K2 for SharePoint Architecture
K2 for SharePoint is an App that runs in the Provider-Hosted App model. This means that all artifacts execute on the K2 server and K2 only integrates with SharePoint through APIs that SharePoint exposes. As a result, there is a very minimal footprint of K2-installed items on the SharePoint Servers, and the majority of all execution happens on the K2 environment. Most of the K2 user interface elements that appear in SharePoint are actually iFrames that point back to the K2 environment.
K2 uses SmartObjects to integrate back to the SharePoint site, and uses the same technology to expose other systems, like SQL and AD, as SmartObjects. In turn, external applications can use SmartObjects to interact with SharePoint through K2.
K2 makes use of Remote Event Receivers (RERs) to listen for events that occur on the SharePoint environment. For example, if you were to configure a workflow to start when an item is added to a SharePoint List, K2 will register a Remote Event Receiver for that list when the workflow is deployed. When an item is added to the list, the RER will instruct K2 to start the workflow.
For examples of environment topologies when using K2 for SharePoint, see SharePoint 2013, SharePoint 2016 and SharePoint Online.
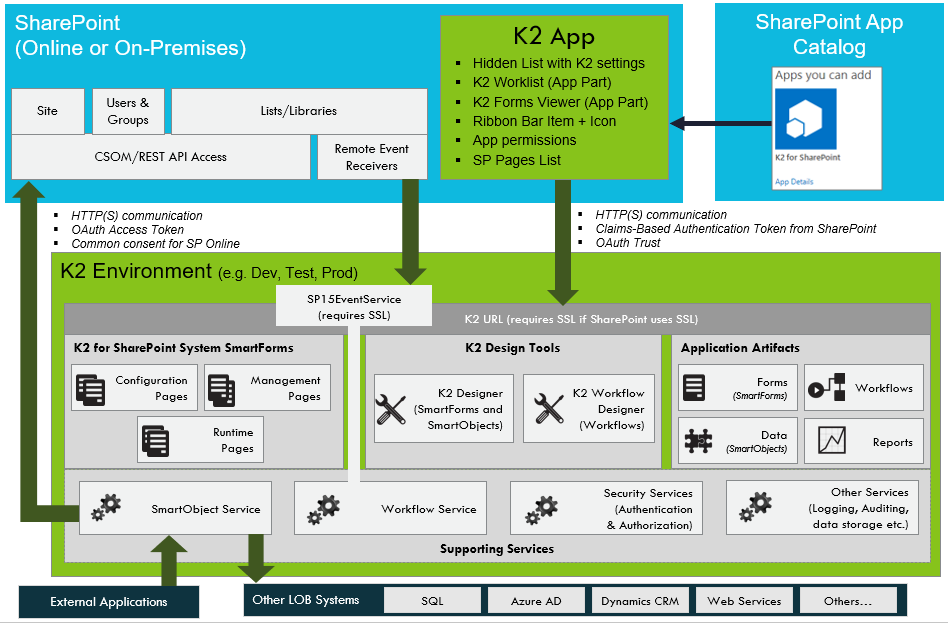
The diagram below conceptually illustrates the integration between K2 and SharePoint. Notice that the K2 App resides in the App Catalog, from where it is deployed to a SharePoint Site Collection. This creates some artifacts on the targeted SharePoint Site Collection, but all execution and operation occurs in the connected K2 environment. K2 in turn, uses K2 SmartObjects to interact with SharePoint items such as Lists, Libraries, Sites and Groups.
Conceptual Diagram: SharePoint and K2 for SharePoint integration
Authentication
The authentication from K2 to SharePoint uses Claims-Based Authentication (CBA) and OAuth. OAuth is configured when you register the App in a SharePoint site. Under the covers, K2 and SharePoint would usually use the same authentication mechanism and therefore user credentials are seamlessly passed from one system to the other. Since CBA is used, Kerberos and Pass-Through Authentication are no longer required as was the case with many SharePoint 2010 and earlier environments.
K2 is a relying party (along with SharePoint, online or on-premises) that trusts SAML2.0 Claims tokens that were issued by a trusted claims issuer (also known as a Secure Token Service or STS), such as Access Control Service for Azure Active Directory or Active Directory Federation Service (ADFS) for Active Directory, and those Claims Tokens were retrieved from a Claims Provider (also known as an Identity Provider), which is most often Azure Active Directory or Active Directory.
- For more information on permissions and rights used with K2 for SharePoint see Permissions and Rights.
- For more information on how authentication and authorization work in K2, see Authentication and Authorization in K2.