Credentials Vault
The Credentials Vault is a module within the Nintex RPA Platform used to manage login credentials for systems that Nintex robots need to access when performing automation tasks. Usernames and passwords are stored securely using data encryption.
The Credentials Vault enables automation developers to utilize the required credentials for any process without hard coding specific usernames and passwords into automation scripts and without exposing credentials to the developers.
Moreover, the Credentials Vault allows for the management of password updates in a single, centralized location – eliminating the need to update a changed password in every workflow in which it is used.
Architecture
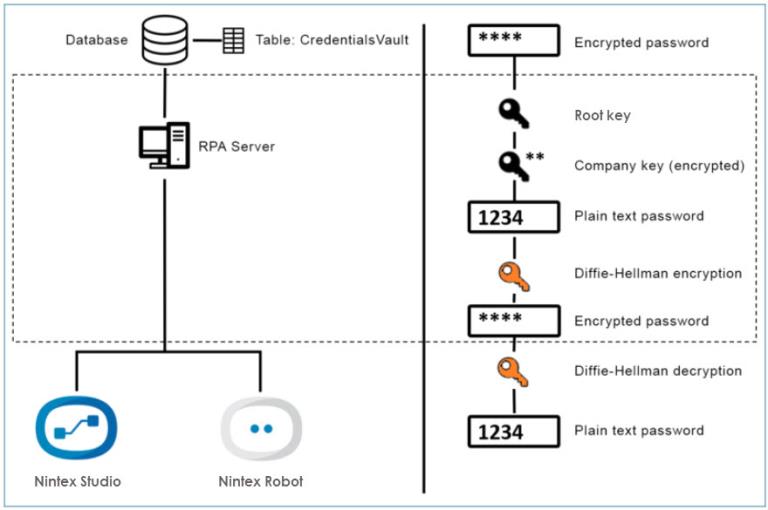
Credentials Vault data is saved in an encrypted format in the Nintex database, utilizing a 2-phase encryption process.
The AES encryption algorithm is used to encrypt/decrypt the data saved in the database, using the 256-bit key, CBC cipher mode.
A per-company encryption key is auto-generated on the server side upon each new company creation.
Upon each Credentials Vault data exchange between client and server, credentials are encrypted using Diffie-Hellman key exchange cryptographic protocol that allows two parties with no prior knowledge of each other to jointly establish a shared secret key, which is unique for each logged-in Nintex use.
A third party (potential attacker) intercepting the public keys but lacking knowledge of either private key cannot generate the shared secret key. Therefore, data encrypted with the resulting shared secret key is secure while in transit.
Diffie-Hellman key exchange usage
The shared secret key is unique and randomly generated by the Diffie-Hellman (DH) algorithm every time a particular user logs in to the system, and it is deleted when the user logs out.
The DH algorithm begins with a large prime (P) and a generator (G). These don't have to be secret and may be transmitted over an insecure channel.
The Credentials Vault utilizes the Chilkat DH component. This third-party library provides the ability to use known "safe" primes, as well as a method to generate new safe primes. (Generating new safe primes is a time-consuming, CPU-intensive task, and is normally handled offline.)
Credentials Vault uses Chilkat DH component’s 8 pre-chosen safe primes.
-
Each side begins by generating an E value
-
Bob (Nintex server) generates a random E (which has the mathematical properties required for DH)
-
Alice (Nintex client) does the same
-
-
The E values are sent over the secured (optional) channel
-
Bob sends his E to Alice, and Alice sends her E to Bob
-
-
Each side computes the shared secret key K
-
Bob computes the shared secret from Alice's E
-
Alice computes the shared secret from Bob's E
-
The shared secret keys of both sides must be identical, otherwise a man-in-the-middle (MITM) attack could result.
/Security Overview_4.png)
Credentials Vault master password
Bcrypt, a password hashing function, is used to protect the Credentials Vault master password. The bcrypt cost factor (work factor, number of rounds of hashing) can be set to any value from 4 to 31. The Credentials Vault uses a value of 10.
Upon each client request to access the Credentials Vault, the server computes a hash for the master password and encrypts it using the Diffie-Hellman algorithm.
Upon receipt, the receiver (Studio/Nintex robot) computes a bcrypt hash value (the user’s typed phrase) and compares the computed value to the received hash. If the two values are the same, the password authenticity is valid.
Hash output will be different for each use because the bcrypt method automatically generates a random salt.