K2 and Claims - FAQ
What claims are mapped from SharePoint to K2?
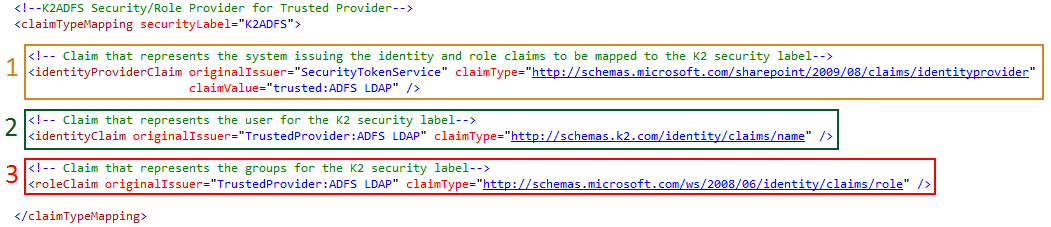
Legend
1 Identity Provider
2 Identity
3 Role
 |
K2 requires the claimType for the identityClaim to match the claim mapping configured in SharePoint as the Identifier Claim. The K2 Server Configuration section provides automatic and manual approaches that aid in configuring the appropriate identity claim type mapping for K2. |
For more information, see Claim Type Mappings.
Can K2 work without access to the source identity store?
K2 needs to map to the same identity store as the source of the claim to fully implement user and group browsing and user property (e.g., email or manager) lookups. However, user and group browsing and property lookups are not requirements for K2 to function. Strings representing the K2 label and the FQN can be used throughout K2 for rights and work assignment, and properties can be stored and retrieved from other places, such as SharePoint User Profile DB.
K2 provides support for AD, LDAP and SQL source identity stores. A custom user manager can be created to support other identity stores.
Does K2 need to communicate with source identity store?
Yes. K2 does not retain claim set data and only uses the identity claim at runtime. K2 needs access to the identity store directly to retrieve user details, similar to the SharePoint User Profile store.
Can K2 support multiple Claims Authentication Types (aka, providers) for the zone you wish to work with?
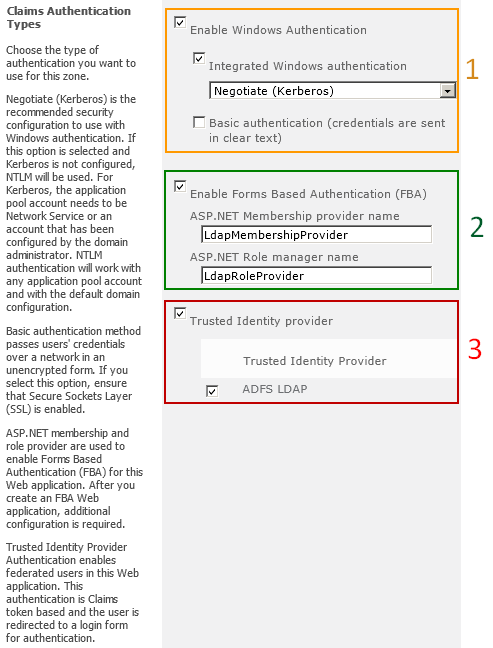
Yes. K2 requires #1 (Windows Authentication) and can support any combination of #2 (Forms) and/or #3 (Trusted).
For more information, see Supported Configuration.
Can K2 for SharePoint components work on a SharePoint web application zone that does not have Windows Authentication enabled?
No. The K2 service account and any K2 Studio or Visual Studio based designer accounts require access to the claims-based zone via Windows Authentication.
Can K2 use one zone configured for Windows Authentication for designer rights and another zone without Windows Authentication for runtime?
No. K2 does not support the use of multiple zones or alternate access mappings. K2 must utilize the same zone (aka, URL) for both design time and runtime integration.
Can K2 leverage the SharePoint User Profile database?
Yes. K2 can utilize the data in the user profile database to retrieve attributes for claims-based users via custom code.
Can K2 work with federated AD FS (e.g., multiple domains)?
No. K2 requires a one-to-one mapping from an identity store to a K2 user manager. Therefore, a single AD FS endpoint that has federated multiple identity stores cannot be configured. K2 supports the development of custom user managers which can manage federated identity stores.
