Enable and Configure the DTC Components
The K2 Host Server makes use of Microsoft’s Distributed Transaction Coordinator (DTC) to ensure data integrity between the K2 Server and the databases.
 |
For the DTC to function correctly, the DTC Components need to be enabled and configured on the K2 Server and SQL server. |
Setting DTC to start automatically
The DTC is a service that coordinates transactions that span multiple resource managers, such as databases, message queues, and file systems. If this service is stopped, these transactions will not occur. If this service is disabled, any services that explicitly depend on it will fail to start.
The DTC is provided as a standard service with the Windows Server 2008 operating system, but does not start up automatically as a service.
To configure the Service to startup automatically, do the following:
 |
Open the Services Manager (Start > All Programs > Administrative Tools > Services) |
 |
Locate the Distributed Transaction Coordinator Service in the list of services |
 |
To configure the service to start automatically, right click on the Distributed Transaction Coordinator Service and select Properties 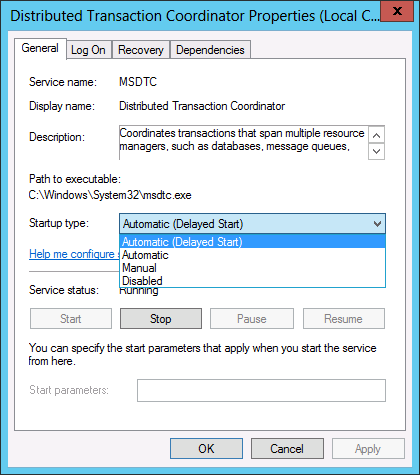 |
 |
If the service is not started, click on the start button. The following dialog appears and displays the system's progress in starting the service. If the action is successful, the dialog disappears and the service's status is set to Started.  |
Configuring DTC
To configure DTC, follow the below steps:
 |
Open Component Services |
 |
From the Console Node expand the following nodes Component Services > Computers > My Computer |
 |
From the My Computer node, locate the new node Distributed Transaction Coordinator |
 |
Expand the node to view the Local DTC |
 |
Right Click on Local DTC and select properties 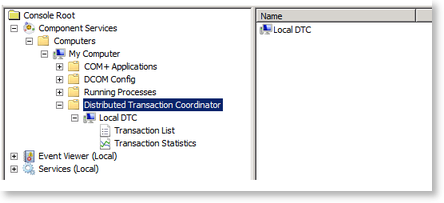 |
 |
On the Local DTC Properties tab, click the Security tab, and configure the properties as follows:
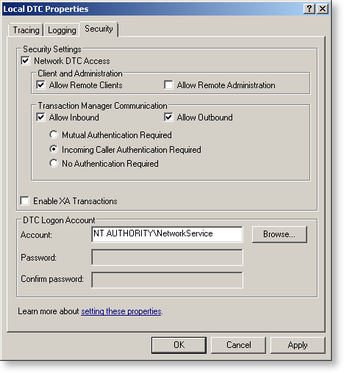 |
 |
Click OK, and in the warning dialog that appears, click Yes |
 |
When the MS DTC service has been restarted, you can click OK on all the dialogs and close Component Management |
 |
This setting is for clustered installations. For non-clustered environments, you can leave the Mutual Authentication Required option selected, as it is the most secure option. The MSDTC transaction mode must be set to either No Authentication Required or Incoming Caller Authentication Required to function correctly on a Windows Server 2008-based failover cluster. Taken from: http://msdn.microsoft.com/en-us/library/dd897479(v=BTS.10).aspx You must use the Incoming Caller Authentication Required transaction mode between Windows Server 2003-based computers in a clustered environment.
Even for the Incoming Caller Authentication Required setting to work in the cluster environment you need to have the environment configured correctly for the Kerberos authentication. And again this might break if there is a Windows 2000 server coming into picture as it would only work if you have set No Authentication Required throughout on all the Windows 2003 server machines. Based on the explanation above, we recommend having “No Authentication Required” setting on the cluster and the other standalone server interacting with the cluster to avoid running into any compatibility issues with older operating systems and authentication failures. Taken from: http://support.microsoft.com/?id=899191 |
DTC Configuration when a Firewall is Active
The following configuration is performed using the dcomcnfg.exe application located in the Windows\System32 folder.
| Firewall Configuration | |
|---|---|
|
Configure firewall to allow MSDTC access with the following command: netsh advfirewall firewall add rule name="MSDTC" dir=in action=allow program="%windir%\system32\msdtc.exe" enable=yes Configure firewall to allow SQL Server access with the following command: netsh advfirewall firewall add rule name="MSSQLSERVER" dir=in action=allow program="C:\Program Files\Microsoft SQL Server\MSSQL.1\MSSQL\Binn\Sqlservr.exe" enable=yes These firewall settings must be activated on SQL server in order for MSDTC to work:
For information please see the Knowledge base article KB001318 - K2 and Firewalls And this MSDN blog: http://blogs.msdn.com/b/chrisforster/archive/2009/05/29/windows-2008-sql-server-cluster-with-msdtc-when-using-windows-firewall-with-advanced-security.aspx |
 |
While infrastructure changes are required by K2, each environment is different and has its peculiarities which must be taken into account. Modifying the infrastructure could have unforeseen results if the changes are not appropriately understood or managed. Given the broad spectrum of underlying infrastructure utilized, it is recommended that a panel or committee with appropriate skill in each area concerned be assembled to outline the underlying infrastructure changes and gauge the impact of the required changes. |
