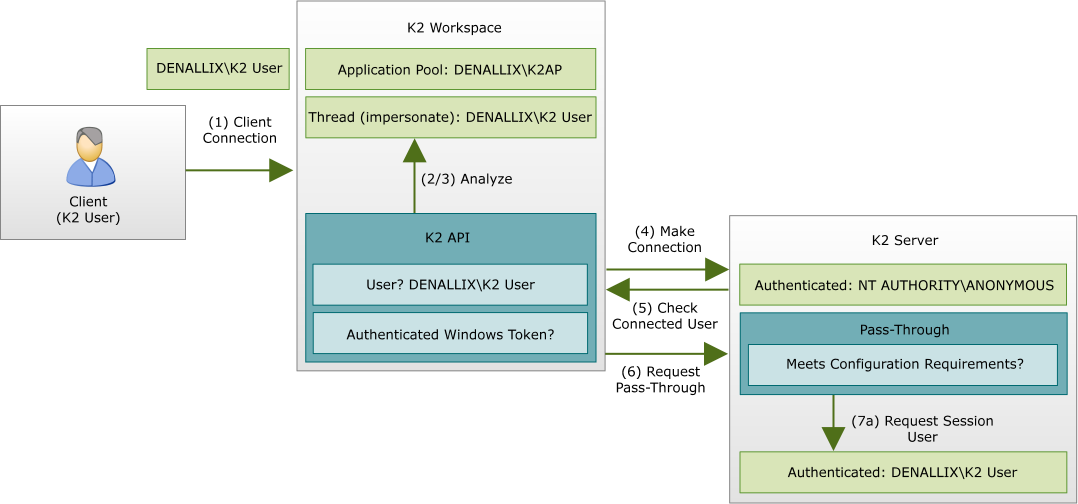
How K2 Pass-Through Authentication works
For K2 Pass-Through Authentication to function as securely as possible follows a protocol which is used to ensure that regardless of the manner in which the K2 Client APIs are used each valid authentication attempt is successful.
- A client which may be a thick or lite client e.g. K2 Workspace makes a normal connection to the relevant K2 client API.

This initial connection is secure even for custom applications as it’s all conducted internally
- The K2 client API will analyze the current configuration (e.g. user context and threads) to ascertain who is the intended end user of the application
- The user token is interrogated to ensure that it is a properly authenticated Windows token (e.g. against Active Directory).

This process is to verify the ClientWindows configuration option
- To initiate the process a connection is made to the K2 Server, just prior to K2 Pass-Through Authentication being performed
- The relevant K2 client API will ask the K2 Server which client was authenticated, to determine if it’s different to the user calculated in step (2)
- If there is a difference, then the K2 Client API will request K2 Pass-Through Authentication, and then send the K2 Server the user’s name, as well as passing in the result of (3)
- From the K2 Server’s side and depending on the requirements of the configuration option (e.g. ClientWindows):
- If step (6) is successful, the K2 Server will switch its security context from the current user (e.g. the anonymous user) to the K2 Pass-Through Authentication user
- If unsuccessful, an error will be logged due to the fact that there is a configuration issue on the client (by the fact that K2 Pass-Through Authentication failed). Any further functionality will continue as the user (e.g. anonymous) as connected in step (4), including any connections to back-end systems.

When configurable levels of trust are required for each server on an individual basis in a distributed environment, Kerberos should be considered as this feature is beyond the Scope of K2 Pass-Through Authentication.