Exchange Wizard - Runtime Operational Rights
- An Exchange administrator account should be created and given Exchange Organization administrator rights.
- When the Create/Disable mailbox action is selected, the wizard should be configured to Run As the Exchange administrator account.
- An Exchange service account should be created and given Exchange impersonation rights.
- When a Meeting Request or a Send Task action is selected in the Exchange Event Wizard, the wizard should be configured to Run As the Exchange service account.
- Using the Exchange Web Service requires the K2 server machine to trust the EWS certificate and its signing Certificate Authority. This is required for the following operations:
- Exchange Calendar SmartObject (used by Send Meeting Request)
- Exchange Task SmartObject (used by Send Task)
- Exchange Meeting SmartObject (for using the Get Meeting Suggestions and Get Specific Time methods)
Rights Specific to Microsoft Exchange Server 2010
K2 Service Account
This account should have Recipient Management rights for Exchange to be able to create and disable mailboxes and browse Exchange servers and mailbox databases.
Also give the account Execute rights on the Microsoft.PowerShell configuration, by running the following command in the Exchange Management Shell:
Set-PSSessionConfiguration Microsoft.PowerShell –ShowSecurityDescrtiptorUI
Exchange Organization and View-Only Administrator Rights
Configuring Exchange Organization and View-Only Administrator rights can be done through the Exchange Management Console:
- Open the Exchange Management Console
- Select the user account that will be configured with the new rights
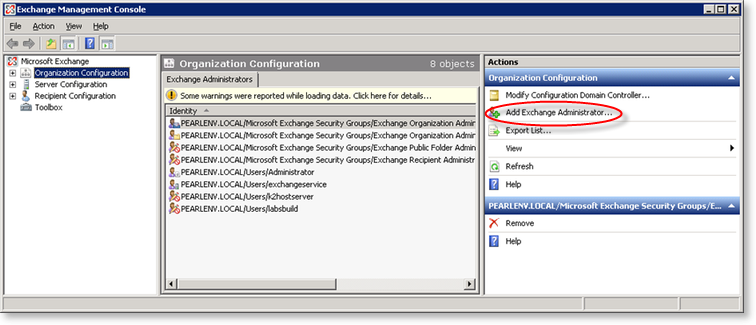
- Then click on the Add Exchange Administrator link in the right hand column and select the required rights.
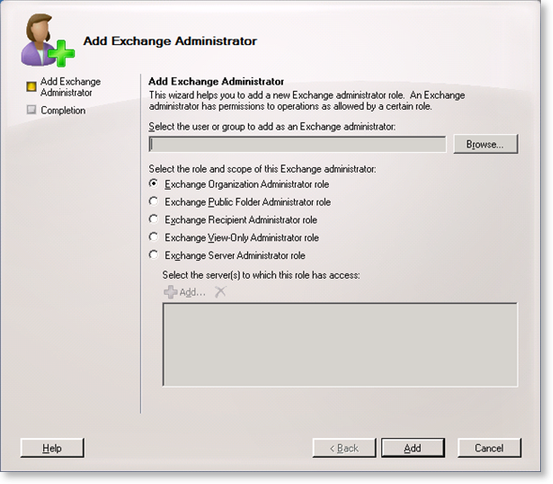
- Click on the Add button to complete the account configuration
Exchange Impersonation Rights
Giving Exchange impersonation rights for an account requires the account to NOT be part of the Exchange Organization Administrator group.
The rights are given to a user for a specific server.
 |
The user running the Exchange Management Shell to execute these commands should be an Exchange Organization Administrator. |
The following commands should be run in the Exchange Management Shell, replacing <ExchangeServer> with the Exchange server’s name where the Exchange web service is running and replacing <ExServiceAccount> with the name of the Exchange service account which the rights should be given to:
Add-ADPermission -Identity (get-exchangeserver -identity <ExchangeServer>).DistinguishedName -User (Get-User -Identity <ExServiceAccount> | select-object).identity -AccessRights GenericAll -InheritanceType Descendents
Add-ADPermission -Identity (get-exchangeserver -identity <ExchangeServer>).DistinguishedName -User (Get-User -Identity <ExServiceAccount> | select-object).identity -ExtendedRight ms-Exch-EPI-Impersonation
Add-ADPermission -Identity (get-exchangeserver -identity <ExchangeServer>).DistinguishedName -User (Get-User -Identity <ExServiceAccount> | select-object).identity -ExtendedRight ms-Exch-EPI-May-Impersonate
Add-ADPermission -Identity (get-exchangeserver -identity <ExchangeServer>).DistinguishedName -User (Get-User -Identity <ExServiceAccount> | select-object).identity -ExtendedRights Send-As
Add-ADPermission -Identity (get-exchangeserver -identity <ExchangeServer>).DistinguishedName -User (Get-User -Identity <ExServiceAccount> | select-object).identity -ExtendedRights Receive-As
- Select the Exchange Management Shell from the Start menu
- This will open the console window, within which the above commands can be executed