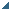
System.Object
SourceCode.Security.Cryptography.AsymmetricProtector
SourceCode.Security.Cryptography.BufferCleaner<T>
SourceCode.Security.Cryptography.BufferCleaner
SourceCode.Security.Cryptography.CryptoFactory
SourceCode.Security.Cryptography.SaltedItem
SourceCode.Security.Cryptography.SymmetricProtector
System.Random
SourceCode.Security.Cryptography.CryptoRandom
System.Security.Cryptography.DeriveBytes
SourceCode.Security.Cryptography.HKDF
SourceCode.Security.Cryptography.PBKDF2
System.Security.Cryptography.HashAlgorithm
SourceCode.Security.Cryptography.Murmur3
System.Security.Cryptography.KeyedHashAlgorithm
System.Security.Cryptography.HMAC
SourceCode.Security.Cryptography.HMAC2
System.ValueType
SourceCode.Security.Cryptography.EncryptionContextType
SourceCode.Security.Cryptography.AsymmetricProtector
SourceCode.Security.Cryptography.BufferCleaner<T>
SourceCode.Security.Cryptography.BufferCleaner
SourceCode.Security.Cryptography.CryptoFactory
SourceCode.Security.Cryptography.SaltedItem
SourceCode.Security.Cryptography.SymmetricProtector
System.Random
SourceCode.Security.Cryptography.CryptoRandom
System.Security.Cryptography.DeriveBytes
SourceCode.Security.Cryptography.HKDF
SourceCode.Security.Cryptography.PBKDF2
System.Security.Cryptography.HashAlgorithm
SourceCode.Security.Cryptography.Murmur3
System.Security.Cryptography.KeyedHashAlgorithm
System.Security.Cryptography.HMAC
SourceCode.Security.Cryptography.HMAC2
System.ValueType
SourceCode.Security.Cryptography.EncryptionContextType