Troubleshooting
This topic describes potential issues that you may experience and troubleshooting steps when working with
Known issue
Authentication or redirect errors when navigating to SharePoint Online
Explanation
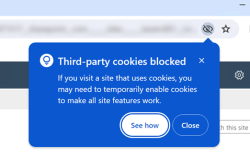
Google is rolling out changes to block third-party cookies in the Google Chrome browser. This affects Nintex K2 for SharePoint
See Prepare for the third-party cookie phaseout for more information about timelines.
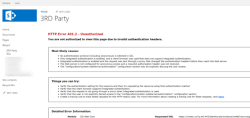
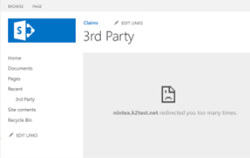
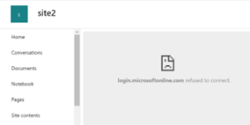
When third-party cookies are blocked, any of the following errors may occur when navigating to a Nintex K2 for SharePoint
Resolution
Configure Google Chrome to allow third-party cookies exception for Nintex K2 and SharePoint sites. Depending on whether Chrome Enterprise or mainstream version is deployed, it can either be configured manually or using Group Policies.
Follow the steps below to allow or restrict third-party cookies manually:
- On your computer, open your Google Chrome browser.
- At the top right, click More
 , and then Settings.
, and then Settings. - Click Privacy and security and then Third-party cookies.If you are part of the Tracking Protection test group, select Tracking Protection instead.
- Next to Sites allowed to use third party cookies, click Add.
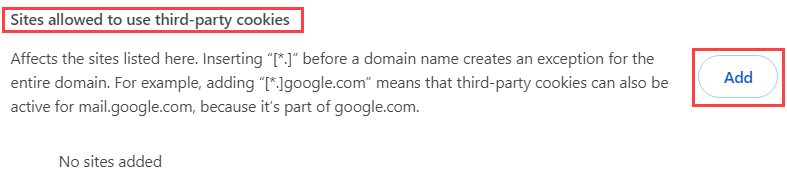
- Enter the Nintex K2 and SharePoint domains for example https://nintex.k2test.net and https://[tenant].sharepoint.com. Click Add after adding each domain.
 To create an exception for an entire domain, insert [*.] before the domain name. For example, [*.]k2test.net means that third-party cookies can also be active for nintex.k2test.net and workspace.k2test.net.
To create an exception for an entire domain, insert [*.] before the domain name. For example, [*.]k2test.net means that third-party cookies can also be active for nintex.k2test.net and workspace.k2test.net. - Your sites are now added to the sites that are allowed to use third-party cookies.
Follow the steps below to allow third-party cookies exception using Group Policies. See Allow third-party cookies from specific URLs for more information.
- Set the BlockThirdPartyCookies policy to true to restrict all third-party cookies.
- Set specific top-level sites to allow third-party cookies by adding each of them with a comma-separated third-party/top-level site pair to the CookiesAllowedForUrls policy. You can allow all third-party cookies on a particular site by using a wildcard, *, instead of a third-party URL.
For example, to allow cookies on nintex.k2test.net, add https://nintex.k2test.net,https://[tenant].sharepoint.com to the CookiesAllowedForUrls policy.
Known issue
When you get 401 unauthorized errors or you no longer have access to your SharePoint environment, your SharePoint certificate may have expired.
Errors
Some errors may include:
- "SharePoint broker methods failed due to 401 unauthorized"
- "A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. NotTimeValid: A required certificate is not within its validity period when verifying against the current system clock or the timestamp in the signed file..."
Resolution
To test if your certificate has expired do the following:
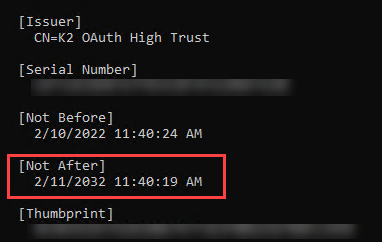
- In SharePoint Online Management Shell, run the following command:Copy
Get-SPTrustedSecurityTokenIssuer - Check the [Not after] section as shown in the image below to see if your certificate has expired.
To generate a new certificate and apply it to the environment, follow the steps below:
-
In Microsoft SQL Server Management Studio, run the script below. This script deletes three rows.
CopyDELETE FROM [K2].[HostServer].[Configuration] WHERE VariableToken like '[[]K2_SIGN%' - Truncate the app only table by running the following script:Copy
TRUNCATE TABLE [K2].[Authorization].[OAuthAppOnlyToken] - Run Configure in the Setup Manager. This generates a new certificate in the K2 database.
- Run the AppDeployment.exe in the following location "%ProgramFiles%\K2\Setup". This replaces the certificate in SharePoint.
- Confirm if the certificate has updated by running the Get-SPTrustedSecurityTokenIssuer command in SharePoint Online Management Shell again and checking the [Not after] section.