Azure Active Directory Management (Read/Write to Azure Active Directory)
K2 Cloud environments require integration with your Azure Active Directory and, in turn, consent to an app. K2 Cloud uses either the K2 for Office 365 app (for SharePoint Online integration) or the Azure Active Directory for K2 app (if SharePoint Online integration is not planned). Both apps request only read permissions to your Azure Active Directory, not write. If you need to build solutions that write data to Azure Active Directory, you must consent the write permission using the Azure Active Directory Management for K2 app. Use this topic to reconfigure your existing Azure Active Directory service instance and consent to the Azure Active Directory Management for K2 app requested read and write permissions.
- Confirm the AADMGMT OAuth resource exists
- Rebind the Azure Active Directory service instance to use the AADMGMT OAuth resource
- Consent to the Azure Active Directory Management for K2 app in your Azure Active Directory tenant
Background
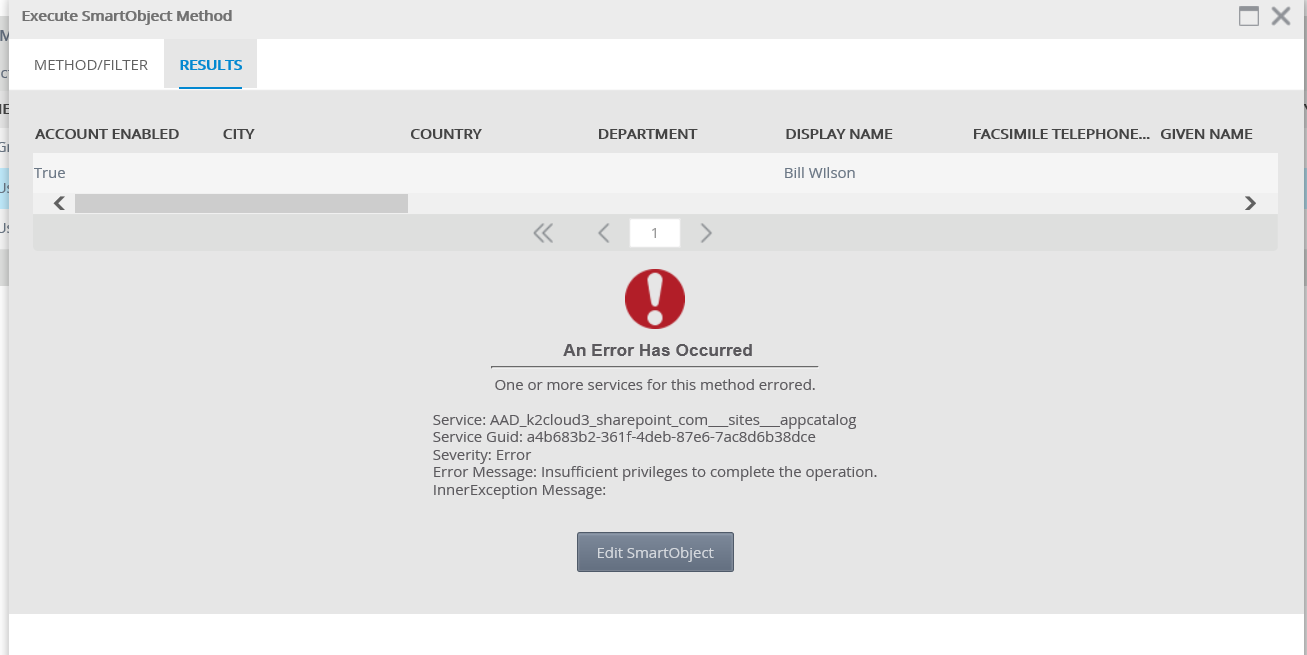
When the Azure Active Directory service instance is configured against the K2 for Office 365 app, all SmartObject methods are exposed even though the underlying OAuth tokens and app do not expose Azure Active Directory editing permissions by default. This means that it is possible to build a solution that attempts to use these edit methods, but those calls fail. Below is an example of the error received if you use an Azure Active Directory-based SmartObject method that attempts to write data. In this example, the Update method of the User SmartObject is called. Notice in the error the message "Insufficient privileges to complete the operation."
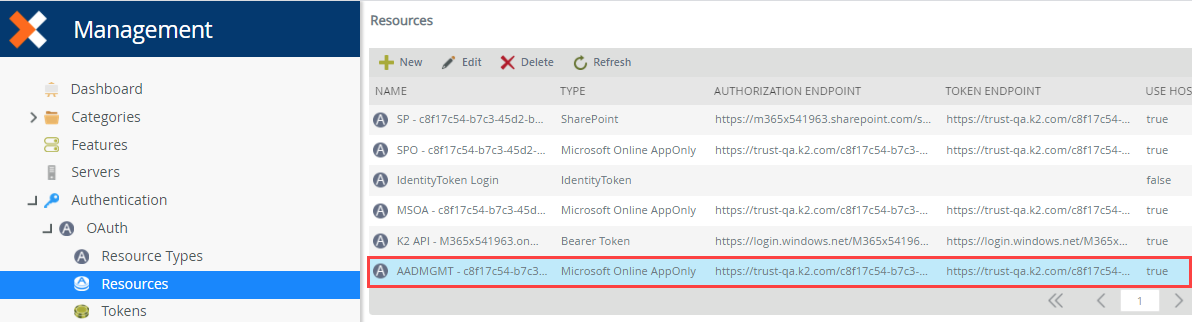
With K2 Cloud, the same resource called AADMGMT is automatically configured with your Azure Active Directory tenant details as well as the parameters necessary to work with the Azure Active Directory Management for K2 app. You can find this resource using the Authentication > OAuth > Resources page in Management.
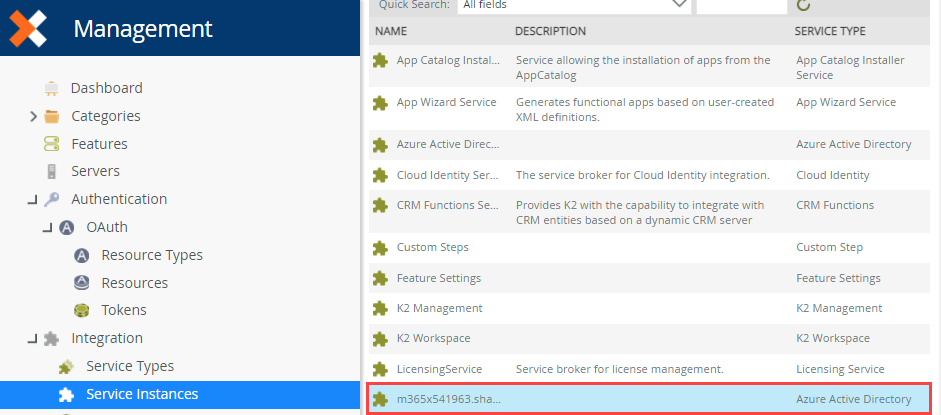
- Find your Azure Active Directory service instance using the Integration > Service Instances page in Management. It's service type is Azure Active Directory.
- Select the Azure Active Directory service instance and click Edit.
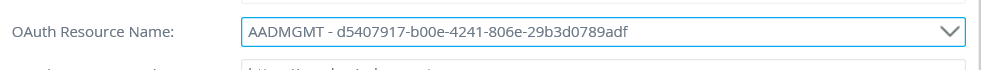
- In the OAuth Resource Name drop down list, select the resource that begins with AADMGMT and followed by your tenant ID.
- After changing the OAuth resource and clicking OK, the following message appears:
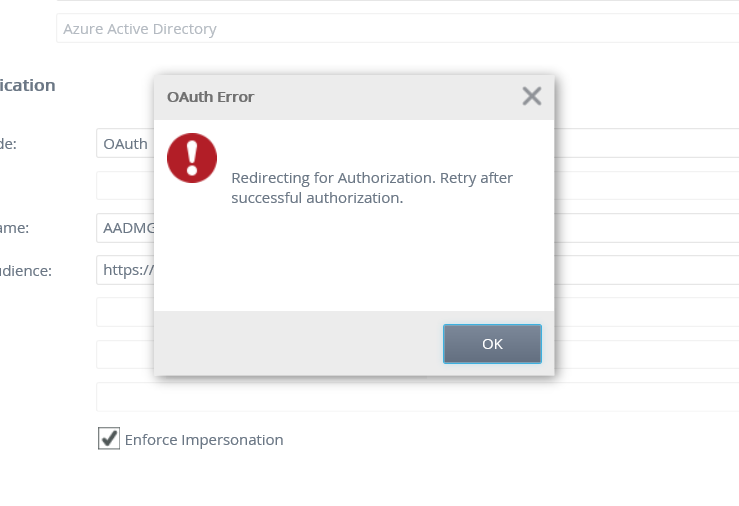
This message appears because you've not consented using the Azure Active Directory Management for K2 app. Click OK to initiate the consent process with Azure Active Directory. You must do this using an Azure Active Directory Tenant Admin account and agree to the permissions requested on your tenancy. - Login with Azure Active Directory Tenant Admin credentials when presented with the Azure Active Directory login screen

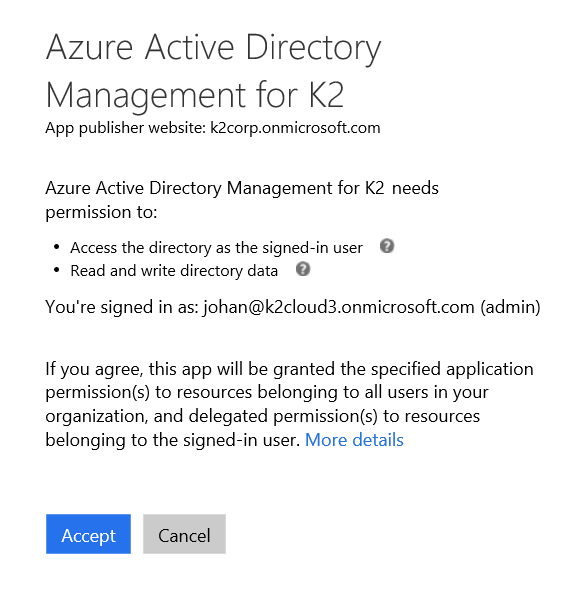
- After logging in, click Accept in order to give the Azure Active Directory Management for K2 app Access the directory as the signed-in user and Read and write directory data permissions in your Azure Active Directory tenancy.
- You then see a confirmation that your authorization is successful. If you do not see this message it means that the account you logged in with does not have sufficient privileges to grant the permissions requested.
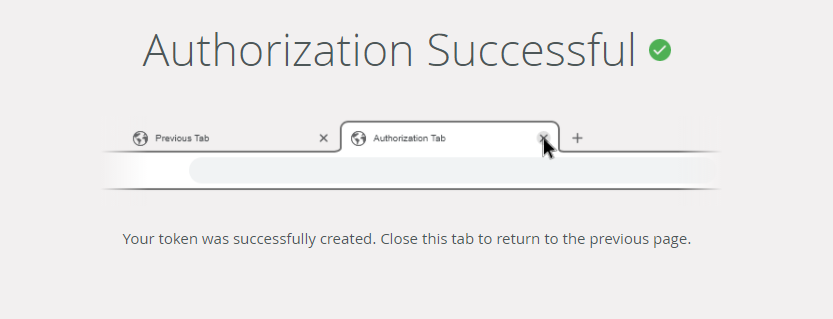
You can close this tab and go back to Management and click OK on the service instance configuration. - You can now use Azure Active Directory SmartObject methods that update or write data to Azure Active Directory.