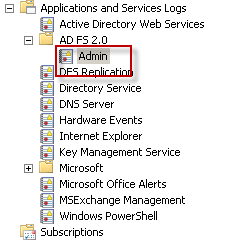
In addition to the Admin log, AD FS 2.0 provides detailed trace information through debug logging. For more information, see How to Enable Debug Logging for Active Directory Federation Services 2.0 (AD FS 2.0).
Some changes in AD FS configuration require a recycling of the user cookies, the AD FS service and the IIS site hosting AD FS:
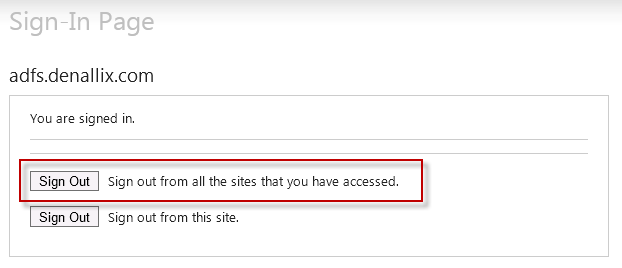
- Expire Cookies: Navigate to [IISWebSite]/adfs/ls/idpinitiatedsignon.aspx and click on Sign Out from all sites.
- Restart the AD FS service:
net stop adfssrv
net start adfssrv - Restart IIS web site:
iisreset