Supported Configurations
K2 supports integration with SharePoint 2010 web applications in either classic mode authentication or claims-based authentication when configured according to the details in this section.
Bootstrap Tokens
SharePoint 2010 claims-based authentication web sites by default are configured to allow the saving of the bootstrap tokens in the IClaimsIdentity and Sessions after token validation. K2 requires the bootstrap token to be present for proper validation of original claim issuers. The <service saveBootstrapTokens="true"> setting can be found in the <microsoft.identityModel> section of the web.config for the claims-based web site and must be set to true.
SharePoint 2010 Claims Authentication Types
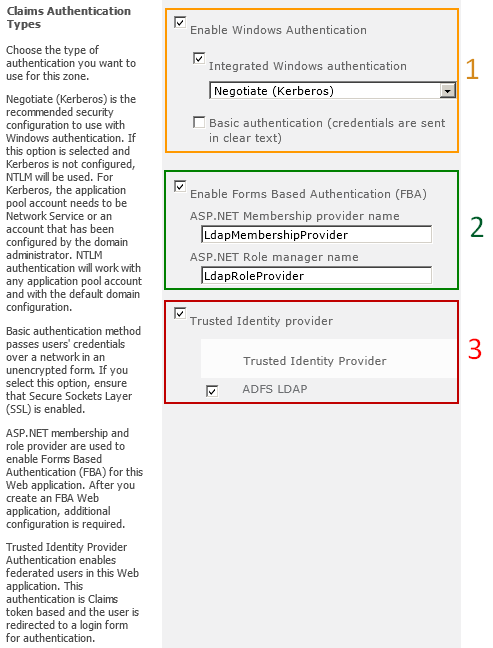
1 Windows Authentication (Windows)
2 Forms Based Authentication (FBA)
3 Trusted Identity Provider (Trusted)
Windows (Required)
Negotiate (Kerberos) is the recommended security configuration to use with Windows authentication. If this option is selected and Kerberos is not configured, NTLM will be used. For Kerberos, the application pool account needs to be Network Service or an account that has been configured by the domain administrator. NTLM authentication will work with any application pool account and with the default domain configuration.
Basic authentication is a sub-option of Windows authentication and is used as a fallback if Integrated Windows authentication is selected and not available.
Basic authentication method passes user credentials over a network in an unencrypted form. If you select this option, ensure that Secure Sockets Layer (SSL) is enabled.
 |
Important: K2 requires that Windows authentication is configured for Integrated Windows authentication using either NTLM or Negotiate (Kerberos) on all zones of claims enabled web applications that have K2 for SharePoint integration components activated. |
Forms
ASP.NET membership and role provider are used to enable Forms Based Authentication (FBA) for a Web application. After you create an FBA Web application, additional configuration is required. For more information, see Configure forms-based authentication for a claims-based Web application (SharePoint Server 2010): http://technet.microsoft.com/en-us/library/ee806890.aspx
K2 has tested Forms Based Authentication configured for Microsoft’s LDAP Providers.
- Membership Provider: Microsoft.Office.Server.Security.LdapMembershipProvider
- Role Provider: Microsoft.Office.Server.Security.LdapRoleProvider
 |
Disclaimer: K2 is expected to be configurable for any Forms Authentication Providers that have been properly configured and proven to work with SharePoint 2010. However, only Microsoft’s LDAP Membership and Role Providers have been tested. |
Trusted
Trusted Identity Provider Authentication enables federated users for a Web application. This authentication is Claims token based and the user is redirected to a login form for authentication.
K2 has tested Trusted Identity Provider configured for AD FS 2.0 with Active Directory and LDAP attribute stores. For more information, see Configuring SharePoint 2010 and ADFS v2 End to End: http://blogs.technet.com/b/speschka/archive/2010/07/30/configuring-sharepoint-2010-and-adfs-v2-end-to-end.aspx
The claim rules tested vary based on the attribute store used.
Active Directory
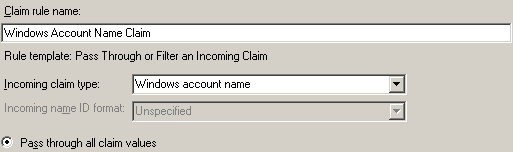
Rule: Windows Claim
- Claim rule template: Pass Through or Filter an Incoming Claim
- Claim rule name: Windows Account Name Claim
- Incoming claim Type: Windows account name
- Pass through all claim values: Selected
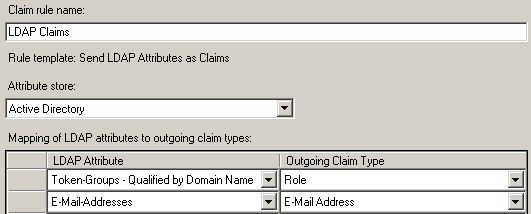
Rule: LDAP Claims
- Claim rule template: Send LDAP Attributes as Claims
- Claim rule name: LDAP Claims
- Attribute Store: Active Directory
- Mapping of LDAP attributes to outgoing claim types
| LDAP Attribute | Outgoing Claim Type |
|---|---|
| Token-Groups – Qualified by Domain Name |
Role |
| E-Mail-Addresses | E-Mail-Addresses |
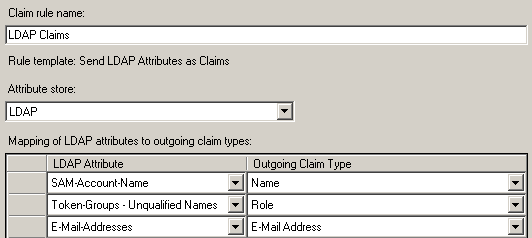
LDAP
Rule: LDAP Claims
- Claim rule template: Send LDAP Attributes as Claims
- Attribute Store: LDAP
- Mapping of LDAP attributes to outgoing claim types
| LDAP Attribute | Outgoing Claim Type |
|---|---|
| SAM-Account-Name | Name |
| Token-Groups- Unqualified Names | Role |
| E-Mail-Addresses | E-Mail-Addresses |
 |
Disclaimer: K2 is expected to be configurable for any Trusted Identity Providers that have been properly configured and proven to work with SharePoint 2010. However, only Microsoft’s AD FS 2.0 has been tested. |
SharePoint Multi-Authentication
SharePoint supports implementing more than one claims authentication type on a single web application zone. Microsoft recommends when using claims authentication and implementing more than one type of authentication, that you implement multiple types of authentication on the default zone. This results in the same URL for all users. For more information, see Planning Zones for Web applications: http://technet.microsoft.com/en-us/library/cc262350.aspx#section6.
The Microsoft SharePoint Search crawl component requires that Windows authentication is configured for Integrated Windows authentication using either NTLM or Negotiate (Kerberos) to access the content of the Web application.
K2 also requires that Windows authentication is configured for Integrated Windows authentication using either NTLM or Negotiate (Kerberos) on all zones of claims enabled web applications that have K2 for SharePoint integration components activated.
The SharePoint crawl component and K2 server utilize the Protocol Discovery Request defined in the Office Forms Based Authentication Protocol Specification to interact with claims based Web applications from Windows based service accounts. The specification provides for the use of request headers to enable authentication through services without login forms.
For more information, see the Protocol Discovery Requests topic in the Office Forms Based Authentication Protocol Specification: http://msdn.microsoft.com/en-us/library/dd773463(v=office.12).aspx.
Multi-Authentication Combinations
Only the following SharePoint 2010 multi-authentication combinations are supported by K2.
Classic Mode
- Windows
Claims Mode
- Windows
- Windows + FBA
- Windows + Trusted
- Windows + FBA + Trusted
