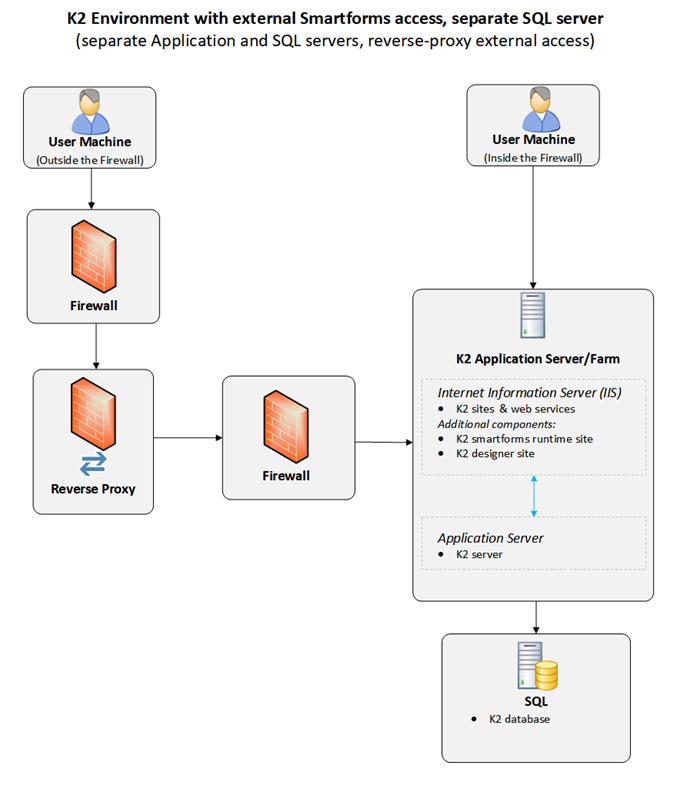
Reverse Proxy
One way to expose your K2 servers to internet users is to use a reverse proxy to retrieve content from K2 servers inside your organization's network. In other words, your K2 server is located behind a firewall and the reverse proxy server accesses the K2 server on behalf of the internet users.
Reverse proxy (all K2 servers on intranet)
Considerations
A reverse proxy is essentially a rule that maps an external URL to an internal web server URL.
- Map the external URL to a different internal URL so that the internal server name is not exposed.
- Reverse proxies use the SSL web port (TCP 443).
- Expose the following virtual folders in the K2 sites:
- Autodiscover (optional but recommended – used to discover the best endpoint to connect to)
- Identity (required, used for authentication)
- K2API (optional, used by K2 mobile devices to connect to K2)
- Runtime (required, used to access the SmartForms runtime site)
- SP15EventService (optional, depending on your requirement, used to allow SharePoint to trigger workflows in K2)
- ViewFlow (optional, used to render the ViewFlow report)
- K2 Workspace (Deskop) (optional, exposes the K2 Workspace (Deskop) site)
- K2Services (Deprecated and optional, used by K2 Mobile 1.0)
- Any other application folders used by custom apps
- K2 server and user segment must be able to reach the following public URLs using SSL (TCP 443) for external integration and authentication. This is also needed for the K2 server to upload and access SharePoint documents and lists:
- https://trust.k2.com
- https://login.windows.net
- https://login.microsoftonline.com
- {Your SharePoint Online URL}
- For some reverse proxies, you must install the same SSL certificate as you have on the web server and select it in the rule.