Service Instances
Service Types are "connectors" that allow K2 to integrate with particular technologies, while Service Instances are configured instances of a Service Type that connect to specific occurrences of that technology. For example: the EndPoints WebService Service Type allows K2 to interact with web services, while an Instance of the EndPoints Web Service must be configured to allow K2 to connect to a specific Web Service at a particular URL, before a developer can create SmartObjects that interact with that particular web service.
Clicking on the Service Instances node displays a list of the registered Service Instances in your environment. You can create, edit and delete instances. You can also generate SmartObjects for an instance, refresh an instance or refresh the instances list.
- If you expect to see a specific service instance in the list and it does not show, you may not have the sufficient rights to do so. See Authorization Framework Overview for information about rights and permissions.
- From time to time it may be necessary to refresh a service instance so that K2 can "discover" any changes to the underlying system. For example, if you have previously configured a Service Instance that connects to a SQL database and new tables or views are added to the SQL database, you will need to Refresh the Service Instance so that K2 can discover the new tables or views in the database, which in turn allows for new SmartObjects to be generated or created that can use those new tables and views.
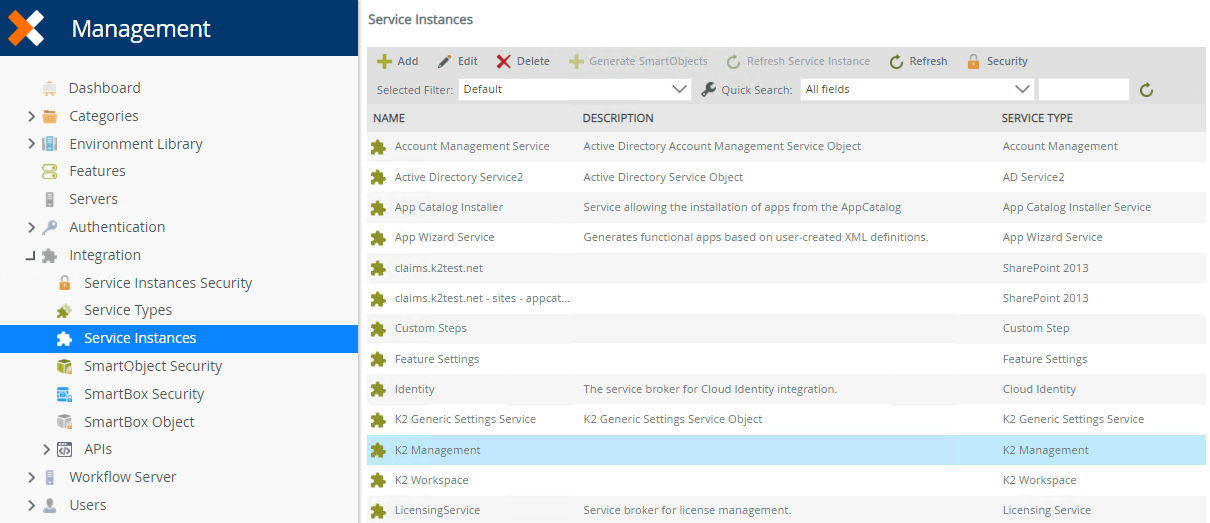
- Click Add from the Service Instances view.
Click New Instance. The Configure Service Instance page opens.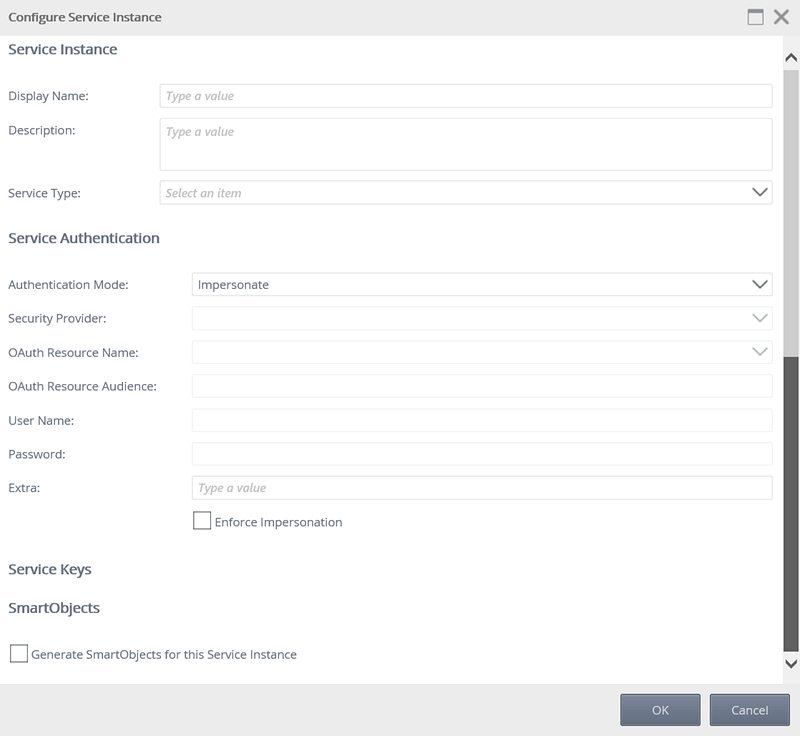
Use the table below as a guideline to configure the new service instance:
Section Field What to do Service Instance Display Name Type a value for the display name of the new service instance. Service Instance Description Type a value to describe the new service instance. Service Instance Service Type The Service Type selected from the previous view will display. You can select a different Service Type from the drop-down if needed. Service Authentication Authentication Mode Select the Authentication Mode to be used for this service instance from the drop-down. This setting determines the security credentials that will be used to connect to the underlying system. See the topic Authentication Modes for more information.
Not all Authentication Modes are supported for all Service Types. Refer to the Service Type documentation for the particular Service Type you wish to configure to see what known Authentication Mode restrictions may exist.- Impersonate: passes the connected user's credentials to the underlying system
- OAuth: uses OAuth tokens to authenticate with the underlying system. This setting requires a configured OAuth resource for the underlying system.
- ServiceAccount: connects to the underlying system using the credentials of the account that runs the K2 application service
- SSO: uses cached Single Sign-On credentials for the connected user. This setting will require you to select a Security Provider that will map an incoming user's credentials to alternate credentials that are accepted by the underlying system.
- Static: use a static username and password to connect to the underlying system
Service Authentication Security Provider The Security Provider drop-down will be enabled when the single sign on (SSO) Authentication Mode was selected. Select the security provider to be used from the drop-down. Service Authentication OAuth Resource Name This drop-down will be enabled when the OAuth Authentication Mode was selected. Select the OAuth resource name to be used from the drop-down.(The Resource is defined using the Authentication section of the K2 management site.) Service Authentication OAuth Resource Audience Enter the OAuth Resource Audience URI to use for OAuth Authentication. This setting is only applicable when using the OAuth Authentication Mode, and refers to the URI used to access a realm, for example https://graph.windows.net Service Authentication User Name This field will be enabled when the Static Authentication Mode was selected. Type the name of the user to be used when connecting to the underlying system. Service Authentication Password This field will be enabled when the Static Authentication Mode was selected. Type the password of the user entered in the User Name field. Service Authentication Extra Type a value for extra connection information. This setting is usually not required unless the authentication mechanism or Service Type selected requires or allows additional configuration. Service Authentication Enforce Impersonation This is a Pass-through Authentication option and is only applicable for the Impersonate and OAuth Authentication Modes. If Enforce Impersonation is not checked and Pass-through Authentication fails for the impersonated user, the service will revert to the K2 Service Account and retry the operation. If Enforce Impersonation is checked, the service will not revert to the Service Account if it fails with the impersonated user. Service Keys (The Service Keys depends on the Service Type selected). Provide the configuration settings for the particular Service Type you are configuring. See the documentation for the particular service type for more information on the available configuration values for that Service Type.
SmartObjects Generate SmartObjects for this Service Instance Select the check box if you want to automatically generate SmartObjects for the new Service Instance. (Whether this check box is selected or not, designers can still create SmartObjects for the underlying system manually using K2 Design tools). - Click OK to register the new Service Instance after providing the necessary values. It may take a few seconds for this operation to complete, since K2 may be performing discovery operations against a large set of entities, and/or generating and publishing SmartObjects, if the Generate SmartObjects option was selected.
You can edit the existing settings defined for a Service Instance.
- Select the Service Instance you want to edit. The Edit button becomes available.
- Click Edit.
- Type or select new configuration values for the instance and click OK. Refer to the table in the section Creating a New Service Instance for more information on the various configuration settings.
- Select the Service Instance you want to delete. Click Delete.
- Click OK on the confirmation window to confirm you want to delete the Service Instance.
You can tell K2 to automatically generate and publish SmartObjects for a Service Instance. If you have refreshed a Service Instance, you can use this button to generate SmartObjects for any new or changed artifacts in the underlying system. Note that designers will still be able to use K2 design tools to manually create SmartObjects that use the Service Instance, regardless of whether you have generated SmartObjects or not.
- Select the Service Instance you want to generate SmartObjects for. The Generate SmartObjects button becomes available.
- Click Generate SmartObjects.
- The Generate SmartObjects screen will open. Select the required SmartObject you wish to create, update or delete.
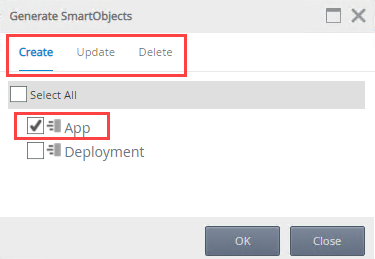
- Click OK to create, update or delete the SmartObject.
You may need to refresh a Service Instance to discover any changes that may have been made to the underlying data store. These steps explain how to do this.
- Select the Service Instance you want to refresh. The Refresh Service Instance button becomes available.
- Click Refresh Service InstanceDepending on the size of the underlying data store, it may take several seconds or even minutes for the refresh operation to complete.
The Refresh button provides an updated list of the Service Instances listed. Click the button to update the list to show any new or modified Service Instances since the last time the list was refreshed.
The Security button allows you to define design-time rules to control who is allowed to manage service instances and who can consume service instances within the design of their SmartObjects. Service instances inherit rights from the service type which in turn inherits rights from the service instances security level. See Authorization Framework Overview and Service Instances Security for more information about rights, inheritance, considerations, and best practices before assigning rights per service instance.
You can assign rights to a specific service instance, which allows you more granular control for each service instance.
| Right | Description |
|---|---|
| View |
Allows you to see and use the service instance at design time in K2 Management and K2 Designer. When a user, group, or role has View rights on a service instance, the user, group, or role can also view its parent service type even if the user, group, or role does not have View rights on the service type. However, it does not allow the user, group, or role to see other service instances of the same service type. |
| Modify |
Allows you to update this service instance in K2 Management. A user, group, or role requires Modify rights to refresh a service instance - This is because refreshing an instance modifies the available service objects and their definitions. |
| Delete |
Allows you to delete this service instance in K2 Management |
| Security |
Allows you to give other people the right to assign rights on this service instance |
Follow these steps to add rights to a specific service instance:
-
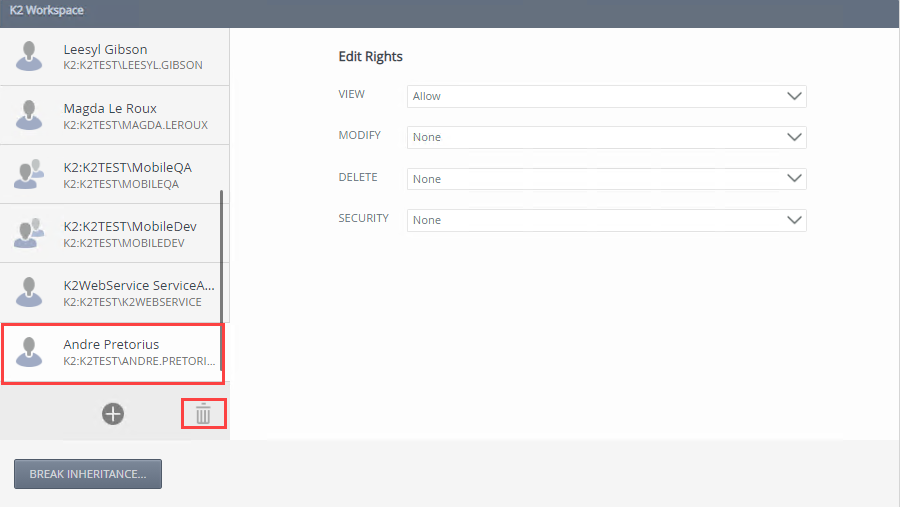
Select a service instance and then click Security.
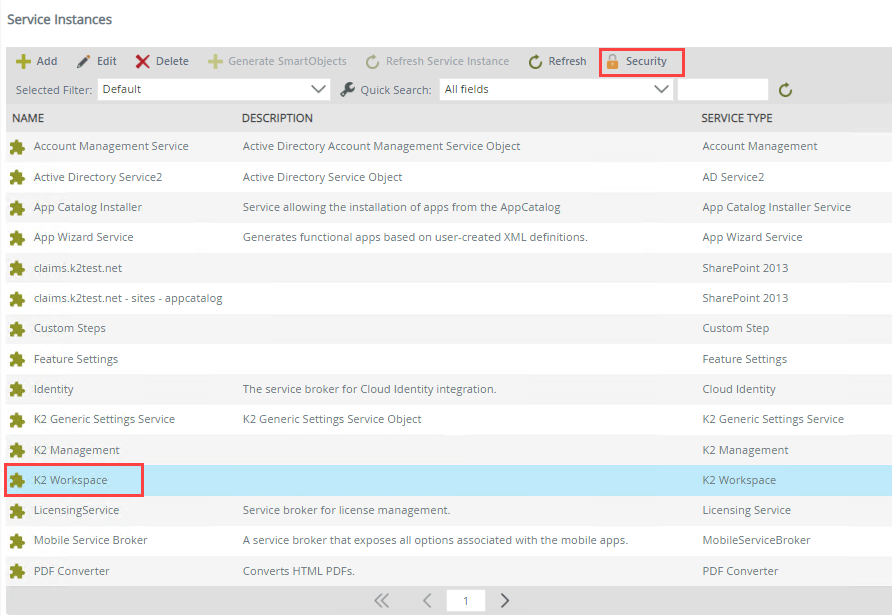
- Add a user, group, or role by clicking the Add button.
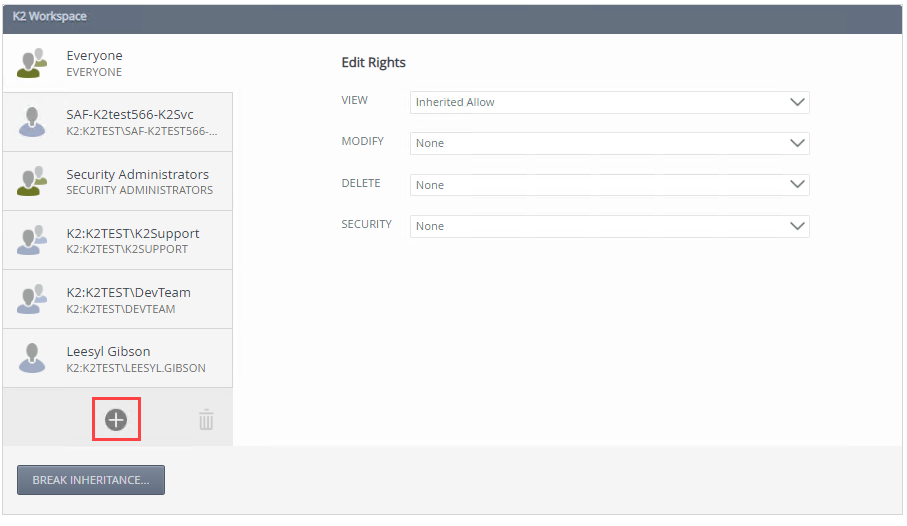
- On the Add Users, Groups, And Roles page search and add a user, group, or role. Click OK.
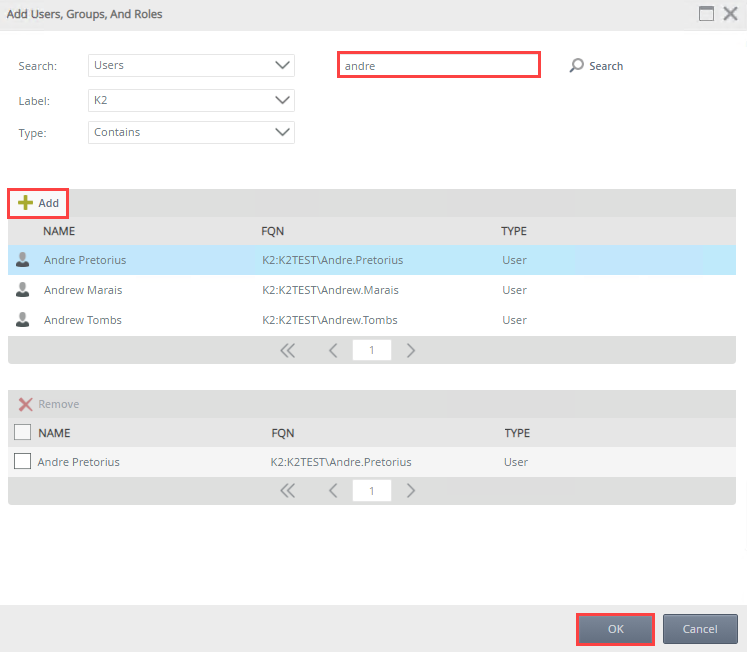
- Specify the user, group, or role's View, Modify, Delete, and Security rights. If the user, group, or role has rights at the service instances security or service type level, the following rights are available: Allow, Deny and Inherited Allow. If the user, group, or role does not have rights at the service instances security or service type level or if the inheritance is broken the following rights are available: Allow, Deny and None.
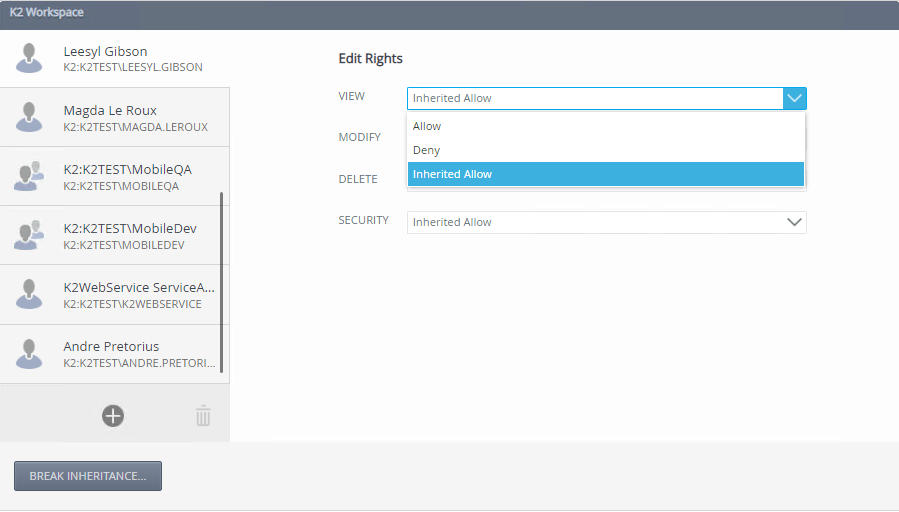
- Add more users, groups, and roles if necessary. Click Close.When specifying users, groups, and roles, the Everyone role is added during installation, providing all authenticated users, the ability to view service types and service instances. Best practice would be to modify the Everyone role's view rights to None on the Service Instances Security level, and grant permissions to users, groups, and roles according to your organizations requirement on the service type and service instance.
Follow these steps to edit service instance rights:
- Select the service instance and click Security.
- Select a user, group, or role and edit the rights. Click Close.
Follow these steps to remove edit service instance rights:
- Select the service instance and click Security.
- Select a required user, group, or role and click Remove.