User Managers
The Management Console in K2 Workspace is superseded by the K2 Management Site and you should use the K2 Management Site to administer your K2 environment, rather than Management Console in K2 Workspace. (In certain cases you may need to use the Management Console in K2 Workspace to perform tasks that are not exposed in the K2 Management Site.)
The User Managers node exposes configuration settings for the Active Directory and SharePoint security providers.
Security Label
Shown in the image below is a security label for K2 displayed in the node directly below the User Managers node. Each user manager (in this example, Active Directory) has one security label per user manager. Multiple domains may however be added per security label; these can be queried equally as the main domain. Any new domain(s) must be added manually and a K2 Server restart may be required as well. New domain(s) are added from the User Managers > K2 Domains node.
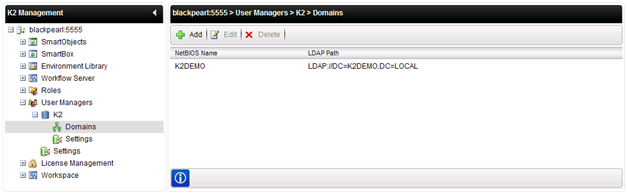
K2 will add a Default Domain based on the domain of the account used to install K2; additional domains must be added, edited and deleted manually, preferably using the K2 Workspace. When a new domain is added, it will not surface in K2 Workspace > User Manager automatically. The domain(s) must be added manually. The K2 blackpearl security label does surface automatically in K2 Workspace. Any additional domains required are added, edited or deleted manually. The default domain cannot be deleted.
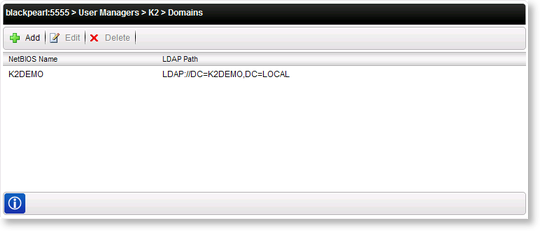
Domains are added manually by a K2 Administrator and are added with reference to the Domain Controller. The NetBIOS Name of the machine must be provided along with the LDAP Path. Once the new Domain has been entered a K2 Server restart is required.

| Field | Description | Example |
|---|---|---|
| NetBIOS Name | This is the NETBIOS name of the domain. You can locate this name by querying the general properties of the domain using the Active Directory Domains and Trusts tool |
DOMAIN |
| LDAP Path | LDAP is a protocol that enables users to locate people, organizations, and other resources in an Internet Directory or intranet Directory. The LDAP Path can be thought of as a connection string to the Directory. |
LDAP://[distinguishedName] The exact value will depend on your AD configuration; check with your AD administrator to determine the LDAP path for the target domain. |
When using multiple domains it is also important to modify the Workspace Web site to authenticate for each domain. To do this, follow these steps:
- Open web.config file corresponding to the Workspace Web site, typically located at C:\Program Files\K2 blackpearl\Workspace\Site.
-
Add a new AD Connection String in the connectionString section. For example:
<add name="ADConnectionString2" connectionString="LDAP://Domain2.com" /> -
In the membership section add a new provider pointing to the newly added connection string. The name of the string needs to be unique and match the other example in Step 2. For example:
<add connectionStringName="ADConnectionString2" connectionProtection="Secure"enablePasswordReset="false" enableSearchMethods="true" requiresQuestionAndAnswer="false"applicationName="/" description="Default AD connection" requiresUniqueEmail="false"clientSearchTimeout="30" serverSearchTimeout="30" attributeMapUsername="sAMAccountName"name="AspNetActiveDirectoryMembershipProvider_Domain2" type="System.Web.Security.ActiveDirectoryMembershipProvider,System.Web,Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" />
When an existing domain is edited, the K2 Server must be restarted.
- Select the domain to edit, click the Edit button.
- When the user dialog opens, apply the changes.
- Click OK.
When an existing domain is edited, the K2 Server must be restarted.
- Select the domain to delete, click the Remove button.
- Confirm the Deletion.
- Click OK.
Group Providers are registered to enable the use of SharePoint Groups. When installing K2, a Group Provider is automatically registered to the Process Portal created by the installer. Should the need exist, Group Providers can be manually registered on other sites by selecting K2 Workspace > User Managers > Group Providers and clicking Add.
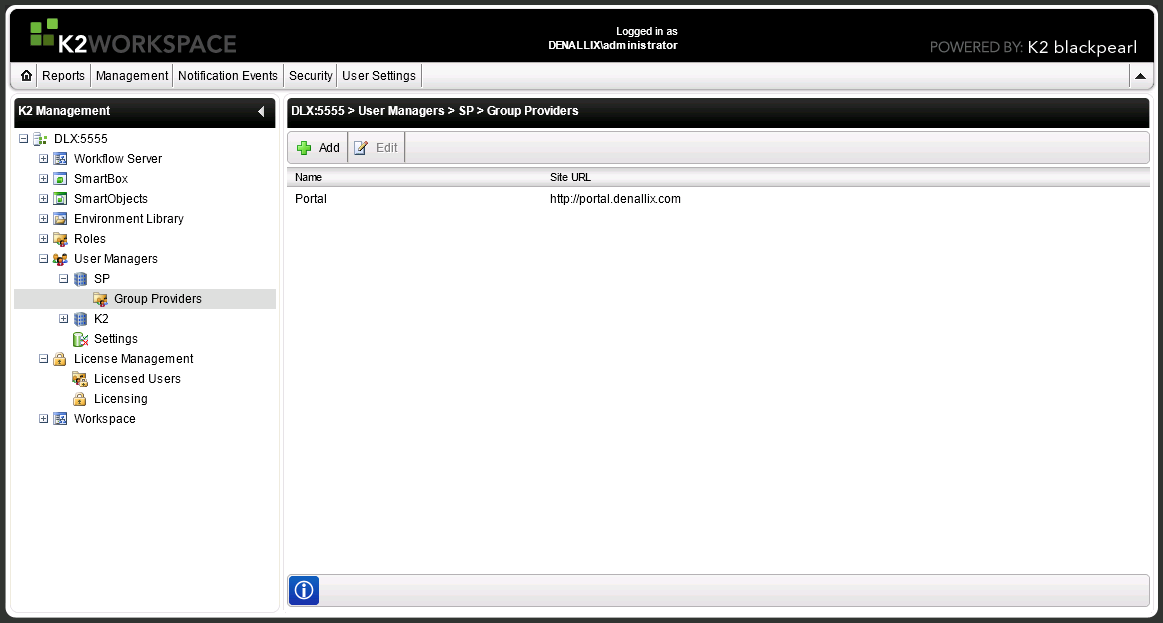
The following steps discuss how to add a Group Provider:
- On the Group Providers screen select the Add button.
- The Add Group Provider screen will be displayed:
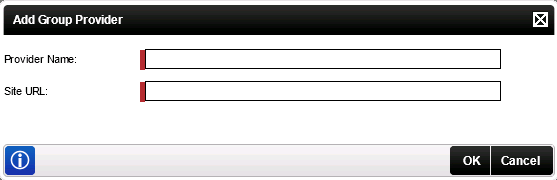
Field Description Provider Name The name of the SharePoint Group Provider. Normally this is created by the K2 installer, but can be manually created as mentioned above. Site URL The URL of the site on which the SharePoint Group Provider is registered. This should always be the root directory. It is not advised to register a Group Provider on a SharePoint sub site as this will have a negative performance impact.
- Click OK.
The following steps discuss how to add a Group Provider:
- On the Group Providers screen select the Edit button.
- The Edit Group Provider screen will be displayed:

Field Description Provider Name The name of the SharePoint Group Provider. Normally this is created by the K2 installer, but can be manually created as mentioned above. Site URL The URL of the site on which the SharePoint Group Provider is registered. This should always be the root directory. - Click OK.
All values below are by default disabled; default cache timeout is set to 0 minutes.
The Settings node implements features that enhance performance from caching users excluding certain operations to improve performance. These options are discussed in greater detail in the relevant topics. The following features provide performance enhancements when referencing the ADUM.
Click on the Settings option, the following K2 Settings screen will open: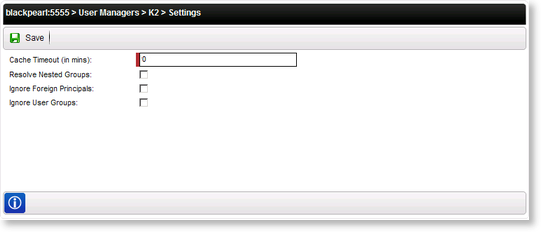
This settings node refers to the ADUM configuration.
When a query is passed to ADUM, it will return all results unless the number of users is limited. Limiting the number of users and groups returned will enhance performance by ensuring that a manageable number of returns reach the screen. Manageable applies to both the number of users a user can use and the system.
| Field | Description |
|---|---|
| Cache Timeout | This setting was deprecated by the introduction of the Identity Service. Please see the Knowledge Base article KB001250: Configuration for Active Directory User Manager cache settings replaced by Identity Service configuration and this blog post for more information. |
| Resolve Nested Groups | Groups within ADUM may contain sub or nested groups with a group. The users within these nested groups will be resolved with this option is enabled. |
| Ignore Foreign Principals | This option enables the Administrator to exclude group members from domains external to the forest. |
| Ignore User Groups | This options enables the Administrator to exclude user groups from being resolved and only the user name will be resolved as part of the current domains. |
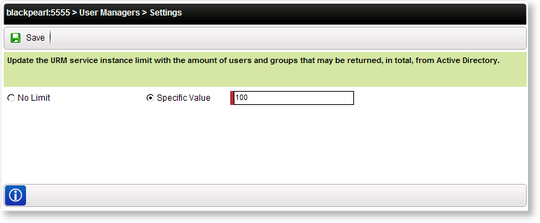
The URM service limit is set to improve system performance. If set to No Limit all users and groups will be returned without paging and may result in reduced system performance.
Click on the Settings option, and configure the URM service instance:
| Field | Description |
|---|---|
| No Limit | All users / groups returned available from the service will be displayed without the benefit of paging. This may result is reduced system performance. |
| Specific value | When the service instance is queried, the specified number of items is returned per page. For systems with a very high volume of users and groups this may result in improved system performance by only returning a specific number of items per page. A value between 0 – 100 or less is recommended. Exceeding this recommended value may negate the value of the feature. |