SharePoint Service Account
In a distributed environment where components are installed on more than one server or if host headers are used, Kerberos security must be configured. One of the components of Kerberos is the Service Principal Name (SPN). Whenever user credentials must be passed from one system to another, the system that is attempting to pass the credentials must be trusted for delegation. For this step to take place successfully, Kerberos delegation must be configured.
 |
Configuring SPNs is an advanced task and should only be performed by an appropriately trained professional. The steps and configurations given in this help file are to be used as a guide - your system may require additional configuration due to different hardware and software compatibilities. |
Set SPNs
In order for the K2 Worklist Web Part and K2 Designer for SharePoint to function properly from another machine, you need to set the SPNs for the SharePoint Service Account.
The following placeholders are used in the commands:
- domain\SharePoint Service Account - The SharePoint Service Account that runs the SharePoint application pool
- MachineName - The name of the computer on which SharePoint Service is running
- MachineName.FQDN - The fully qualified domain name of the computer on which the SharePoint Service is running
 |
Be sure to set all the SPNs as listed below. Also, the service account is required so be sure to specify the account properly. |
 |
If you have SharePoint running on a cluster, be sure to use the name of the cluster and the fully qualified cluster name instead of a single node's machine name. |
 |
If you are using Host Headers to access your SharePoint Service, use the HostHeader value instead of the MachineName in the below commands. An SPN for each Host Header will need to be created. |
Open a command prompt on a server that has the Windows Support Tools installed, and execute the following commands:
- setspn -A HTTP/MachineName domain\SharePoint Service Account
- setspn -A HTTP/MachineName.FQDN domain\SharePoint Service Account
After the commands have successfully executed, you can verify the SPNs were set by executing the following command:
- setspn -L domain\SharePoint Service Account
Configure for Delegation
After the SPN has been set, a new Delegation tab is available in Active Directory Users and Computers for the Service Account. By default, the option selected is the Do not trust this user for delegation. You need to set the account to be trusted for delegation, by following the below steps:
 |
If you are running your Active Directory domain in Windows 2000 native mode, the Delegation tab will not be present. Instead, on the Account tab, you will see a Trust this user for delegation check box. |
 |
Open Active Directory Users and Computers (Start > All Programs > Administrative Tools > Active Directory Users and Computers) |
 |
Find the domain\SharePoint Service Account and view its properties |
 |
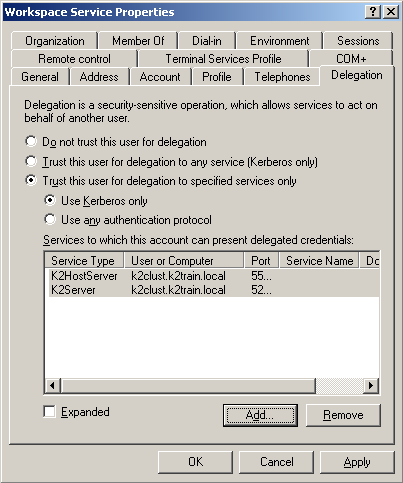
On the Delegation tab, select the Trust this user for delegation to specified services only option |
 |
Select the Use Kerberos only option, and click on Add |
 |
Click on Users or Computers and select the domain\K2 Service Account you created as the K2 Server Service Account |
 |
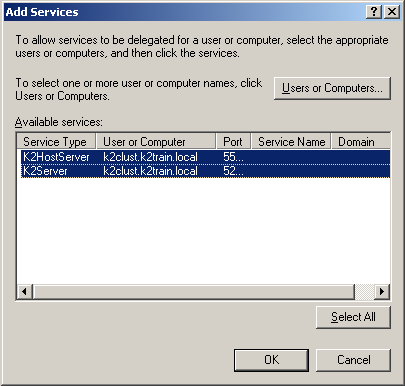
In the Available Services section, select both the K2HostServer and K2Server items listed: |
 |
Click OK. Your properties should resemble the following: |
 |
Click Add again |
 |
Click on Users or Computers and select the domain\K2 Workspace Account you created as the K2 RuntimeServices Account |
 |
In the Available Services section, select the HTTP item listed |
 |
Click OK. This will allow the SharePoint Service Account to delegate to the K2 Workspace Account. |
 |
While infrastructure changes are required by K2, each environment is different and has its peculiarities which must be taken into account. Modifying the infrastructure could have unforeseen results if the changes are not appropriately understood or managed. Given the broad spectrum of underlying infrastructure utilized, it is recommended that a panel or committee with appropriate skill in each area concerned be assembled to outline the underlying infrastructure changes and gauge the impact of the required changes. |