Service Instances Security
The Service Instances Security node is used to define design-time rules for service instances and service types to provide extra security to SmartObjects and increased granularity of control for the management of service types and service instances. This allows you as a member of the security administrators role to control who is allowed to manage service types and service instances and who can consume service instances within the design of their SmartObjects. The Create right is required to create a new Service Instance and the View right is required to use a Service Instance in a SmartObject. For more information see the Authorization Overview topic.
Consider the following when assigning rights in the different nodes in Management:
- Service Instances Security - Serves as the root level from where rights are inherited and is useful where rights must apply across all service types and service instances.
- Service Types - Inherits rights from the service instances security level.
- Service Instances - Inherits rights from its associated service type.
Inheritance can be broken on both the service type and service instance level by going into the respective object's UI in Management, selecting it from the list and clicking Security at the top. See Considerations and Best practices for managing security permissions for considerations and best practices when assigning rights and managing permissions.
While it is possible to give users and groups rights directly on service types and service instances, you should preferably create roles, and then assign rights to roles, because this will make subsequent security administration easier.

| Service instances security level rights | Description |
|---|---|
| View | View and use items at design time in K2 Management and K2 Designer |
| Create | Create service types and service instances in K2 Management |
| Modify | Update items in K2 Management |
| Delete | Delete items in K2 Management |
| Security | As the creator of service types and service instances, you can assign Security rights to those items, which allow others to manage the item's security, including assigning View, Create, Modify, Delete and Security rights |
Follow these steps to add rights on the service instances security level:
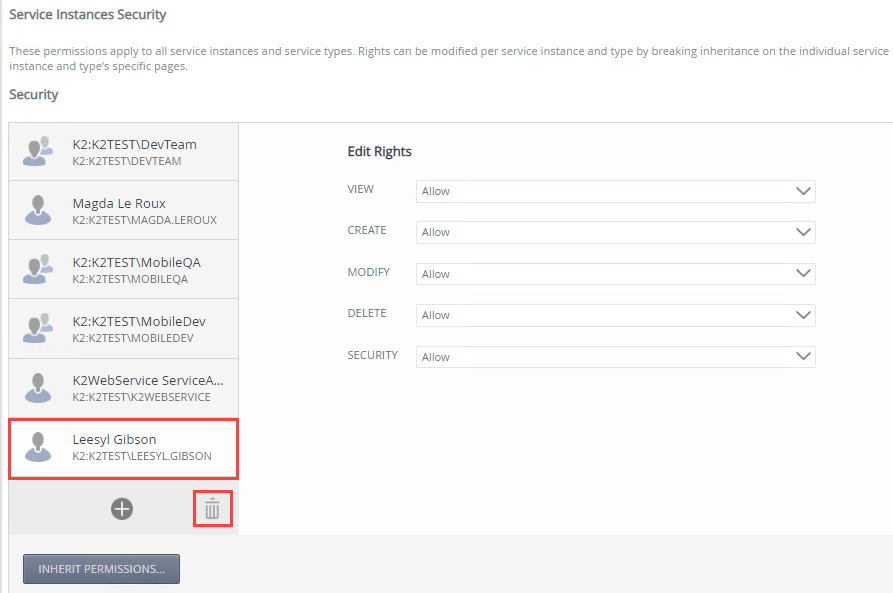
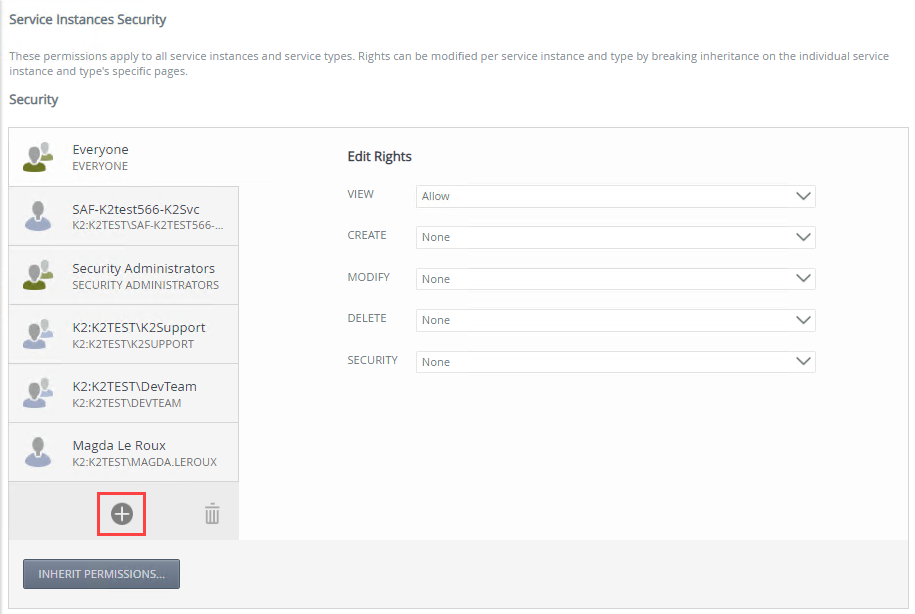
- Add a user, group, or role by clicking the Add button.
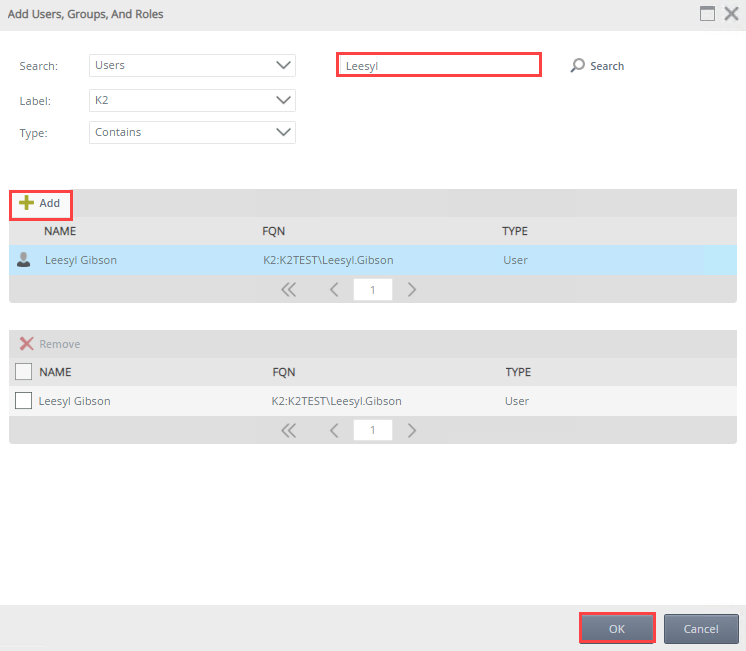
- On the Add Users, Groups, And Roles page search and add a user, group, or role. Click OK.
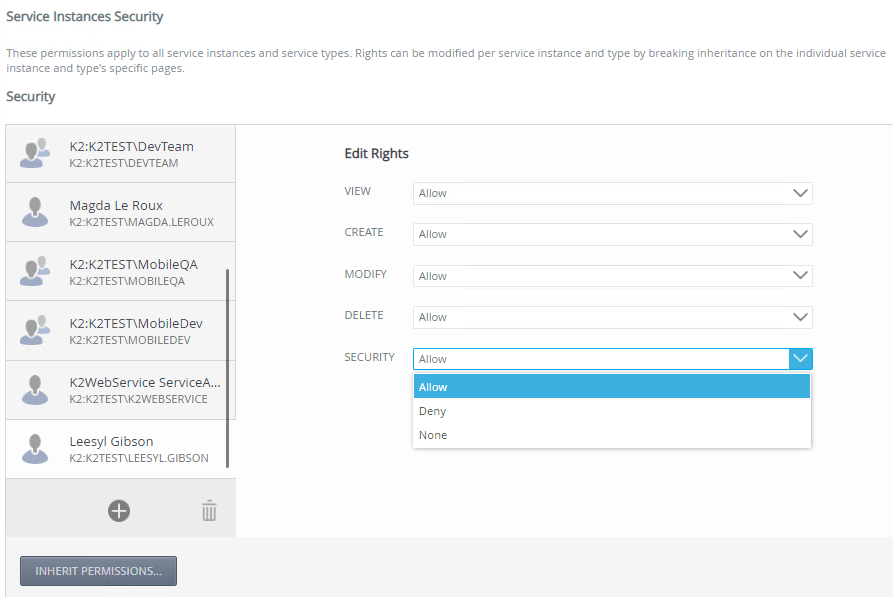
- Specify the user, group, or role's View, Create, Modify, Delete, and Security rights.
- Add more users, groups, and roles if necessary.When specifying users, groups, and roles, the Everyone role is added during installation, providing all authenticated users, the ability to view service types and service instances. Best practice would be to modify the Everyone role's view rights to None on the Service Instances Security level, and grant permissions to users, groups, and roles according to your organizations requirement on the service type.
Follow these steps to edit service instances security level rights:
- Select a user, group, or role and edit the rights.
Follow these steps to remove edit service instances security level rights:
- Select a required user, group, or role and click Remove.