Impersonating a User
You may need to impersonate another user after establishing the initial connection to K2. This is especially useful in situations where you are not able to obtain the original user’s Active Directory credentials, but still need to connect to K2 as that user so that you can complete a worklist item that was assigned to them. For example, suppose you have a ASP.NET website that will allow a user to work with their K2 Worklist. That website resides on a physically separate IIS server to the server hosting the K2 host service.. For whatever reason, it is not possible to configure Kerberos delegation between the IIS serve and the K2 server to allow user credentials to seamlessly flow between the two servers. Therefore, when the ASP.NET code on the IIS server attempt to connect to K2 without specifying a username or password, the user that is connected to K2 is actually the App Pool identity of the IIS website hosting the ASP.NET application, and NOT the identity of the user that is opening the web page.
This is where the ImpersonateUser() method comes into play: it effectively allows you to switch to another user’s security context, perform some tasks on the K2 server and then switch back to the original connected user’s context. In the example above, you would grant the App Pool Identity of the website hosting the ASP.NET application the Impersonate permission, and as long as you are able to obtain the connected user's username, the App Pool Id will be able to impersonate the connected user when connecting to the K2 server.
The SourceCode.Workflow.Client API provides methods to allow authorized accounts to impersonate user and perform actions such as
- Starting workflows
- Retrieving worklists
- Opening and completing worklist items
- Redirecting and delegating tasks
The
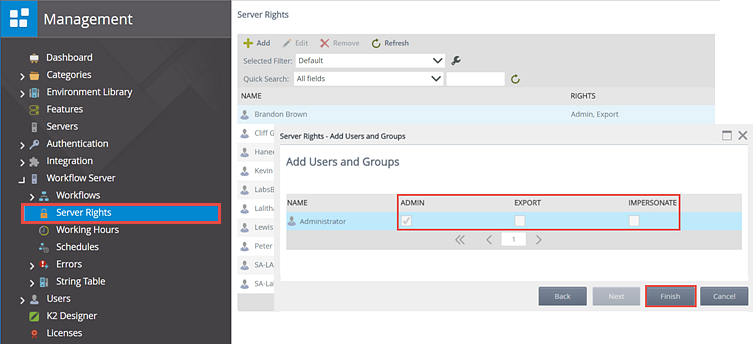
For security purposes, only those user accounts with the Impersonate permission on the K2 environment will be able to call the ImpersonateUser() method. The screenshot below shows where this permission is set.
This sample code requires references to the assemblies:
- SourceCode.HostClientAPI
- SourceCode.Workflow.Client
//connect to the K2 server as the current user account
K2Conn.Open("localhost");
//once connected to K2, the connected account can impersonate another user
//but the connected account must have "Impersonate" permission
K2Conn.ImpersonateUser(@ "K2:domain\username");
try {
//perform actions on behalf of that user. e.g.
//do something with impersonated user"s worklist
Worklist K2WL = K2Conn.OpenWorklist();
} catch (Exception ex) {
//do something with exception
} finally {
//when you are done impersonating, revert to the original account
K2Conn.RevertUser();
}
}