Configuring the K2 LDAP User Manager
Use this information to configure the K2 LDAP user managers settings. You can edit the sample script for your environment and use it to configure your LDAP user manager.
There are many settings due to the nature of LDAP and its various implementations. Each user directory implements different capabilities and queries for one LDAP provider may not work for another. Once you understand these settings, you can configure the LDAP user manager to work with your specific LDAP identity store.
Sample SecurityLabels SQL Script
The following example is for the fictitious Denallix.com domain. You must change some of the values below to match your environment. The downloadable script file includes this XML and running the script inserts it into the SecurityLabels table of the K2 database.
Sample SecurityLabels SQL Script
-- K2 LDAP User Manager (Forms - Setup).sql
-- sample script for creating a K2 LDAP user manager that uses the SourceCode.Security.Providers.LdapProvider.Forms.Ldap provider
-- DECLARATIONS
DECLARE @SecurityLabelName NVARCHAR(20) = 'K2FORMS'; --Update as needed
DECLARE @XmlConfig XML =
'<AuthInit>
<LdapConnection LdapServer="dlx.denallix.com" LdapServerPort="389" LdapSsl="false" LdapAuthTypeConnect="Negotiate" LdapAuthTypeAuthenticateUser="Negotiate" LdapResolveAuthenticationUserToDistinguishedName="false" LdapAutoBind="false" LdapScope="Subtree" LdapConnectIntegrated="true" LdapConnectUserName="" LdapConnectUserPassword="" LdapTimeout="0" LdapProtocolVersion="3" LdapServerCertificatePath="" />
<LdapUserBaseObject>OU=FORMS,DC=QA,DC=COM</LdapUserBaseObject>
<LdapUserSearchFormatString>userPrincipalName={0}</LdapUserSearchFormatString>
<LdapUserGroupSearchFormatString />
<LdapUserAttributes>
<K2LdapMapping K2Name="ID" LdapName="userPrincipalName" ObjectType="System.String" />
<K2LdapMapping K2Name="Name" LdapName="userPrincipalName" ObjectType="System.String" />
<K2LdapMapping K2Name="Description" Multiline="true" LdapName="description" ObjectType="System.String" />
<K2LdapMapping K2Name="Email" LdapName="mail" ObjectType="System.String" />
<K2LdapMapping K2Name="DistinguishedName" LdapName="distinguishedName" ObjectType="System.String" />
<K2LdapMapping K2Name="ObjectSID" FullOnly="true" LdapName="objectSID" ObjectType="System.String" />
<K2LdapMapping K2Name="CommonName" LdapName="cn" ObjectType="System.String" />
<K2LdapMapping K2Name="UserPrincipalName" LdapName="userPrincipalName" ObjectType="System.String" />
<K2LdapMapping K2Name="Manager" FullOnly="true" LdapName="manager" ObjectType="System.String" SearchQuery="(&(objectClass=Person)(objectCategory=User))" SearchResultProperty="userPrincipalName" />
<K2LdapMapping K2Name="SipAccount" LdapName="msRTCSIP-PrimaryUserAddress" ObjectType="System.String" />
<K2LdapMapping K2Name="DisplayName" LdapName="displayName" ObjectType="System.String" />
<K2LdapMapping K2Name="TelephoneNumber" LdapName="telephoneNumber" ObjectType="System.String" />
<K2LdapMapping K2Name="Mobile" LdapName="mobile" ObjectType="System.String" />
<K2LdapMapping K2Name="HomePage" LdapName="wWWHomePage" ObjectType="System.String" />
<K2LdapMapping K2Name="FaxNumber" LdapName="facsimileTelephoneNumber" ObjectType="System.String" />
<K2LdapMapping K2Name="HomePhone" LdapName="homePhone" ObjectType="System.String" />
<K2LdapMapping K2Name="IPPhone" LdapName="ipPhone" ObjectType="System.String" />
<K2LdapMapping K2Name="StreetAddress" LdapName="streetAddress" ObjectType="System.String" />
<K2LdapMapping K2Name="City" LdapName="l" ObjectType="System.String" />
<K2LdapMapping K2Name="Country" LdapName="c" ObjectType="System.String" />
<K2LdapMapping K2Name="State" LdapName="st" ObjectType="System.String" />
<K2LdapMapping K2Name="Title" LdapName="title" ObjectType="System.String" />
<K2LdapMapping K2Name="Department" LdapName="department" ObjectType="System.String" />
<K2LdapMapping K2Name="Company" LdapName="company" ObjectType="System.String" />
<K2LdapMapping K2Name="Office" LdapName="physicalDeliveryOfficeName" ObjectType="System.String" />
<K2LdapMapping K2Name="ManagedUsers" FullOnly="true" LdapName="managedUsers" SearchQuery="(&(objectClass=Person)(objectCategory=User))" SearchResultProperty="userPrincipalName" ObjectType="System.Collections.ArrayList" />
<K2LdapMapping K2Name="Groups" FullOnly="true" LdapName="memberOf" SearchQuery="(objectCategory=Group)" SearchResultProperty="userPrincipalName" ObjectType="System.Collections.ArrayList" />
</LdapUserAttributes>
<LdapGroupBaseObject>OU=FORMS,DC=QA,DC=COM</LdapGroupBaseObject>
<LdapGroupSearchFormatString>userPrincipalName={0}</LdapGroupSearchFormatString>
<LdapGroupMemberSearchFormatString />
<LdapGroupAttributes>
<K2LdapMapping K2Name="ID" LdapName="userPrincipalName" ObjectType="System.String" />
<K2LdapMapping K2Name="Name" LdapName="cn" ObjectType="System.String" />
<K2LdapMapping K2Name="Description" Multiline="true" LdapName="description" ObjectType="System.String" />
<K2LdapMapping K2Name="Email" LdapName="mail" ObjectType="System.String" />
<K2LdapMapping K2Name="DistinguishedName" LdapName="distinguishedName" FullOnly="true" ObjectType="System.String" />
<K2LdapMapping K2Name="ObjectSID" LdapName="objectSID" FullOnly="true" ObjectType="System.String" />
<K2LdapMapping K2Name="Member" LdapName="member" FullOnly="true" SearchQuery="(&(objectClass=Person)(objectCategory=User))" SearchResultProperty="userPrincipalName" ObjectType="System.Collections.ArrayList" />
</LdapGroupAttributes>
</AuthInit>' -- XML configuration for the LDAP provider, see K2 Help for more information on configuration values
DECLARE @SecurityLabelID UNIQUEIDENTIFIER = NEWID();
DECLARE @AuthSecurityProviderID UNIQUEIDENTIFIER = NEWID(); --Assigning new GUID
DECLARE @AuthInit XML = @XmlConfig;
DECLARE @RoleSecurityProviderID UNIQUEIDENTIFIER = @AuthSecurityProviderID;
DECLARE @RoleInit XML = @XmlConfig;
DECLARE @DefaultLabel BIT = NULL; --1 = true, NULL and 0 = false
DECLARE @ProviderClassName NVARCHAR(200) = 'SourceCode.Security.Providers.LdapProvider.Forms.Ldap';
DECLARE @SPProviderID UNIQUEIDENTIFIER;
-- UPDATE TABLES
DELETE FROM [k2].[HostServer].[SecurityProvider] WHERE ProviderClassName = @ProviderClassName;
DELETE FROM [k2].[HostServer].[SecurityLabel] WHERE SecurityLabelName = @SecurityLabelName;
INSERT INTO [k2].[HostServer].[SecurityProvider] VALUES (@AuthSecurityProviderID, @ProviderClassName);
INSERT INTO [k2].[HostServer].[SecurityLabel] VALUES (@SecurityLabelID, @SecurityLabelName, @AuthSecurityProviderID, @AuthInit, @RoleSecurityProviderID, @RoleInit, @DefaultLabel);
SELECT @SPProviderID = [SecurityProviderId] FROM [k2].[HostServer].[SecurityProvider] WHERE [ProviderClassName] = N'SourceCode.Security.Providers.SharePoint.SharePointProvider';
IF NOT EXISTS (SELECT 1 FROM [k2].[HostServer].[GroupProvider] WHERE [SecurityLabelID] = @SecurityLabelID)
BEGIN
INSERT INTO [k2].[HostServer].[GroupProvider]
(
[GroupProviderID]
,[SecurityLabelID]
,[SecurityProviderID]
,[Name]
,[Init]
)
VALUES
(
NEWID()
,@SecurityLabelID
,@SPProviderID
,'*'
,'<init><label name="SP" /></init>'
)
END| LDAP Setting | Description |
|---|---|
| LdapConnection |
|
| LdapUserSearchFormatString | This is the LDAP query used to search for users. It should include a placeholder “{0}” for where to insert the user's ID.
As this is in XML, escape any reserved XML characters (such as the ampersand character &). For example:
(&(objectClass=Person)(objectCategory=User)(samAccountName={0}) |
| LdapUserGroupSearchFormatString | This is the LDAP query used to search for users that belong to a specific group. It should include a placeholder “{0}” for where to insert the group’s ID. Do not include wildcards as these get handled automatically. As this is in XML, escape any reserved XML characters (such as the ampersand character &). For example, to return users from this specific group and all nested groups:
(memberOf :1.2.840.113556.1.4.1941:={0}) For more information see Search Filter Syntax (MSDN). |
| LdapGroupSearchFormatString | This is the LDAP query used to search for groups. It should include a placeholder “{0}” for where to insert the user’s ID. Do not include wildcards as these get handled automatically. As this is in XML, escape any reserved XML characters (such as the ampersand character &). For example:
(&(objectCategory=Group)(samAccountName={0})) |
| LdapGroupMemberSearchFormatString | This is the LDAP query used to search for groups of which the user is a member. It should include a placeholder “{0}” for where to insert the user’s ID. Do not include wildcards as these get handled automatically. As this is in XML, escape any reserved XML characters (such as the ampersand character &). For example, to return groups and all nested groups of which the user is a member: (member:1.2.840.113556.1.4.1941:={0}) For more information see Search Filter Syntax (MSDN). |
| LdapUserBaseObject | This is the LDAP base object from which all user searches are made. Make sure that this correlates correctly to your LdapScope setting above. . For example:
dc=denallix,dc=com |
| LdapGroupBaseObject | This is the LDAP base object from which all group searches are made. Make sure that this correlates correctly to your LdapScope setting above. For example:
dc=denallix,dc=com |
| LdapUserAttributes | The following is the set of attributes that are used in your directory. The available settings for each attribute are:
|
| LdapGroupAttributes | As above, except these attributes would be the ones returned for groups. |
Register the LDAP User Manager
To register the LDAP User Manager, modify the SecurityLabels table in the database. This table stores the security label, security provider, and authorization/role initialization data for the user manager. The K2 User Manager sample scripts available for download allow you to add or remove a LDAP user manager. Make sure to edit the scripts to fit your configuration before executing them. Follow the steps below to add the LDAP user manager.
- Download and extract the K2 User Manager sample scripts.
- Open the K2 LDAP User Manager (Forms - Setup).sql script and edit it for your environment.
- Execute the K2 LDAP User Manager (Forms - Setup).sql script from Microsoft SQL Server Management Studio against the K2 database.
- You need to update of the existing user cache if you change user managers configuration. Execute this SQL command against the K2 database.
Copy
Update of the existing user cache
UPDATE [K2].[Identity].[Identity]
SET [ExpireOn] = GETDATE()
,[Resolved] = 0
,[ContainersResolved] = 0
,[ContainersExpireOn] = GETDATE()
,[MembersResolved] = 0
,[MembersExpireOn] = GETDATE()
GO
- Restart the K2 Server service.
Create, Link and Map the Issuer to the Security Label
-
Follow the user guide steps to set up a New Claim Mapping.
-
Use the settings in the table below when setting your New Claim Mapping.
Items Setting Security Lab K2FORMS Issuer K2 Forms STS Claim Type Info Checked Name Identity Issuer User Token Identifier Group Took Identifier Identity Provider Original Issuer FormsSTS Claim Type http://schemas.microsoft.com/identity/claims/idenityprovider Claim Value FormsSTS Identity Original Issuer FormsSTS Claim Type http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name Claim Value Security Label Original Issuer FormsSTS Claim Type http://schemas.k2.com/identity/claims/securitylabelname Claim Value 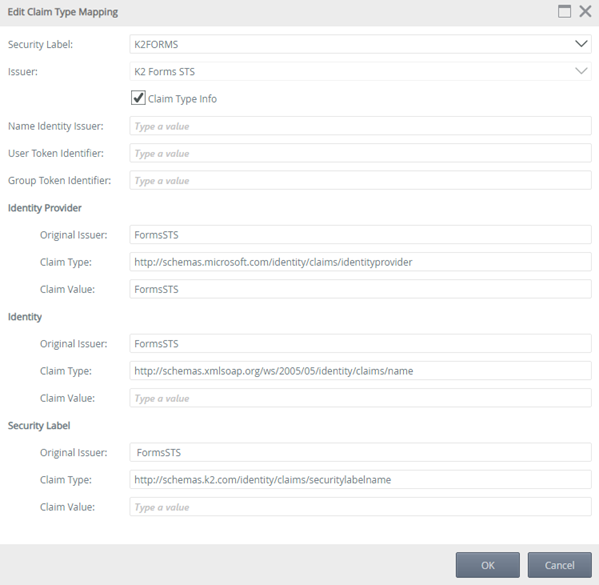
-
Edit each Realm to add the K2 Forms STS to each Realm, the final result is shown below: