Security and Authentication (On-Prem and Online)
Important: Be sure to log on to the target machine with local System Administrator rights before beginning the installation. Also see the Installation of K2 for SharePoint in the App Catalog (SharePoint 2013) section of the Required Permissions topic.
K2 for SharePoint Online requires SSL for querying and updating data, and also for passing OAuth tokens. These bindings need to be set up with the installation of K2 or, if installing K2 for SharePoint on an existing K2 environment, the K2 sites need to be reconfigured for HTTPS support. SSL-enabled sites are installed by default using a K2 self-signed certificate unless you specify your own certificate, which is recommended.
If SharePoint is configured for SSL then K2 also needs to be configured for SSL. The K2 for SharePoint Registration Wizard prevents you from proceeding if a mismatch is detected between the SSL settings for SharePoint and K2.
Supported Scheme Configurations
The following table outlines the supported non-SSL and SSL based communication configurations supported by K2:
| SharePoint Scheme | K2 Designer Scheme | Supported |
|---|---|---|
| HTTP | HTTP | Yes - Workaround for SharePoint On-Premises only, SharePoint Online requires SSL |
| HTTP | HTTPS | No |
| HTTPS | HTTP | No |
| HTTPS | HTTPS | Yes |
- Run the K2 Setup Manager and uncheck the ‘Use previously configured values’ check-box.
- On the K2 Site Configuration page in the Resolve IIS Bindings dialog (clicking the Bindings button open this), select the SSL binding and set it as the default environment field:
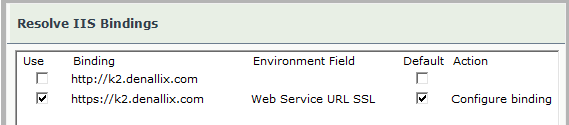
- On completion of the upgrade:
- The STS URI’s are configured to use the SSL binding.
- A Claim Realm is added for ViewFlow on the SSL binding.
- The Realm in the ViewFlow web.config points to the Realm for the SSL binding.
- Run the K2 Setup Manager.
- On the K2 Designer Web Site and SmartForms Runtime Site pages, in the Resolve IIS Bindings dialog, select the same SSL binding, uncheck the checkbox to use the HTTP binding, and set the SSL binding as the default environment fields.
The claims configuration for the Designer and Runtime are now properly configured to use the SSL binding and realms are added for these URLs like they are for ViewFlow.
Configuring the K2 environment to run with matching non SSL-based connections requires running SharePoint PowerShell commands to modify the default settings in order to enable SharePoint apps to exchange metadata over a non-secure connection. Before continuing with these steps, read the TechNet article Configure server-to-server authentication between SharePoint 2013 farms to familiarize yourself with the implications of these actions.
- The following SharePoint PowerShell commands must be run on the SharePoint Web Front Ends(WFEs):# Dev Only - Disable HTTPS requirement
$stsc = Get-SPSecurityTokenServiceConfig
$stsc.AllowMetadataOverHttp = $true
$stsc.AllowOAuthOverHttp= $true
$stsc.Update() - Confirm that the default runtime and designer environment library variables are non-SSL using the K2 Management site.
- The K2 installer and the K2 for SharePoint registration wizard may now be used to complete the non-SSL installation.
Carefully read these sections to determine where and when you need K2 web sites and endpoints to be signed by a valid certificate and available on the internet.
Certificate Requirements
K2 strongly recommends using a certificate issued by a Certificate Authority (CA) that is trusted by Windows.
K2 recommends the same certificate be used for all K2 web sites and endpoints.
K2 generates a self-signed certificate for web sites selected during installation that do not already have certificates, but this approach should only be used in Development and Test/QA environments.
SharePoint Online requires that the certificate associated with SharePoint remote event receiver endpoint in K2 (https://{K2WebSite}/SP15EventService/RemoteEventService.svc) be issued by a CA that is trusted by Windows. If a root authority certificate is not used for the Remote Event Service, SharePoint Online will not make the event call to K2.
You should know your actual requirements when choosing an SSL certificate. For example, a single wildcard certificate for *.domain.com, will work for these domains:
- runtime.domain.com
- designer.domain.com
- apps.domain.com
However, because the wildcard only covers one level of subdomains, these domains would not be valid for the same *.domain.com certificate:
- data.runtime.domain.com
- forms.designer.domain.com
- app-123356.apps.domain.com
Internet Requirements
The K2 web sites and SharePoint remote event receiver endpoints may need to be accessible to the internet depending on your scenario.
- User Browser (Intranet Only) – K2 web sites do not need to be internet-accessible when the user is accessing those sites from within the company intranet or via VPN.
- User Browser (Remote Access) - K2 web sites need to be internet-accessible when the user is accessing these sites from outside the company intranet or VPN.
- SharePoint Online Remote Event Receivers – The SharePoint remote event receiver endpoint in K2 (https://{K2WebSite}/SP15EventService/RemoteEventService.svc) must be internet-accessible when building event-based processes for SharePoint Online.