Exchange Wizard - Design-time Operational Rights
The K2 Service Account needs Exchange View-Only Administrator rights. These rights are needed because the K2 Studio Object Browser uses the K2 Service account to view the Storage Groups and Mailbox Databases on an Exchange server.
In order for these rights to take effect, the K2 Server needs to be restarted.
Rights Specific to Microsoft Exchange 2010
Installation Account
This account should have View-Only rights for Exchange to be able to browse Exchange servers and mailbox databases.
Also give the account Execute rights on the Microsoft.PowerShell configuration, by running the following command in the Exchange Management Shell:
Set-PSSessionConfiguration Microsoft.PowerShell –ShowSecurityDescrtiptorUI
K2 Service Account
This account should have Recipient Management rights for Exchange to be able to create and disable mailboxes and browse Exchange servers and mailbox databases.
Also give the account Execute rights on the Microsoft.PowerShell configuration, by running the following command in the Exchange Management Shell:
Set-PSSessionConfiguration Microsoft.PowerShell –ShowSecurityDescrtiptorUI
Impersonation Account
This account should be assigned the Application Impersonation role to be able to impersonate users for sending meeting requests and creating tasks.
Run the following command in the Exchange Command Shell to give impersonation rights:
new-ManagementRoleAssignment -Name: _suImpersonateRoleAsg -Role: ApplicationImpersonation -User: “impersonation account name”
Give this account “Log on as batch job” rights on the K2 Server machine to be able to run Exchange Events as this account.
Configuring WinRM
The following commands should be run through the Exchange Management Shell on the Exchange server machine:
Enable-PSRemoting
Set-Item wsman:\localhost\client\trustedhosts “k2server machine fan”
Configure IIS on the Exchange server machine:
By default, WinRM uses http and connects through the Default Web Site on port 80.
Add bindings to http port 80, with no host name and All Unassigned if they don’t exist.
\PowerShell should not have SSL enabled.
\PowerShell should have only anonymous access enabled.
Troubleshooting
To resolve possible connection issues with WinRM, try the following:
On the Exchange server, edit group policy and under Computer Configuration\Administrative Templates\Windows Components\Windows Remote Management (WinRM)\WinRM Service, set IPv4 & IPv6 filters = *
IPv6 should be enabled
On the K2 server machine, run the following cmd let in PowerShell
Set-ExecutionPolicy Unrestricted
PowerShell can’t connect to host headers, so the Exchange certificate should be issued to the Exchange server machine name and the Exchange service instances should point to the machine name as well
Exchange Organization and View-Only Administrator Rights
Configuring Exchange Organization and View-Only Administrator rights can be done through the Exchange Management Console:
- Open the Exchange Management Console
- Select the user account that will be configured with the new rights
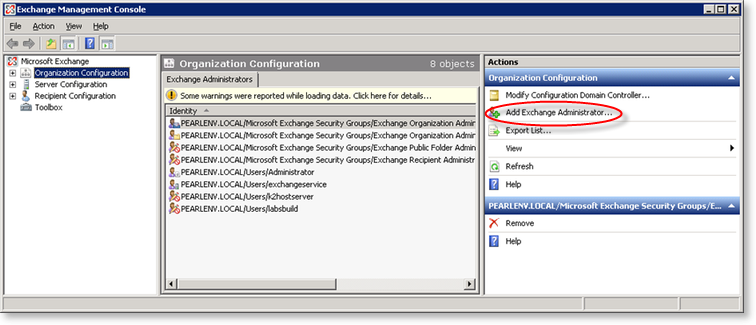
- Then click on the Add Exchange Administrator link in the right hand column and select the required rights.
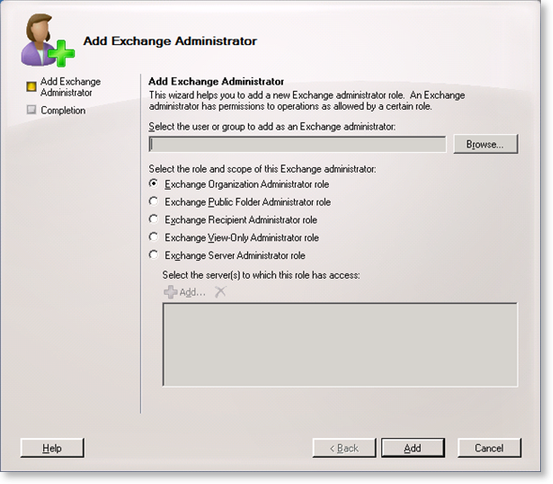
- Click on the Add button to complete the account configuration
