Single Sign On
 |
The Active Directory credentials that are cached are stored securely in the K2 Databases using an encrypted password |
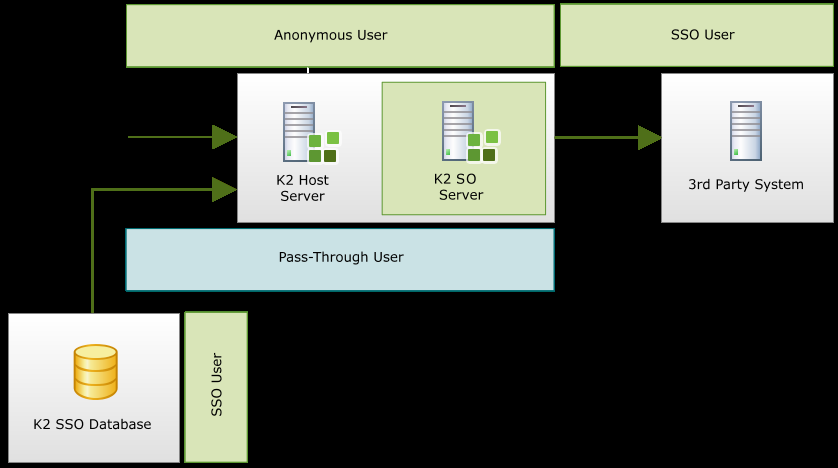
Single Sign on is a feature that has been primarily used in conjunction with 3rd party systems where a secondary set of credentials were cached against a security label and this would create a single sign in identity. This feature was originally made available so that K2 blackpearl was capable of authenticating a client user for systems for example K2 Connect for SAP and SalesForce.
 |
Single Sign On will only come into affect if first K2 Pass-Through were called. Therefore, if the K2 Server using K2 Pass-Through does not receive a pass through call or does not determine that a Pass-Through requirement exists then SSO would not be called in affect either. |
Single Sign On has been enhanced to work in conjunction with K2 Pass-Through Authentication so that Active Directory credentials can also be cached in a similar way. This feature enhancement enables the system to check for cached credentials when calling an external system for the current K2 Pass-Through Authentication user. All Active Directory passwords are stored securely within the K2 Databases using K2 symmetric key. This method is therefore by no means a security threat or risk.
Once credentials have been cached and they are available K2 can then logon and impersonate the user when calling the 3rd party system. This method is equivalent to if Kerberos were used to do the same.
There are a number of steps that K2 Host Server follows when utilizing Single Sign On with K2 Pass-Through Authentication: