Aerobase MFA
The digital world faces many cybersecurity challenges today. As a solution to increase security in access management and add authentication to applications, Keycloak, an innovative open-source tool, was created. It provides an easy-to-use Multi-Factor Authentication (MFA) with one-time passwords (OTP).
Configuring the Keycloak Multi-Factor Authentication is a simple task. All that you need to do, is implement the need for all users, existing and new, to use one-time passwords. In this configuration, you can manually enforce these rules upon your users.
To access the portal, use the URL: http://[FQDN or IP]/auth/admin/kryon/console/#/realms/kryon.
Configure Aerobase Managed Users for MFA
To configure managed users for MFA:
-
Login to the Aerobase console, Keycloak Admin.
-
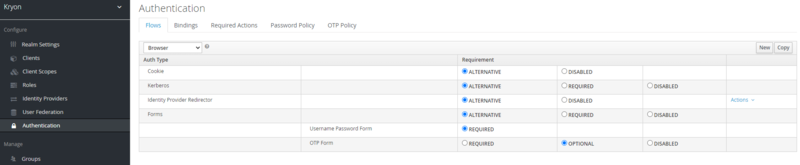
Go to Authentication (under Configure on the left pane).
-
On the Flow tab, make sure the OTP Form is set to REQUIRED or OPTIONAL.
-
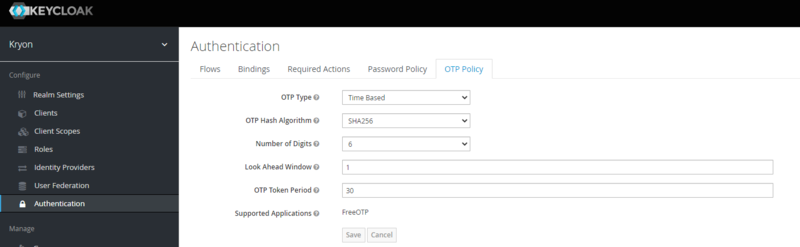
Open the OTP Policy tab and update the properties according to your policy.
-
Create or update a user: Go to Manage > Users > Create User (see Creating and Managing Admin Users for more details). Users and Roles in Aerobase/Keycloak and Nintex Admin Tool.
-
Make sure it is an Aerobase user.
-
LDAP or Identity providers users cannot be changed (it is up to the LDAP or IDP configuration).
-
-
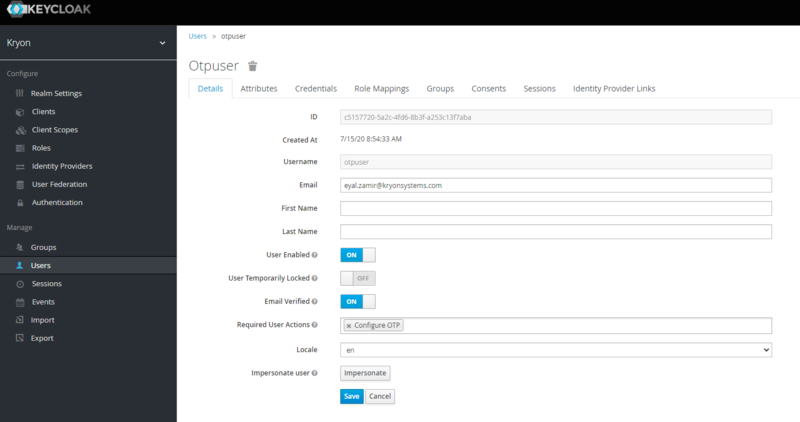
Go to Users (under Manage on the left pane).
-
Open the Details tab and by Required User Action, choose “Configure OTP”.
-
Click Save.
Log in with the Newly-Created User
Now, to complete the setup, log in with the newly-created user:
-
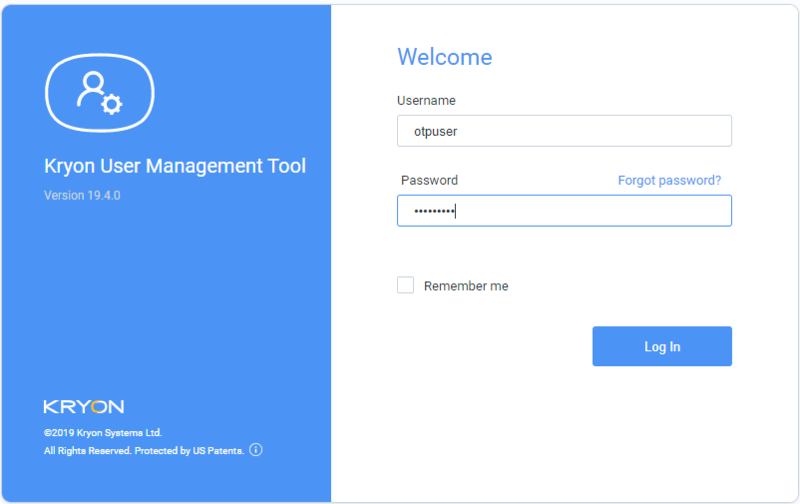
In the Nintex User Management Tool, type in the User's credentials.
-
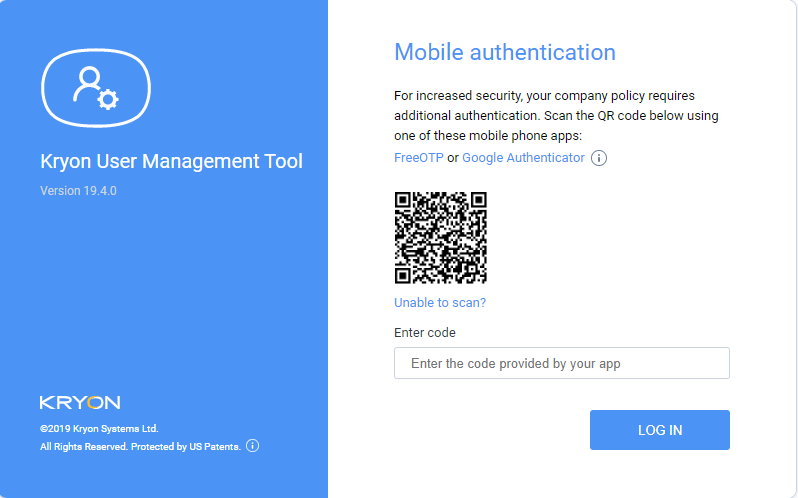
If you are using FreeOTP or Google Authenticator, you can now scan the QR code, enter the code, and press Log In.
-
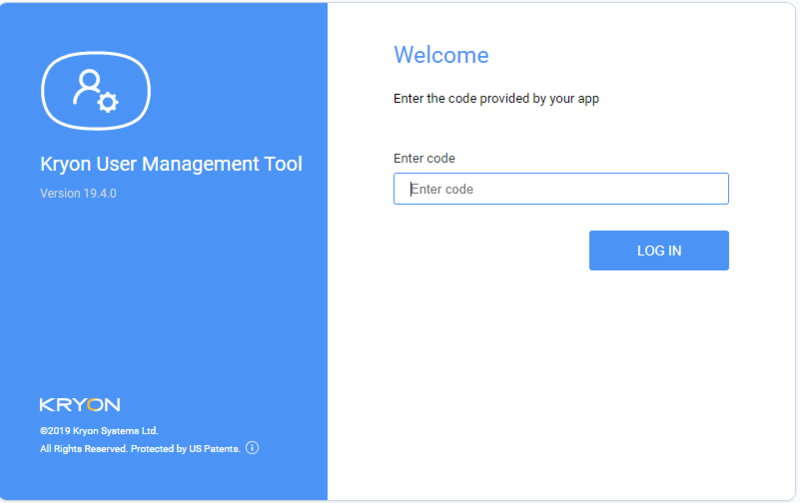
At this stage, your MFA is fully set up. Logout and then log in again, an extra form to set your MFA code appears:
-
Enter the code provided by your app.
-
Click Log In.
Congratulations - now your MFA is set up for the user!