Creating SmartObjects for LOB Systems
Creating a SmartObject that exposes some back-end provider is best approached with a sequence of six steps.
1. Determine the Service Type
The first step in creating a SmartObject based off of a Line of Business system is to determine the appropriate service type for the system that you want to connect to (for example, a SQL database, an Active Directory domain or a Web Service). K2 comes with a set of installed Service Types as standard, and it is possible for developers to write custom Service Brokers so that you can interact with other types of systems as well. The K2 Community site also has a dedicated section especially for community-provided service brokers. you can explore the group at following URL http://community.k2.com/t5/K2-blackpearl/bg-p/K2_bm_blackpearl.
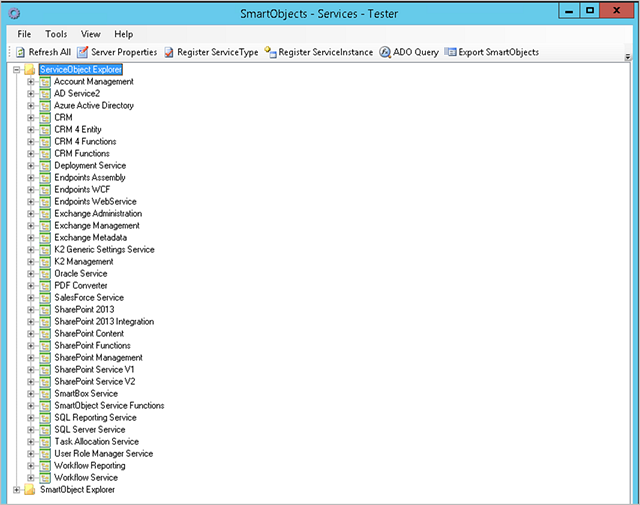
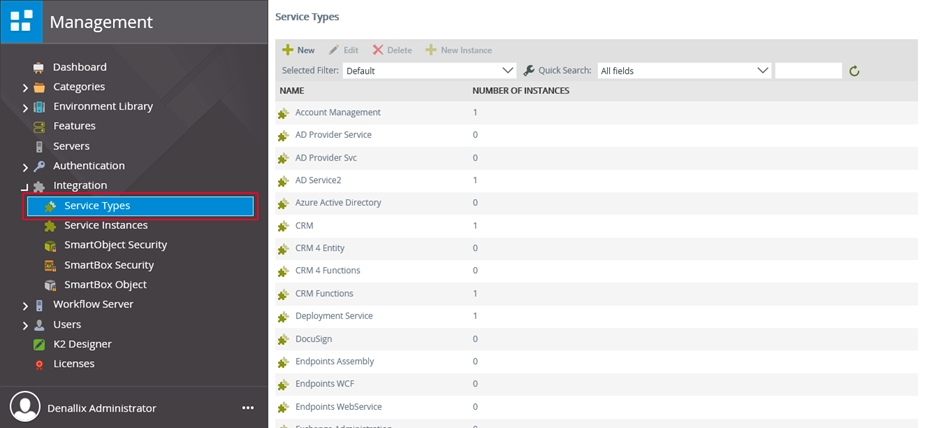
You can use tools like the SmartObject Service Tester utility (located by default at [Program Files (x86)]\K2 blackpearl\Bin\SmartObject Service Tester.exe) or the K2 Management Site to browse the available Service Types that have been registered in your K2 environment, and to register new custom Service Types.
Exploring the available Service Types with the SmartObject tester utility
Exploring the available Service Types with K2 Management Site
2. Locate the Data
Investigate the data source (for example, the SQL database or the web service) to understand where the data is that you want to expose and how the data is accessed. Understand the properties and methods that are available in the data source, and how you want to define logical business objects that expose those properties and methods.
3. Determine Security considerations
Next, determine the security requirements for the data source. The service instance that exposes the data source can be configured with different authentication options (refer to the topic Service Instance Authentication Modes for more details on the available modes), and the authentication mode selected will depend on several factors. These factors include the authentication mechanism supported by the data source, whether or not the data source is secured and whether data is secured according to user credentials, whether it is possible to pass user credentials over machine or network boundaries and more.
Consider the organization’s security policy, network infrastructure and the authorization and authentication mechanisms of the provider to select the appropriate authentication mechanism to use when K2 interacts with the provider. In addition, you should determine what the security considerations for the target system are, such as whether all operations must be audited in the context of the currently-connected user, or if it is OK to use static credentials.
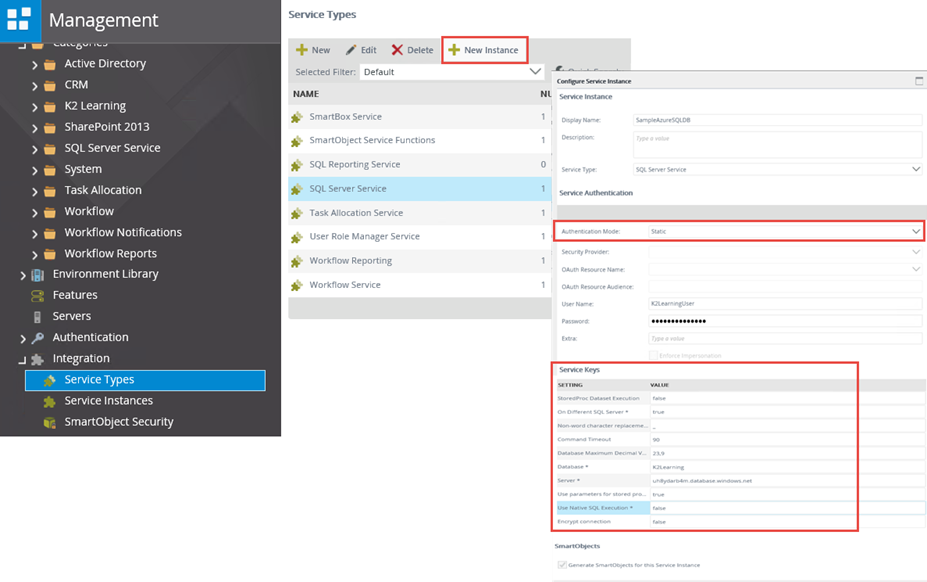
4. Register a Service Instance
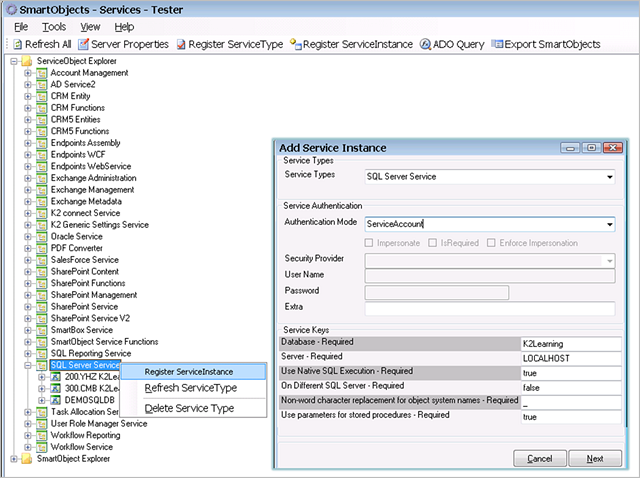
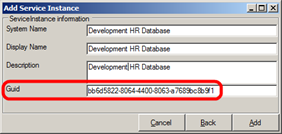
If there is not already an existing instance for the service broker configured for the provider you want to use, use the K2 SmartObject Service Tester utility, the K2 Management Site, K2 Workspace. K2 Site Settings in SharePoint to register a new instance of the broker that will be used to access the provider. Depending on the broker, you will need to provide different configuration settings to set up the Service Instance.
As part of the service instance registration process, K2 will discover the underlying provider and automatically generate Service Objects for the provider. Depending on the size of the provider store, this process may take a few minutes to complete.
Registering a Service Instance with the SmartObject tester utility
Registering a Service Instance with the K2 Management Site
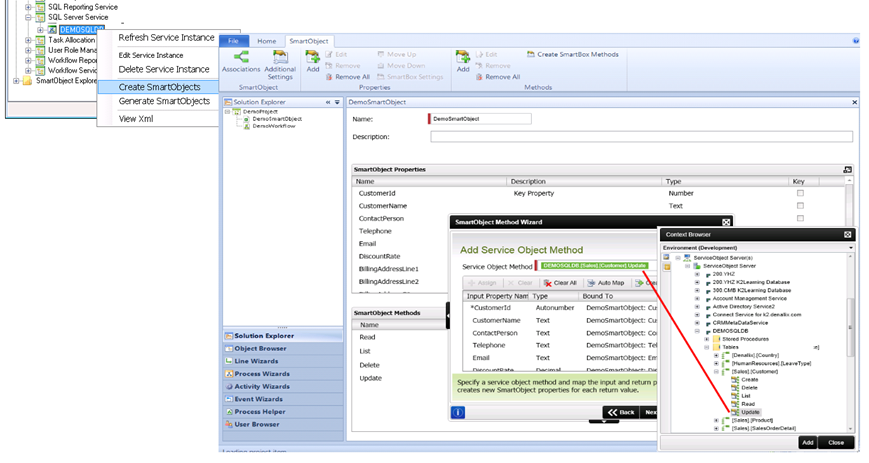
5. Create SmartObjects
Once the Service Objects have been discovered by K2, you can begin creating SmartObjects for the provider. You may use utilities like the K2 SmartObject Service Tester utility or K2 Settings in SharePoint to generate and deploy SmartObjects for specific Service Instances, or use K2 design tools like K2 Studio, K2 for Visual Studio or K2 Designer to create SmartObjects manually.
Generating SmartObjects with the Service Tester utility, or creating SmartObjects in K2 Studio
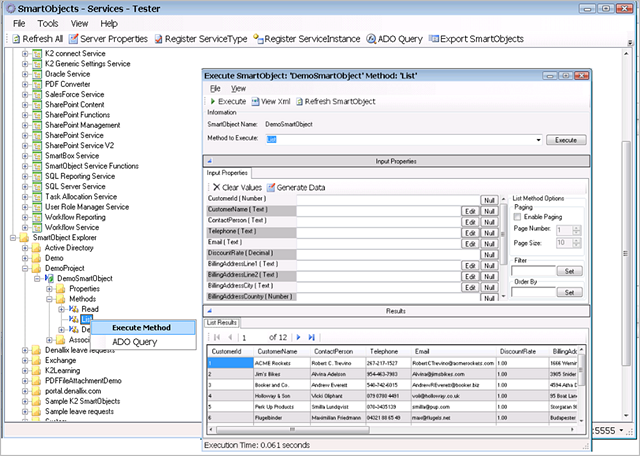
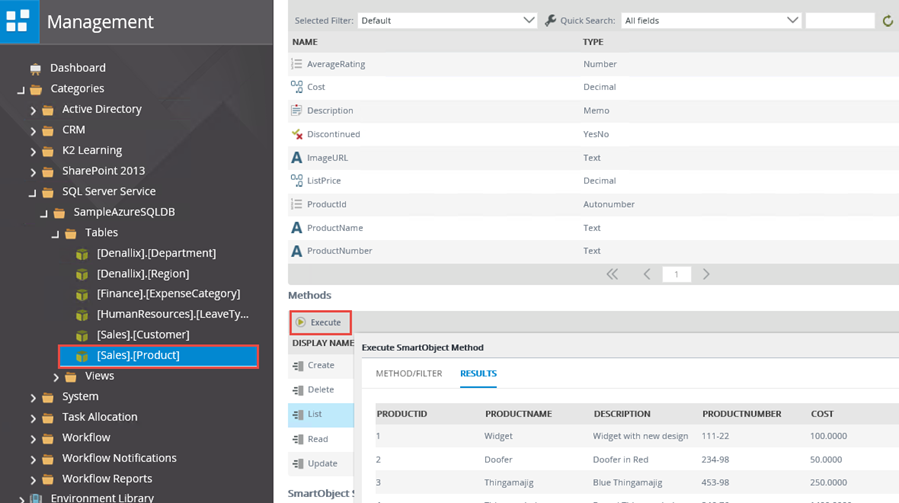
6. Test the SmartObjects
Once the SmartObject has been deployed, use the SmartObject Service Tester utility or the K2 Management Site to test the SmartObject, or create a quick workflow, SmartForm or report to test the SmartObject and that it behaves as expected.
Testing a SmartObject with the SmartObject Service tester utility
Testing a SmartObject with the K2 Management Site
Summary
- Determine which Service Type to use for the target technology.
- Locate the data in the data source.
- Determine the security considerations and the Service Instance Authentication mode.
- Register and configure a Service Instance that points to the target data source.
- Use the SmartObject tools to generate, use the K2 design tools like K2 Studio/K2 Designer to design and deploy the SmartObject.
- Test the SmartObject using tools like the SmartObject Service Tester/K2 Management site, or generate a SmartForm from the SmartObject.