Process Discovery TLS Configuration
The system file paths in this guide are the default Process Discovery Server installation.
Steps Overview
Step 1 - Stop Process Discovery services
Step 2 - Configure TLS in Aerboase
Step 3 - Configure Process Discovery
Step 4 - Start Process Discovery services
Step 6 - Configure Discovery Robots
Step 1 - Stop Process Discovery services
Shutdown the following Nintex windows services:
-
Nintex Server - Authentication Gateway
-
Nintex Server - Authentication Server
-
Nintex Server - Process Discovery Service
Step 2 - Configure TLS in Aerboase
-
Copy the server
.crtand.keycertificate files to Aerobase SSL folder (C:\Nintex\IDP\Aerobase\Configuration\ssl) -
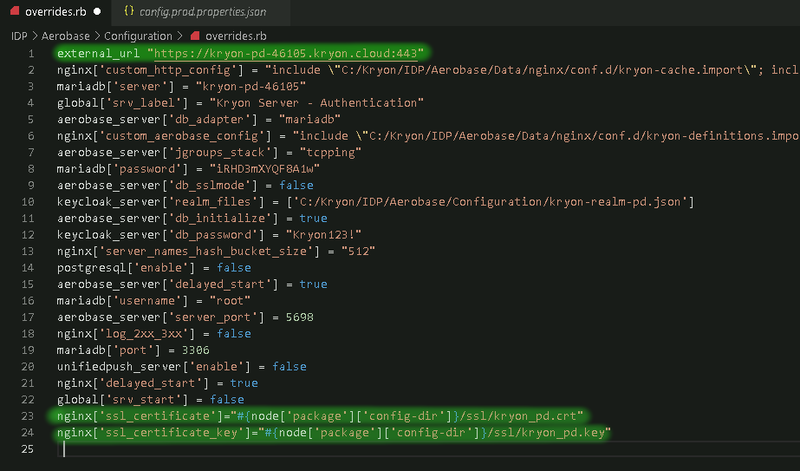
Edit the Aerobase configuration file C:\Nintex\IDP\Aerobase\Configuration\overrides.rb as follwing:
-
Modify the property
external_url: Change the protocol to https and the port to 443 -
Insert the following properties and set the file names to be exactly like the copied certificate names:
-
nginx['ssl_certificate']=
"#{node['package']['config-dir']}/ssl/<FILE_NAME>.crt" -
nginx['ssl_certificate_key']=
"#{node['package']['config-dir']}/ssl/<FILE_NAME>.key"
-
-
-
Run Aerobase configure command:
-
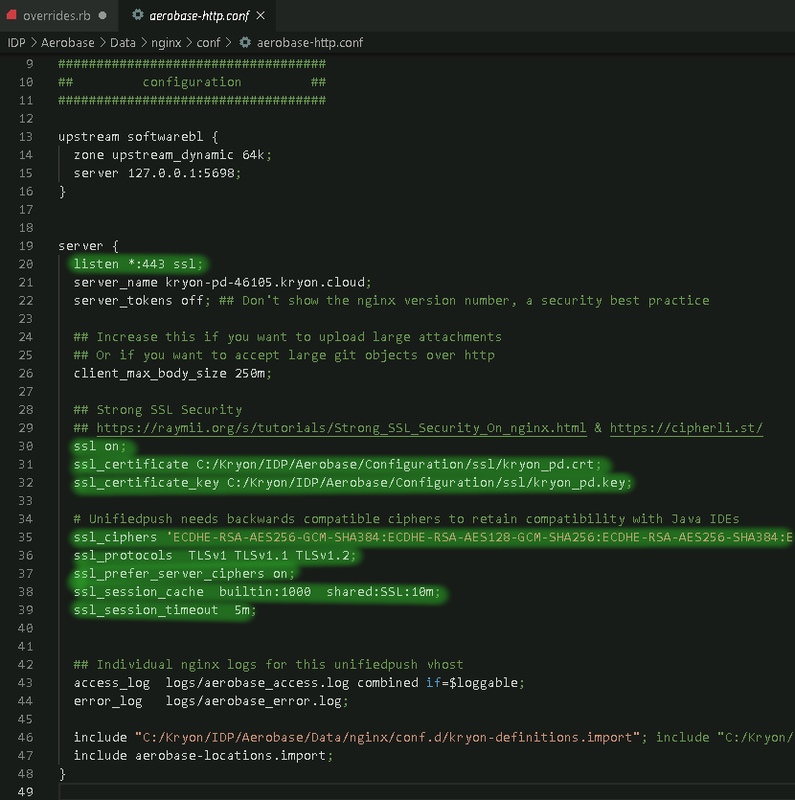
Validate the Aerobase TLS configuration by reviewing the file:
C:\Nintex\IDP\Aerobase\Data\nginx\conf\aerobase-http.conf
EXAMPLE:
-
If an issue occurs, check aerobase and nginx logs: C:\Nintex\IDP\Aerobase\Logs
- Upon any change to the aerobase override.rb file, make sure to re-run aerobase configuration
- The file names of the certificate must not contain dot characters (e.g., my.cert.crt)
-
Use only slashes “/” in the files path (not backslash! “\”).
EXAMPLE:
powershell
(Invoke-Command {cmd.exe /c C:\Nintex\IDP\Aerobase\Aerobase\bin\aerobase-ctl.bat reconfigure} | Out-File aerobase-reconfigure-output.txt)
Step 3 - Configure Process Discovery
-
Modify the Process Discovery configuration by editing the file C:\Nintex\installer-assets\config\prod\scripts\config.prod.properties.json and setting the following values:
-
"HTTP_TYPE": "https" -
"NGINX_PORT": 443 -
"NODEJS_CA_CERTS": "<PATH_TO_CA_BUNDLE>\ca_bundle.pem"
-
-
Run Process Discovery configureAll command:
-
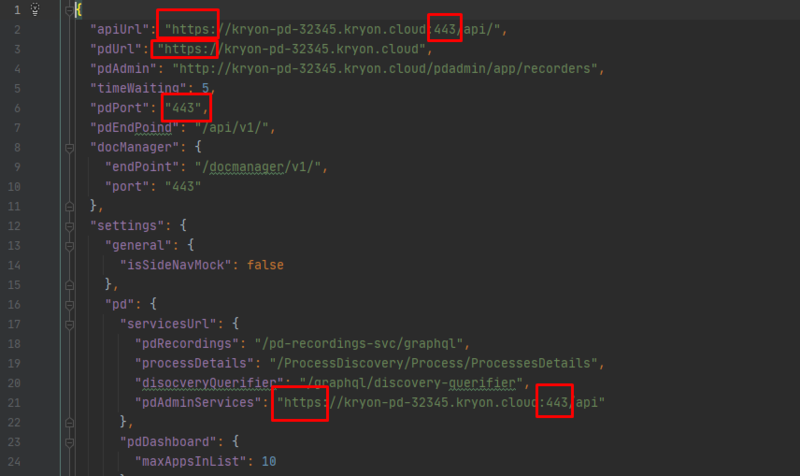
Modify the Console configuration by editing the file C:\Nintex\Console\Web\ConsoleX\assets\data\appConfig.prod.json and setting the following values:
-
“pdUrl”: Change the URL protocol to https
-
“pdPort”: Change the port to 443
-
“pdAdminServices”: Change the URL protocol to https and the port to 443
-
-
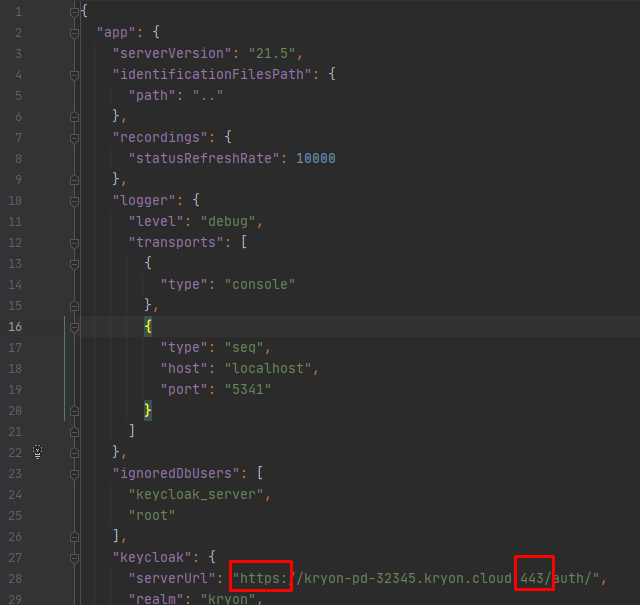
Verify the Process Discovery Admin configuration by opening the file C:\Nintex\PDServer\Orchestrator\config\production.json and verifying the following properties values:
-
In the “keycloak” section, ”serverUrl” property value is https and the port is 443.
-
EXAMPLE:
"NODEJS_CA_CERTS": "C:\\Nintex\\IDP\\Aerobase\\Configuration\\ssl\\cert.pem",
CD C:\Nintex\installer-assets\config\prod\scripts
powershell.exe -Command "C:\Nintex\installer-assets\config\prod\scripts\configureAll.ps1 -h 'C:\Nintex' -configDir 'C:\Nintex\config' -n prod -servicesDir 'C:\Nintex\PDServer\MicroServices' -utilsDir 'C:\Nintex\PDServer\Support'"
EXAMPLE:
EXAMPLE:
Step 4 - Start Process Discovery services
Start the following Nintex windows services:
-
Nintex Server - Authentication Gateway
-
Nintex Server - Authentication Server
-
Nintex Server - Process Discovery Service
Step 5 -Verify Server TLS
Verify TLS by opening your browser and accessing the Process Discovery components by using https://:
-
PD Console -
https://${SERVER_FQDN}/console -
Seq logging server -
https://${SERVER_FQDN}/seq -
Aerobase management -
https://${SERVER_FQDN}/auth/admin/kryon/console/#/realms/kryon
Step 6 - Configure Discovery Robots
-
On your client machine, open %localappdata%l\Nintex\ActionsRecorder\config\pddr.appsettings.config.
-
Modify the following parameters:
-
Re-run the Discovery Robot.
<add key="messagesProtocol" value="https"/> <!-- HTTPS protocol -->
<add key="messagesBrokerHost" value="${SERVER_FQDN}"/> <!-- with no protocol prefix -->
<add key="messagesBrokerPort" value="443"/> <!-- HTTPS port -->
<add key="IDPuthUrl" value="https://${SERVER_FQDN}/auth/"/> <!-- with no port specification -->