Prevent IIS Server version information disclosure through the K2 Site Server response header
Security scanning tools and penetration tests often report that the K2 Site returns the IIS Server version in the Server response header. Although this is correct, the server response header is controlled by IIS and K2 is unable to remove the server header for all responses. To address the risk of the IIS Server's version being disclosed, IIS server administrators should configure a URL Rewrite rule that will remove or change the value.
Use the following steps to configure a URL Rewrite rule:
- Download and install the IIS URL Rewrite add-on
from:
https://www.iis.net/downloads/microsoft/url-rewrite - Open IIS and click on the K2 Site node.
- Double-click on the URL Rewrite icon.
- In the Actions panel on the right-hand side of the screen, click View Server Variables....
- In the Actions panel, click Add... and enter RESPONSE_SERVER in the Add Server Variable dialog.
- In the Actions panel, click Back to rules to return to URL Rewrite.
- In the Actions panel, click Add Rule(s)....
- Select Blank Rule Under Outbound rules and click OK.
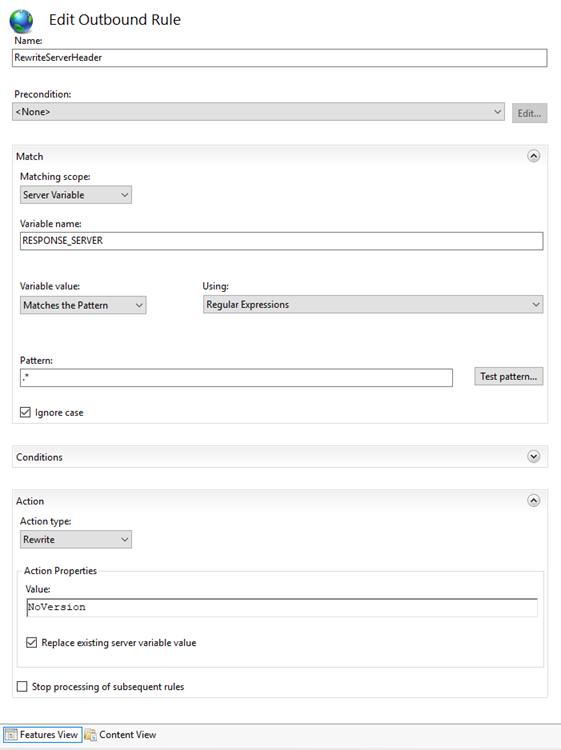
- Configure the rule as in this image:
- In the Actions panel, click Apply to save the changes.
This completes the rule creation, and there is no need to perform an iis_reset.