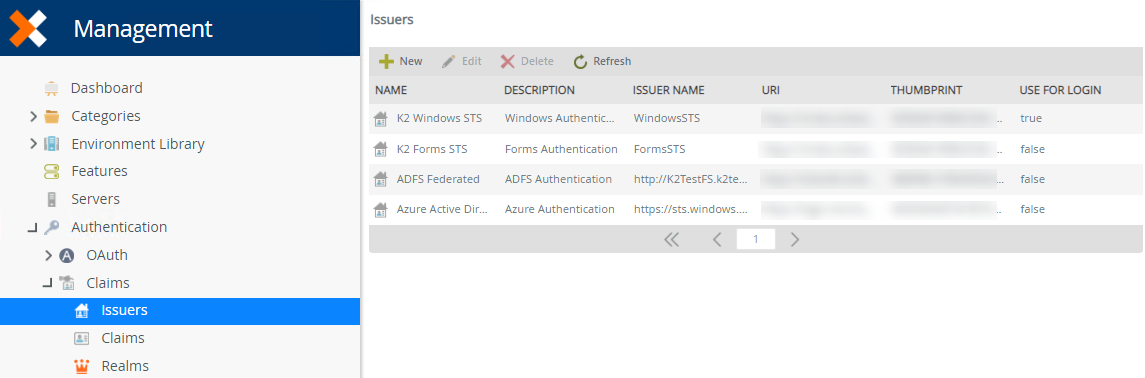
Issuers
The Issuers node is used to view and administer configuration information about each claims issuer (such as SharePoint, ADFS and Azure Active Directory) that the server trusts.
Follow these steps to add a claims issuer:
- Click New from the Issuers section.
- Enter values in the fields for the new claim issuer. Refer to the table below the image for guidance.
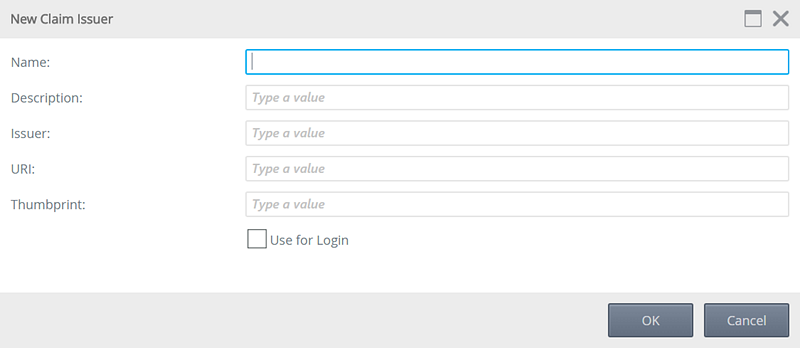
Field Description Name The name of the claim issuer. Description The description of the claim issuer. Issuer Name The issuer, which can be in a URI format or simply a name. URI The URI of the issuer. Thumbprint The thumbprint of the issuer. Use for Login Set this to true if you want this issuer to be displayed as an available login method on the Designer login page. - Click OK.
Follow these steps to edit a claims issuer:
-
Select the issuer you want to edit. The Edit button becomes available.
- Click Edit.
- Change the values that you want to edit, and then click OK to apply the chnages..
Follow these steps to delete a claims issuer:
-
Select the issuer you want to delete. The Delete button becomes available.
- Click Delete.
- Click OK on the confirmation dialog to confirm that you want to delete the Issuer.
The Refresh button refreshes the claims issuers list after changes have been applied.
- When integrating Azure Active Directory with the product for login, we do not automatically refresh the token for you, we send the user back to the Issuer to re-authenticate. It also depends on how the Issuer (Azure Active Directory) is configured, to either refresh your token or prompt for a login again. The product does not use OAuth for login and instead uses the Issuer for authentication. As a result, there is no refresh token or refresh endpoint involved and the product does not have an automatic token refresh feature built in for logins. The product also do not control the token lifetime. The Issuer (Azure Active Directory) manages the token lifetime. For information on how to configure this, you need to consult the documentation for your Identity Provider. Implementing an auto-refresh mechanism for maintaining "idle" users' sessions poses a potential security risk, as continuously refreshing tokens can extend a session indefinitely. This increases the chances of an attacker hijacking a session, especially if a user's credentials or session data are compromised. See Access tokens in the Microsoft identity platform for more information.